Product Newsletter March 2024
This is Max from ZITADEL. In this newsletter, I would like to highlight some of our product updates, and tips and tricks in making your identity infrastructure easier and more effective. This is the March 2024 edition of our newsletter.
Feature highlights
In March, the team shipped over 110 improvements and features to ZITADEL, including many bug fixes and stability improvements. We also delivered critical security patches for issues that were reported by the community and customers. Most of the new feature development in March contributes to our roadmap items and improves the user experience.
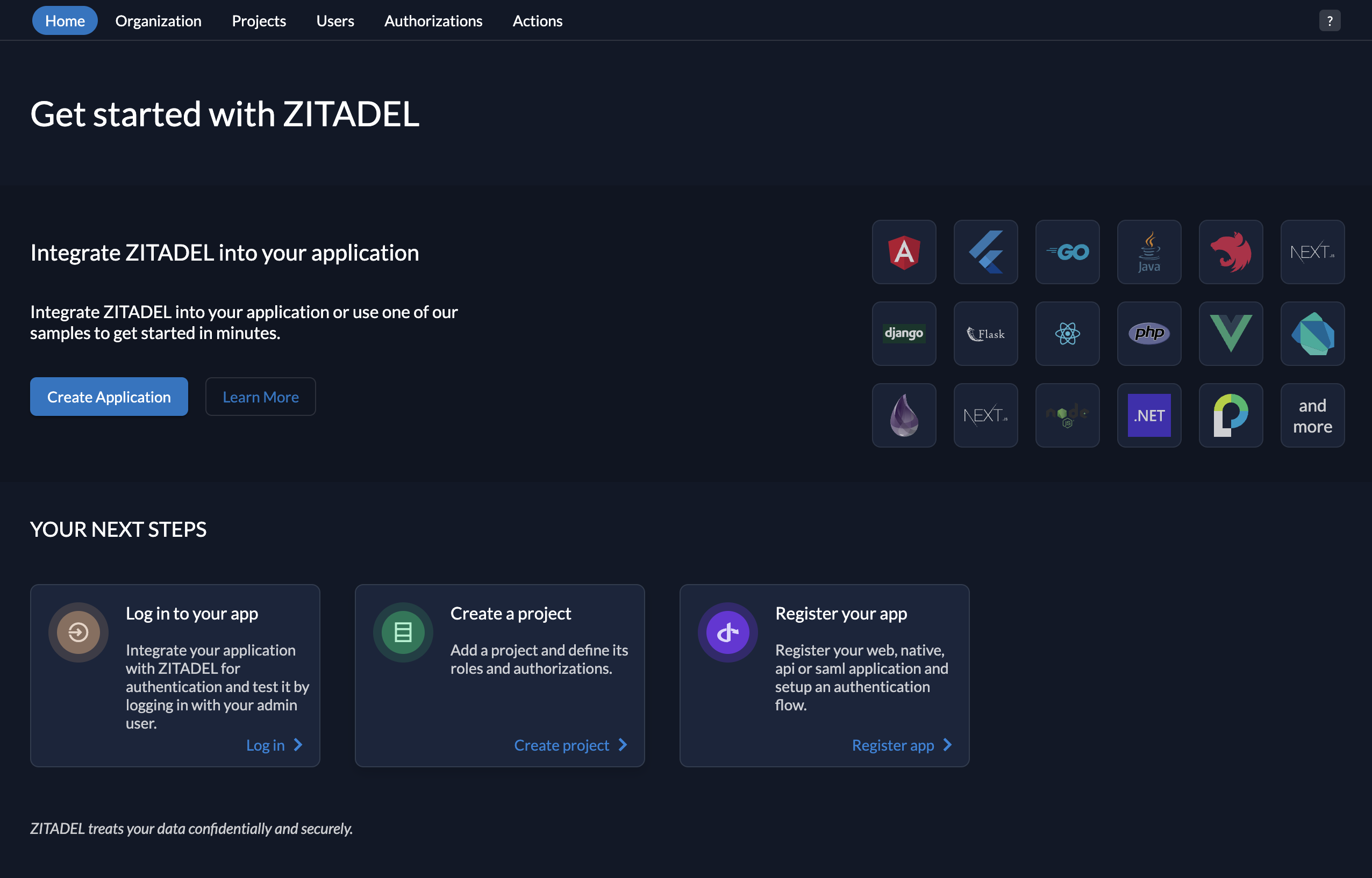
Easier integration with your frameworks
Simply set up a client application in your framework and programming language. You can choose your framework in the Console, and we take care of the default settings for you so you can get started even faster.
