Product Newsletter April 2024
This is Max from ZITADEL. As always, I would like to highlight some of our product updates, and tips and tricks in making your identity infrastructure easier and more effective.
Summarizing the April product updates for ZITADEL is a difficult task. While we continue to work on the big roadmap items, the team worked diligently to address improvements ranging from new security features to performance enhancements to secure millions of identities. We shipped over 76 features, improvements, and bug fixes to our products. For those keeping score, that is nearly 400 year to date.
Feature highlights
Let me share some of the more noteworthy features that were shipped during the month of April.
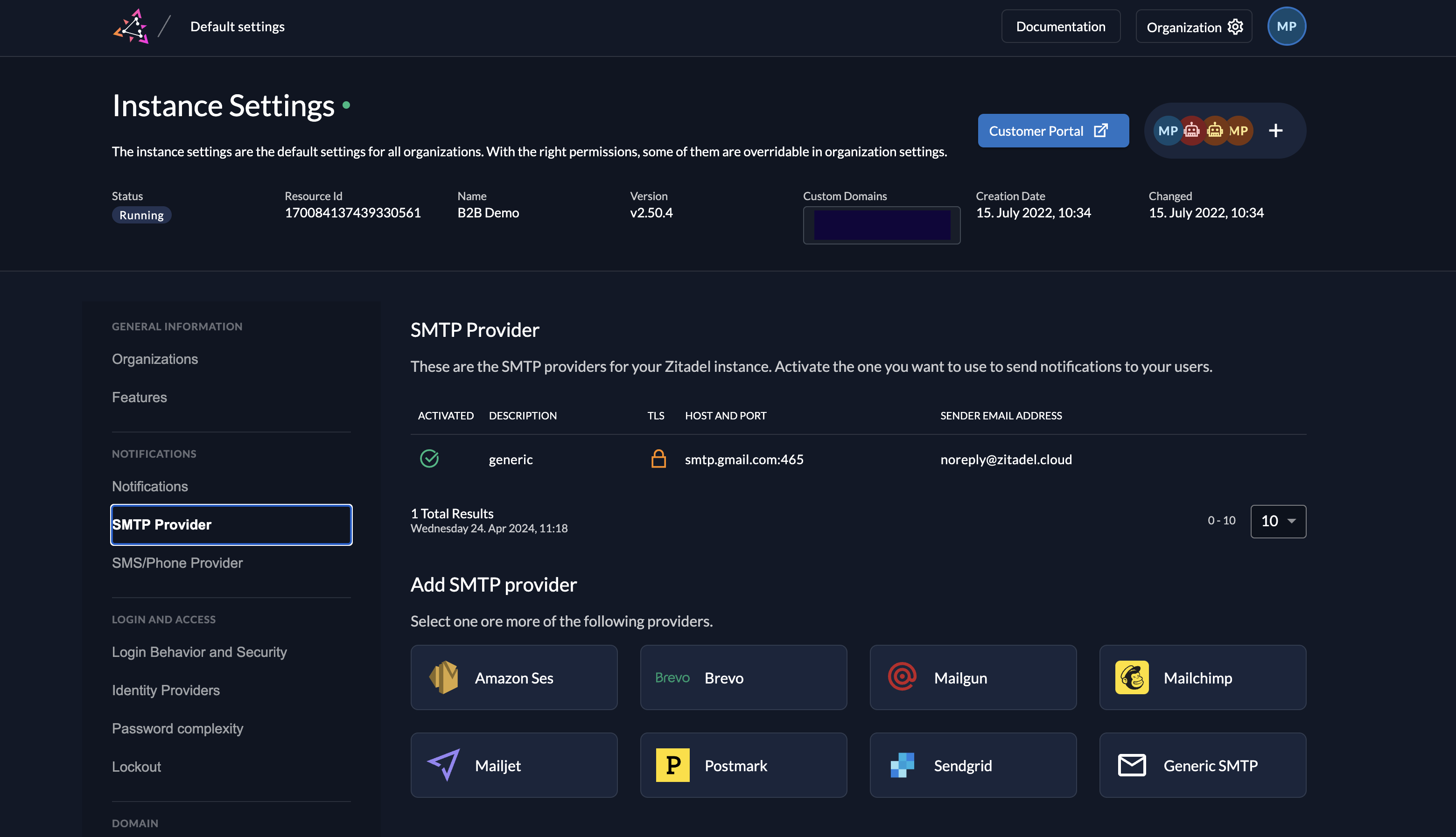
Setup your email provider - easier than ever
A generous contribution from our open source community, simplifies the configuration of email delivery within ZITADEL by introducing SMTP provider templates. These templates offer pre-defined settings for popular email service providers (ESPs) like Amazon SES, Mailgun, Mailjet, Postmark, Sendgrid, and a Generic SMTP option.
