Blog.
- #auth0 alternative
- #Authentication
- #custom login
- #API
- #keycloak vs. zitadel
- #auth0 vs. zitadel
- #PHP SDK
- #Ruby SDK
- #Build vs. Buy
- #typescript-login
- #GRPC
- #Python SDK
- #terraform
- #Authorization
- #zitadel
- #announcement
- #Beyond Authentication
- #actions
- #token-management
- #SDK
- #oidc
- #Zitadel SDKs
- #iam
- #multi-tenancy
- #iaac
- #zitadel_cloud
- #community
- #about_us
- #Service Ping
- #Java SDK
- #engineering
- #keycloak alternative
- #how-to
- #features
- #imo
- #open_source
- #pentest
- #security
- #self_hosting
- #case_studies
- #alternative
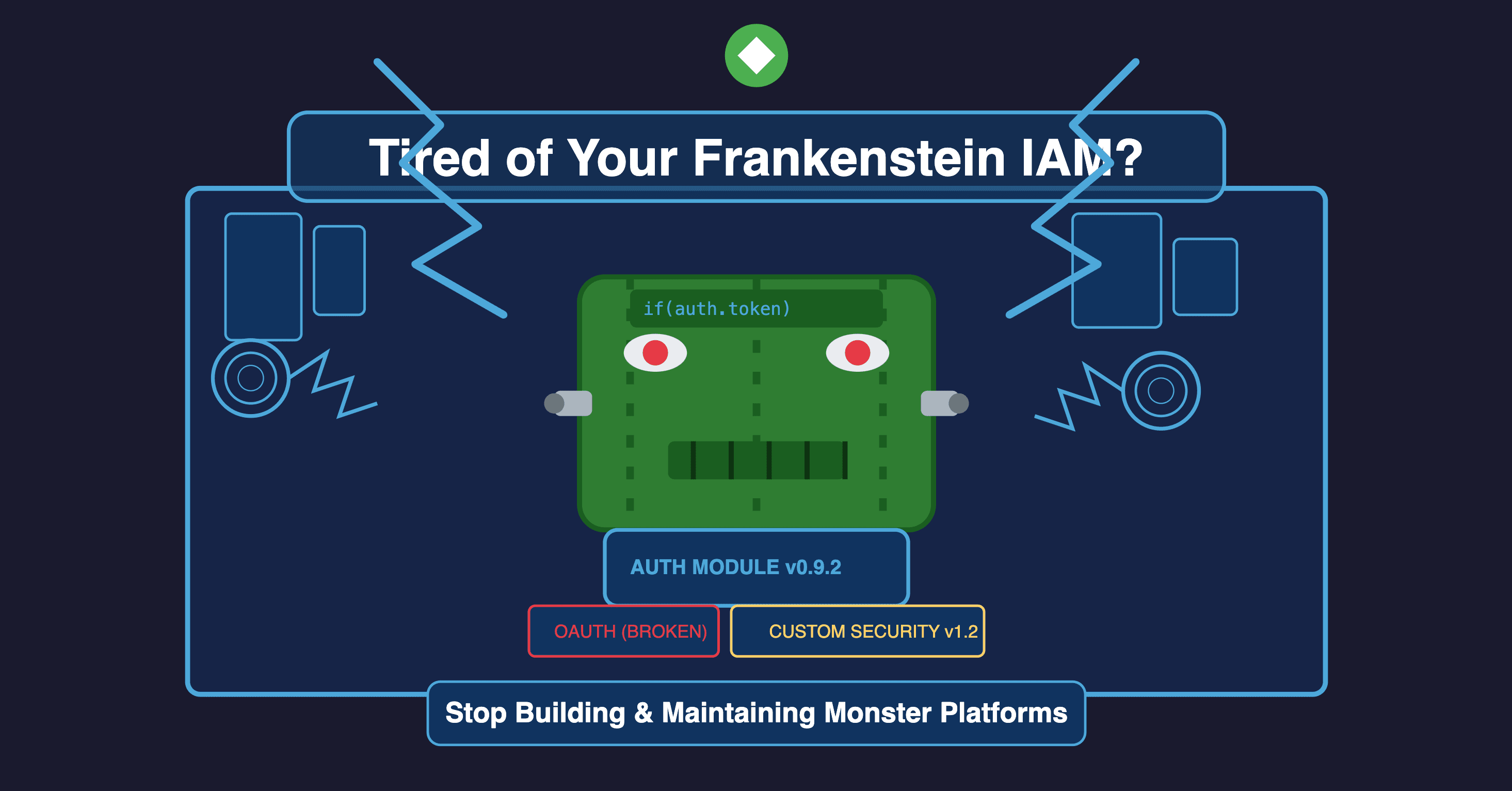
Stop Building and Maintaining Frankenstein IAM Platforms
The Zitadel Identity and Access Management (IAM) platform offers a turnkey enterprise-grade platform for cloud-native organizations looking to move away from a custom-built IAM platform with modules that are expensive to maintain.
• 12 min
Zitadel vs. Keycloak: What makes Zitadel the best Keycloak alternative
Understanding why Zitadel best fits your organization in comparison to Keycloak will ensure a streamlined deployment and authentication experience for your organization and customers.
• 9 min
Thank you for 10,000 Stars!
Zitadel Identity and Access Management (IAM) platform celebrates the milestone for the open source project reaching 10,000 github stars.
• 6 min
Strengthening Our Open Source Foundation: Moving to AGPL 3.0
Zitadel aims to build a sustainable ecosystem and business as it continues to stay committed to open with a license change from Apache 2.0 to AGPL 3.0.
