Blog.
- #auth0 alternative
- #Authentication
- #custom login
- #API
- #keycloak vs. zitadel
- #auth0 vs. zitadel
- #PHP SDK
- #Ruby SDK
- #Build vs. Buy
- #typescript-login
- #GRPC
- #Python SDK
- #terraform
- #Authorization
- #zitadel
- #announcement
- #Beyond Authentication
- #actions
- #token-management
- #SDK
- #oidc
- #Zitadel SDKs
- #iam
- #multi-tenancy
- #iaac
- #zitadel_cloud
- #community
- #about_us
- #Service Ping
- #Java SDK
- #engineering
- #keycloak alternative
- #how-to
- #features
- #imo
- #open_source
- #pentest
- #security
- #self_hosting
- #case_studies
- #alternative
Navigating Session Logouts, Timeouts, and Token Expiry
Using ZITADEL's OIDC integrations as a guide, this article offers insights into mastering the essential security measures of session timeouts, logouts, and token expriy.
• 17 min
Built with ZITADEL: Orbica's Cloud Native Geospatial Platform
Exploring how Orbica leveraged ZITADEL for exclusive authentication in its geospatial platform.
• 10 min
From Persona-based to Resource-based: Rethinking ZITADELs API Design
We decided to adopt a resource-based API for ZITADEL in response to feedback from our customers and community members.
• 5 min
ZITADEL in the Classroom: A Look at smartive's and OST's Advanced Frontend Engineering Course
Smartive and OST have enhanced the user experience in their Advanced Frontend Engineering Course by utilizing ZITADEL.
• 9 min
How MFA Fatigue Attacks Compromise User Security
This article discusses MFA Fatigue Attacks targeting MFA systems with push notifications and how we can mitigate them.
• 7 min
ZITADEL and Fine-Grained Authorization: A Code-Focused Exploration
This articles showcases fine-grained authorization with ZITADEL and delves into managing access control, validating tokens, and separating business logic from authorization rules.
• 14 min
5 Authentication Methods at ZITADEL - Ranked from Least to Most Secure
This article showcases ZITADEL's five implementable authentication methods ranked from worst to best regarding security and user experience (UX).
• 8 min
Reuniting Across Boundaries: Our Unforgettable First Team Retreat
This article recounts the journey of our first team retreat as a remote-first company.
• 8 min
How Password Hashing and Salt Can Enhance Password Security
This article discusses the importance of password hashing and salting to secure password storage.
• 5 min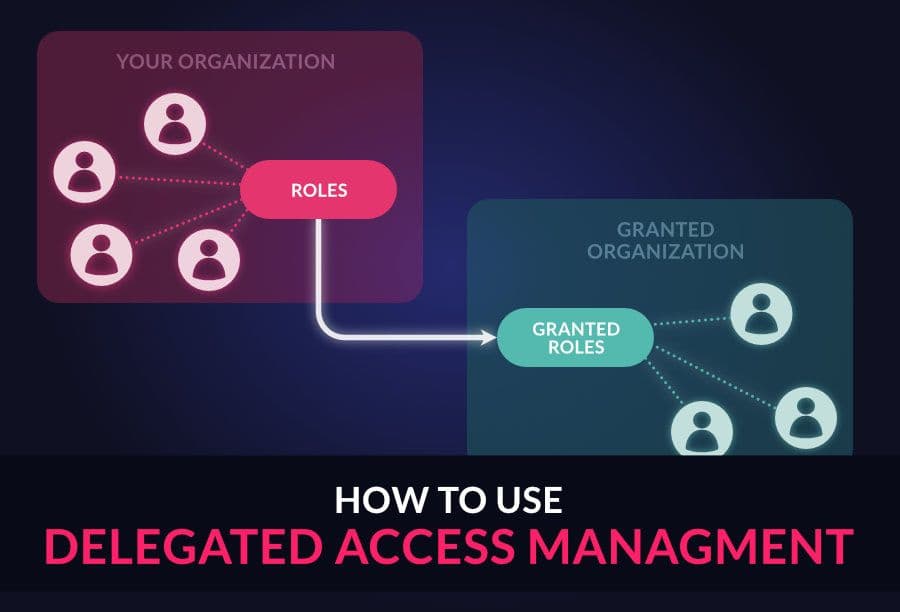
Multi-Tenancy and Delegated Access Management with Organizations
This article explains the most important concepts on how you can structure your multi-tenancy identity architecture with organizations.
• 11 min
Single Sign-On (SSO) vs. Federated Identity Management (FIM) - The Key Differences
Numerous businesses have implemented solutions like federated identity management (FIM) and single sign-on (SSO) to enhance authentication process security while minimizing password fatigue. This article discusses the difference between these two approaches.
• 6 min
Comparing ZITADEL to Firebase
The purpose of this article is to guide readers on what are the differences between ZITADEL and Firebase
• 11 min