Of course, you can still integrate with any other framework or language.
Better descriptions and tooltips
While you can use the APIs to configure ZITADEL, many users rely on the Console as a user interface to configure their system. Descriptions, tooltips, and labels of both the default settings and the organization settings pages were adapted for clarity and to provide more information to users.
The latest stable version is 2.43.11. You can find the version of our stable release information in our documentation. Some features are only available in the latest versions.
New docs resources
This month, we worked on several documentation resources to help developers use and integrate ZITADEL more effectively.
- How to handle session validation when building your own login UI
- Using OKTA SAML IdP for single-sign-on
- Using Entra ID SAML IdP for single-sign-on
- Code example for ZITADEL actions
- Guide on how to login users with SSO in ZITADEL
- Reworked service user authentication and guides on how to access ZITADEL APIs
- Streaming audit logs to external systems such as SIEM/SOC
Technical & security advisories
Technical advisories (“TA”) are notices about major issues with ZITADEL Self-Hosted or the ZITADEL Cloud platform that could potentially impact security or stability in production environments. For example, we issue technical advisories if breaking behavior was introduced in a release or if you must expect downtime during an upgrade.
Review and subscribe to our technical advisories
Security advisories are notices about security vulnerabilities that affect ZITADEL. While we patch ZITADEL Cloud automatically, these advisories are critical for self-hosted deployments. Make sure to subscribe to “Security alerts” on our GitHub repository, by clicking on “Unwatch”, then “Custom” and selecting “Security alerts”.
Review past security advisories
Both technical and security advisories contain the details about the issue, affected versions, and how to resolve the issue.
What we’re working on
Behind the scenes, the team is continuously developing and refining the next major feature and improvement.
We needed to make delivery of alpha (experimental) and beta features safer and easier for users. With the recent releases in March, we introduced feature flags via a feature API, allowing users to enable features that are not yet intended for general availability for testing purposes.
In March, we made significant progress on these features. Make sure to subscribe to the underlying GitHub issue to receive regular updates.
- Impersonation enables a functionality to impersonate users to act on behalf of other users. Our efforts in March focused on security settings, Manager roles, and token exchange. We expect to release a preview of the feature in the coming weeks.
- User Schema: Implementation for user schemas has started with the first APIs becoming available. This feature is still experimental and behind a feature flag.
Community building: Contributions and feedback
Token exchange (RFC8693) is a permissive standard that we will implement to facilitate use cases, such as the impersonation of users. We hope to gather some feedback on our implementation from our community.
Give your feedback on Token Exchange and impersonation.
In March, our community contributed to ZITADEL and our libraries again. Thank you for your continuous support!
- ay4toh5 implemented the OpenID Connect form_post response mode, increasing interoperability with client applications of our zitadel/oidc library and in the further development of ZITADEL itself.
- doncicuto added expiration date information for service users’ keys. Keys expire at midnight (UTC), and that information was previously not displayed to users.
- vigneshsankariyer1234567890 realized we were misaligned with our login button in the email verification and fixed it, while github-tijlxyz corrected a mistake in our keycloak migration guide
- bjw-s and pisarz improved our charts allowing additional pod labels and introducing parametrization to probe schemes
- PaulHiryliuk and petrmifek helped by reviewing and improving Czech and Russian translations
We are really grateful to receive all the big and small contributions and the countless feedback and improvement ideas. In case you want to contribute, start with our contribution guide.
