Social Engineering - How Hackers are Manipulating You

Marketing
When we think of cyber criminals, the first image that commonly comes to mind is a mysterious computer expert seamlessly accessing all of a platform's data with a few keystrokes. Astonishingly though, brute force only accounts for 2% of cyberattacks - the remaining 98% involve a non-technical hacking method relying on human interaction, known as social engineering.
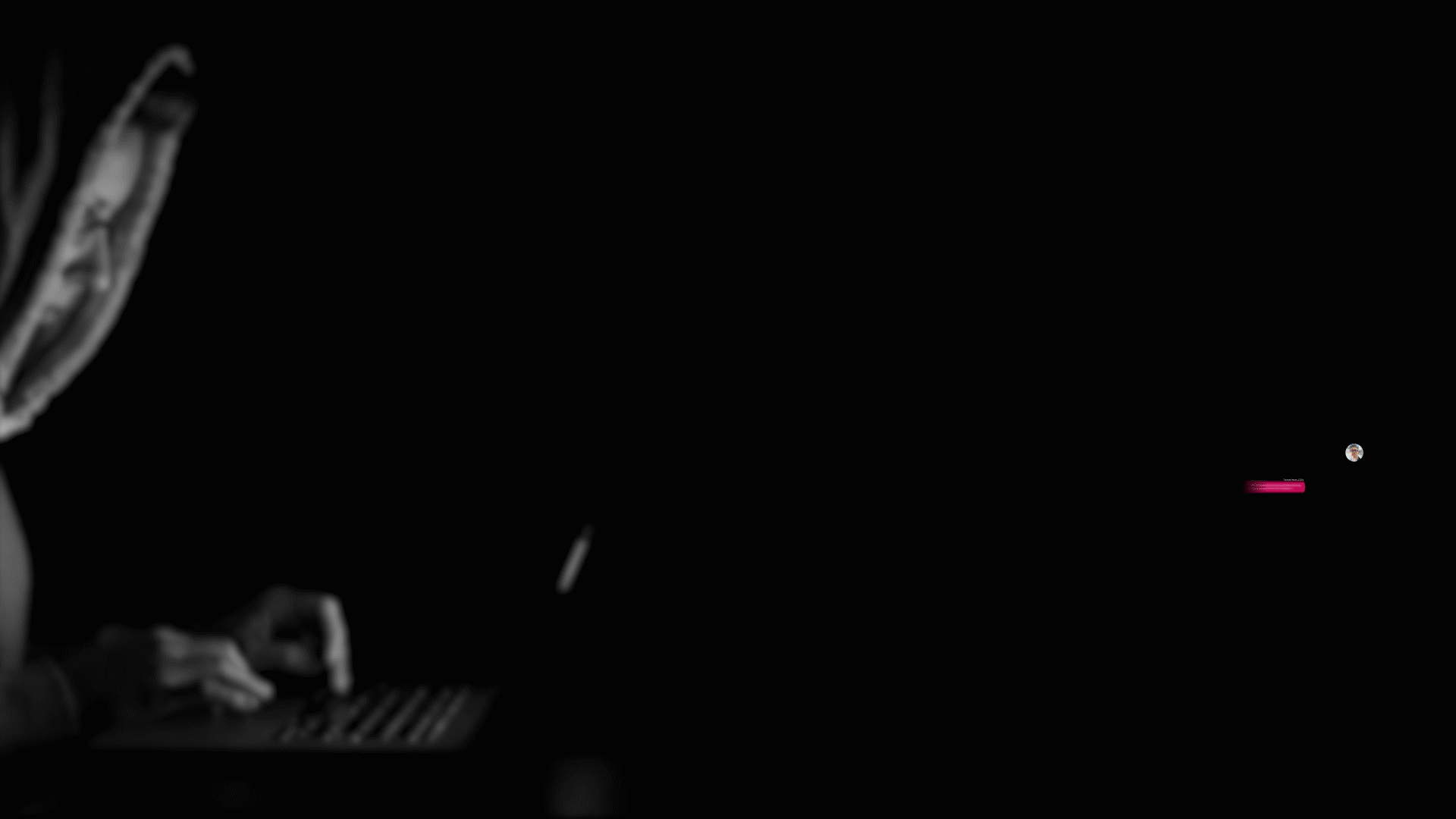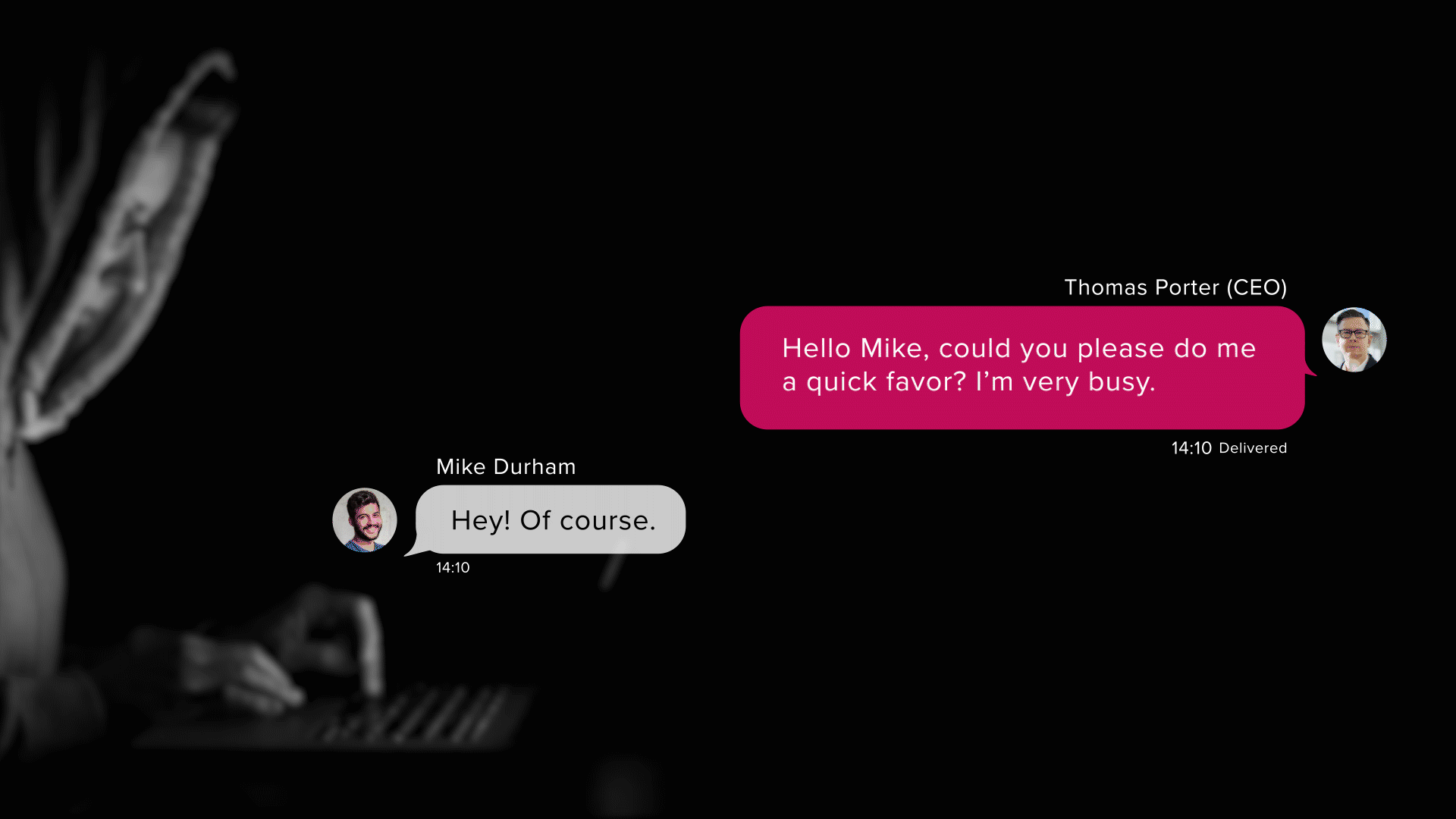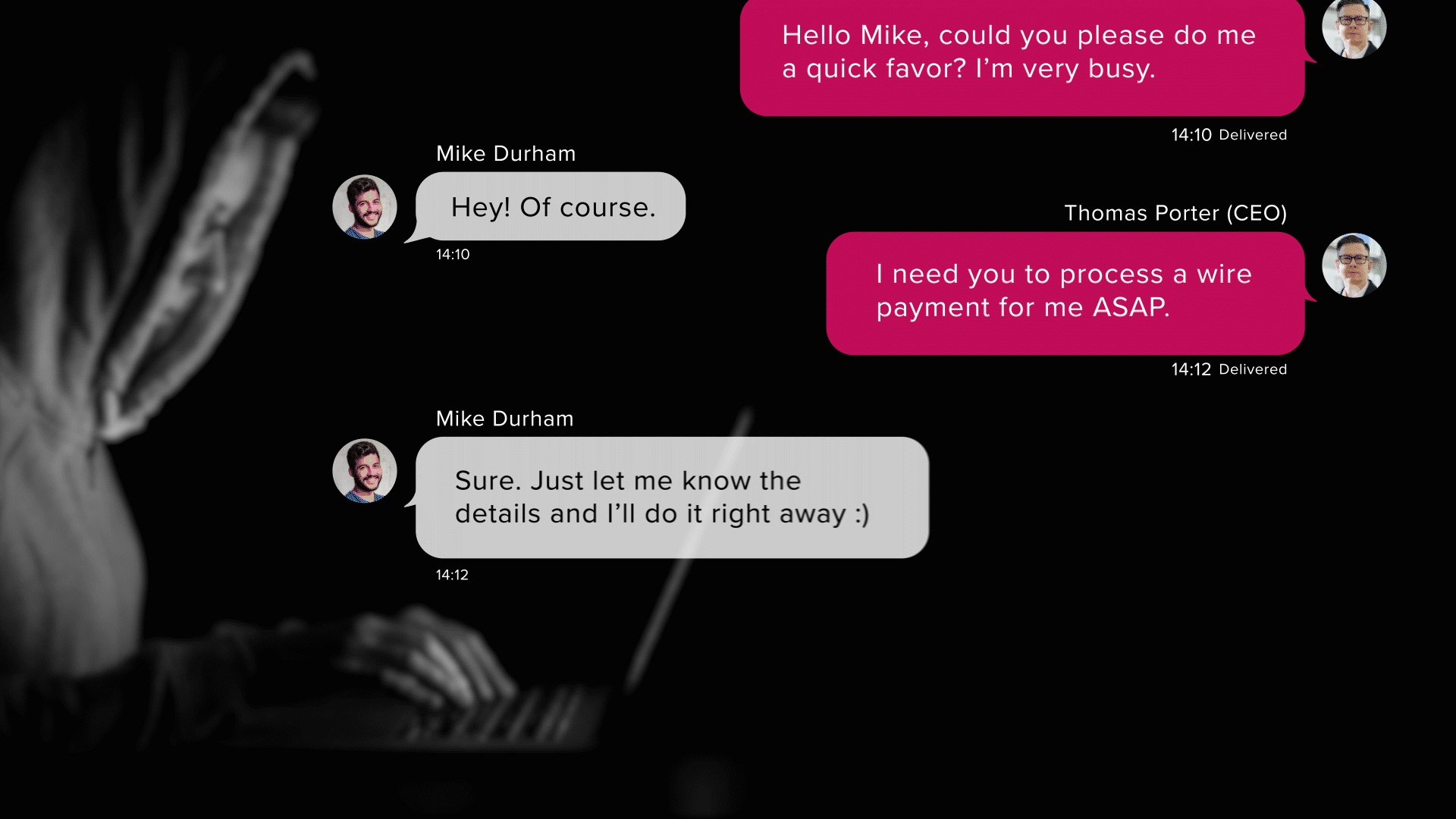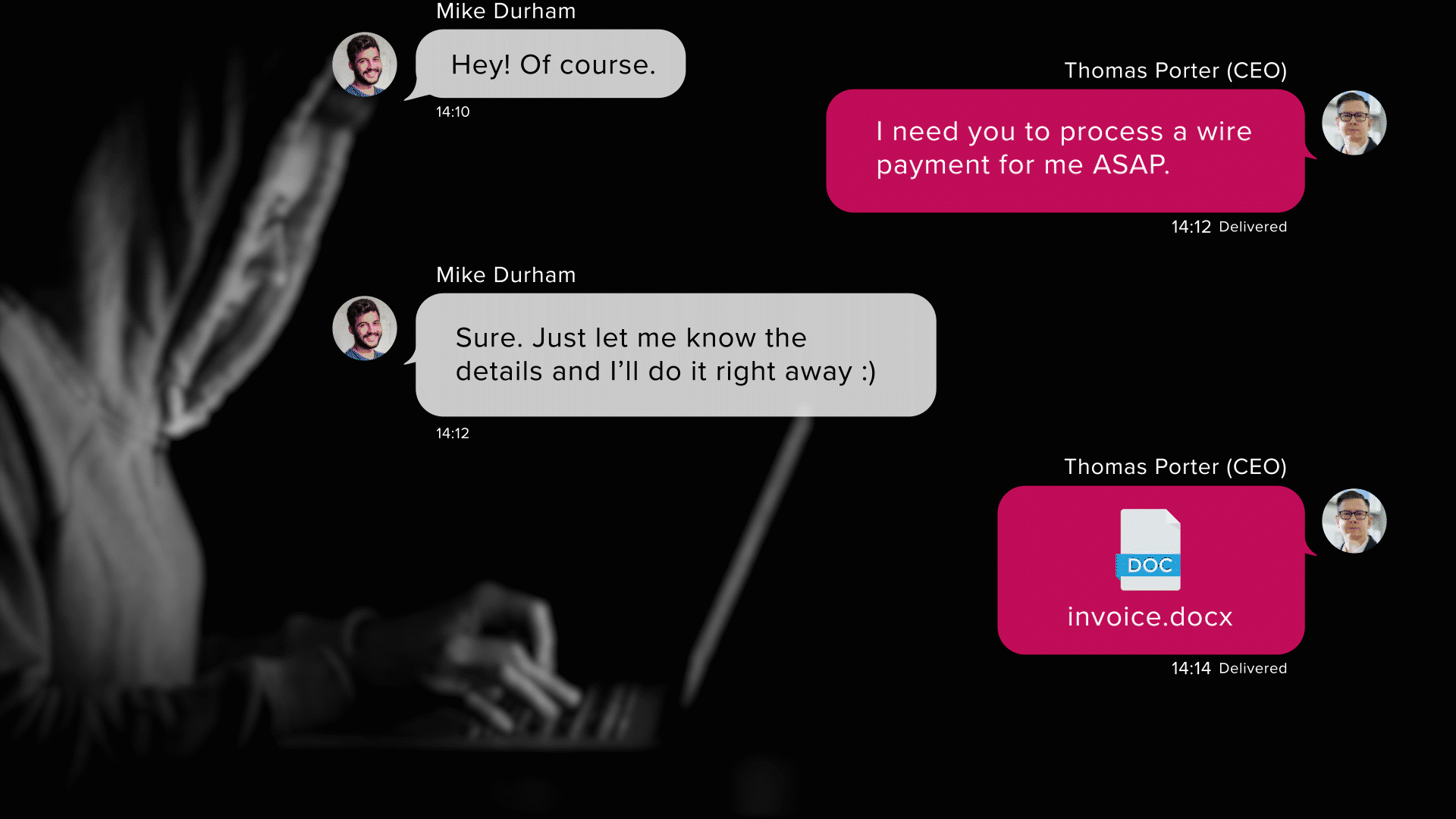
What is social engineering?