By the way, we strongly recommend replacing the pre-configured SMTP service in ZITADEL Cloud. The default provider is for demonstration purposes only and will not provide a reliable way to send emails to your users.
Link accounts with external identity providers
There are situations where your users might have created an account in your application and only later on want to connect their social login or external identity provider.
As of now an error might have been shown to the user, since the IdP link was not known before, but the automatic federation / creation failed, because the information (e.g. username) already existed in ZITADEL.
With a newly introduced functionality, users can connect their account with an account provided by an external identity provider. Administrators can configure how accounts should be matched against usernames or email addresses.
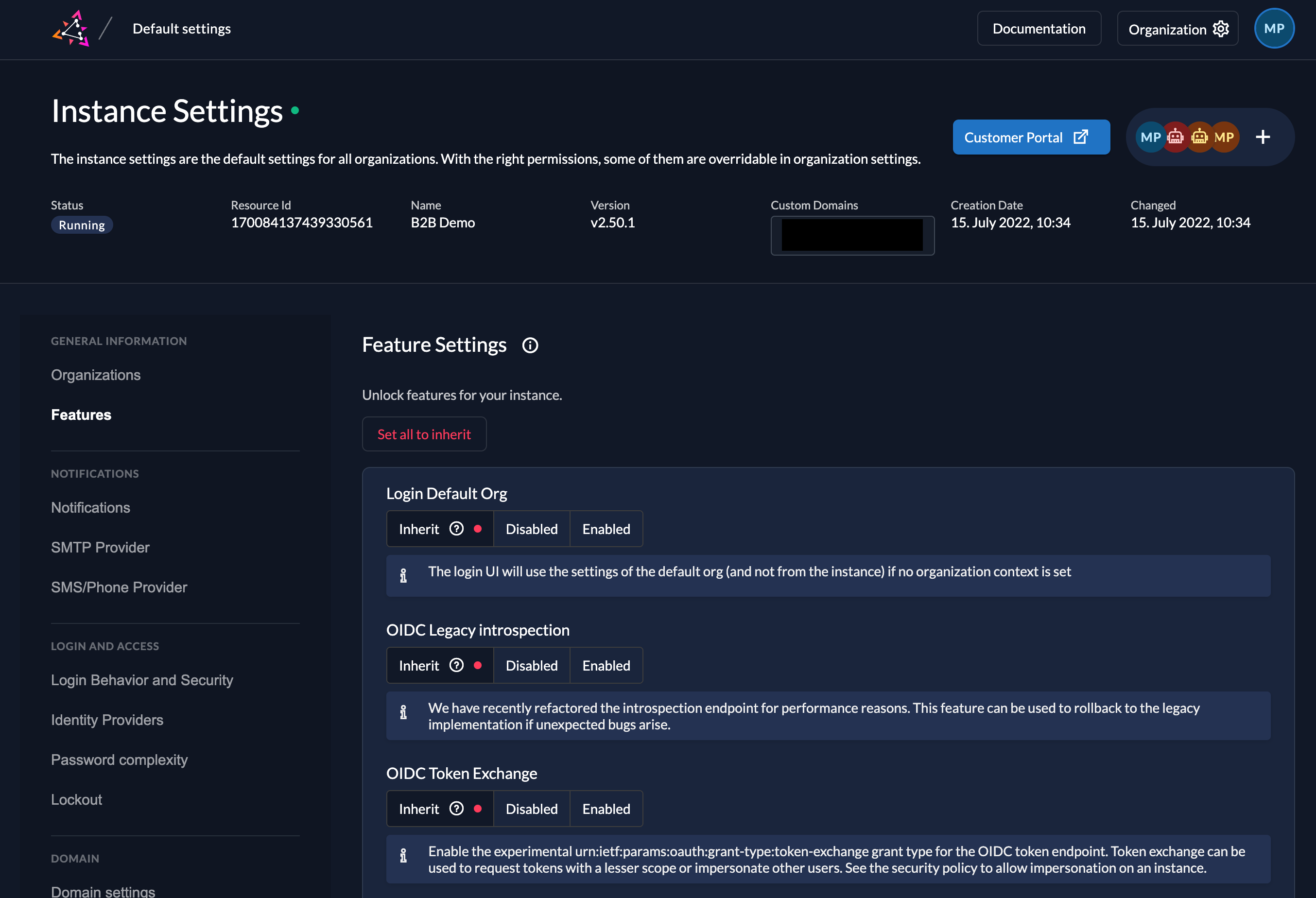
Experimental features
Over the past weeks we introduced feature flags into the core of ZITADEL. Feature flags allow administrators to opt-in or opt-out of experimental features that are not intended to be generally available. In April we finished the work by shipping the new feature settings into the Console.