• 6 min
Zitadel v3: AGPL License, Streamlined Releases, and Platform Updates
As Zitadel continues to evolve, the team announced several significant changes coming with the release of Zitadel v3, including a licensing update, streamlined releases, and standardization on PostgreSQL
• 6 min
Zitadel vs Auth0: The Definitive Comparison for Enterprise Identity Infrastructure
Understanding why Zitadel is the best Auth0 (by Okta) alternative and how it best fits your organization in comparison to Auth0 will ensure a streamlined deployment and authentication experience for your organization and customers.
• 9 min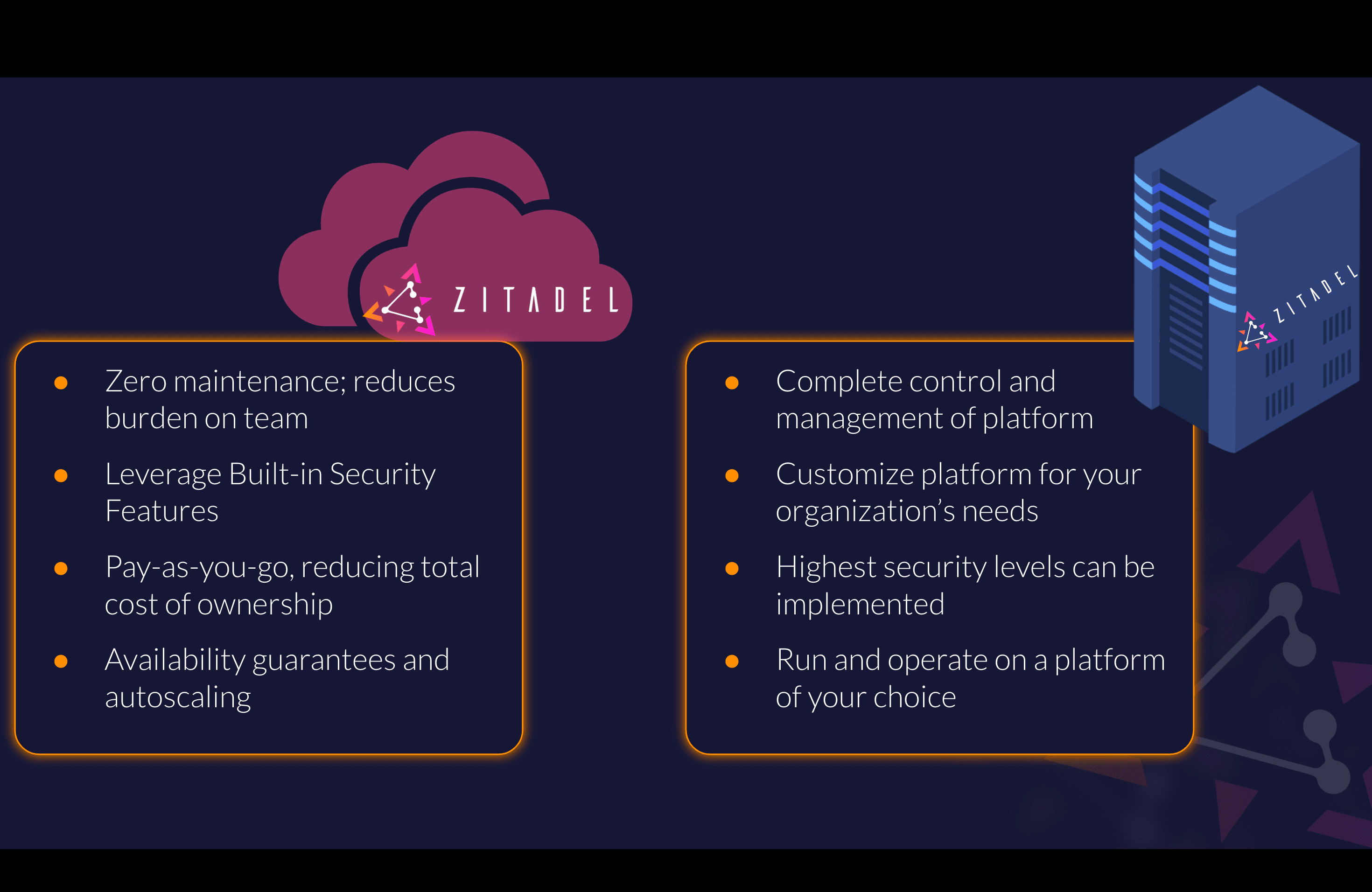
Zitadel Self-Hosted vs. Cloud: Making the Right Choice
A blog post detailing the use cases that best suit a self-hosted vs. cloud model for an IAM Platform while demonstrating the flexibility offered by Zitadel
• 7 min
Introducing our New TypeScript Login
We've developed a new TypeScript-based login system to streamline the authentication process for our customers.
• 7 min
End Of Year Product Wrap Up 2024
Have a look at our great product enhancements of 2024 and what is ahead for 2025.
• 8 min
Hopp Schwiiz - Company retreat V4
Discover how our fourth team retreat in Zurich turned last-minute challenges into opportunities for collaboration, connection, and cultural exploration.
• 9 min
Zitadel: The Future of Identity Infrastructure
Zitadel raises $9 million in Series A to advance the future of identity infrastructure to a cloud-native, multi-tenant, and developer-friendly platform.
• 5 min
The Complexities and Pitfalls of Multi-Tenant Identity and Access Management
This post explores the complexities and solutions of multi-tenant identity management in modern SaaS environments.
• 8 min