Our intention with feature settings is to provide means to access and test early features for users to test and provide feedback. Among the currently available functionalities are several performance improvements, OpenID Connect Token Exchange, a preview of User Schemas, and a preview of a more powerful Actions feature. Some settings allow you to roll-back some improvements that would result in issues to few users.
Limit one-time password attempts
Similar to the existing lockout functionality for password attempts, Managers are able to configure automatic lockouts after a specified number of consecutive failed Time-based One-Time Password (TOTP) checks. The new feature strengthens security posture by mitigating brute-force attacks targeting (T)OTP verification.
Lockouts are applied independently for each TOTP method. This ensures users retain the ability to attempt alternative verification methods (e.g., email OTP) even after exceeding the threshold for a specific TOTP method (e.g., mobile app).
View all changes on our new changelog
ZITADEL Cloud for scale and simplicity: focus on what matters most
We have no plans of moving to a cloud only service. Let me state that right at the start. There are many reasons and use cases to go for an enterprise grade identity management solution that runs on your private infrastructure, ranging from compliance requirements and risk reduction to special cases such as embedded systems.
In a self-hosted setup you will not only be responsible for managing the infrastructure layer, but also the operational security aspects of the deployment. When using cloud you don’t have to worry about DDoS attacks, WAF configuration, or bot detection during login and register. These are all covered by our systems, have a look at our shared responsibility matrix to learn more.
The Pro plan now includes 25’000 daily active users per month. The cost for additional daily active users was also reduced to offer you better scale. We will streamline our subscriptions and update all existing plans that use authenticated requests to an up-to-date plan. No action is required on your end, the changes will be applied automatically on July 1st.
What we’re working on
Feedback wanted on Token Exchange
We are very happy to announce that OAuth 2.0 Token Exchange according to RFC 8693 landed in ZITADEL. This grant will lay the foundation for more advanced integration scenarios, including impersonation of users, token validation and exchange with third-party identity providers, and exchange of session tokens and OAuth tokens.
To get started, follow our integration guide on Impersonation and delegation using Token Exchange and make sure to enable the feature in the newly introduced feature settings.
We would very much like to get your feedback on the implementation and learn more about your use cases. Join the discussion on our Github repository.
A new login UI in typescript for you to make your own
Already today you can use our hosted login UI for the highest security standards. For a couple of months you are also able to use the Session API to build your own login interface and user flows.
We are currently working on a next generation of our login page, written in Typescript, that will replace our existing hosted login UI. The goal is to implement a login UI, using the session API of ZITADEL, which also implements the OIDC Standard and is ready to use for everyone.
In the first phase we want to have a MVP login ready with the OIDC Standard and a basic feature set. In a second step the features will be extended.
As always, we value your early feedback, ideas, and contributions to the next generation of our - and hopefully your - login experience.
Better together
Our community members contributed 23 improvements and features to ZITADEL repositories. I want to thank you for your continued support and the time you put in to make the project better for everyone.
- The feature SMTP templates for the most popular email service providers was contributed by doncicuto. Not only a great feature, but also a lot of testing involved - a special thanks for that contribution
- aDogCalledSpot added the option to use locally generated RSA keys for service users, avoiding keys being sent over the network instead
- Doncicuto contributed also to multiple parts of the console to fix reported issues, improving the overall usability of the UI and APIs
- Compatibility of oidc client device authorization grant with Google by celian-garcia and ability to verify ID tokens based on available sign algorithms from the discovery endpoint by otakakot
- vigneshsankariyer1234567890 improved UX where users switching between register and login got lost
- celian-garcia , jkroepke, and otakakot improved error handling in our oidc library
- yordis, zoltantemesvari, ahmednfwela, and HaimKortovich helped us to improve and keep our SDKs up-to-date
- Charts repository dependencies by rud and improved configuration of ports ameijboom
- Typos and corrections to docs EthanHeilman, alexrimlin, and thamow
Thinking of contributing? Grab a ‘good first issue’ or start a discussion and get started with our contribution guide.
Additional resources
- ‘Worth exploring’ - Thoughtworks technology radar
- Video: Complete Guide to Identity Federation and Brokering Using ZITADEL
- Built with ZITADEL: 23 Technologies' Kubernetes-as-a-Service
- Test Token Introspection in ZITADEL with Postman
Thanks for reading,
Max