Social engineering is a general term for non-technical attacks employing deception to exploit people's good intentions and trust to acquire sensitive data. From commonly seen scam e-mails to the exploitation of CEOs, social engineering techniques heavily vary in their scales and stakes. These diverse techniques, combined with the lack of required technical knowledge, make this attack accessible to anybody with malicious intentions, placing everyone who uses technology and interacts with people at risk.
This article discusses the six most commonly encountered social engineering tactics and how to protect your account from cybercriminals.
6 Common types of social engineering attacks
1. Phishing and Whaling
As the most common form of social engineering, phishing has become an inescapable term in cybersecurity. It describes a virtual attack during which attackers send messages posing as reliable entities to trick users into giving away personal information or installing malware via a malicious link. These messages usually depict situations that, due to their urgency, are known to grab the victim’s attention, such as a package delivery notification, a purchase confirmation, or a credit card suspension notice.
While fraudulent e-mails are the most widespread phishing tactic, the attack takes many forms. Smishing (SMS Phishing), Vishing (voice phishing), and Spear Phishing are all smaller-scale methods commonly used to target everyday individuals. Whereas the former two alternatives generally rely on ambiguous situations that anyone could experience, spear phishing messages aim to explicitly captivate a specific target by involving personal details about the victim (f.e. an e-mail from the gym they attend).
Akin to spear phishing, whaling is a targeted phishing scam; however, as the name implies, it aims to catch “bigger fish.” The goal of the attack is to exploit the influence high-ranking individuals (such as CEOs) of companies have by spoofing their e-mail addresses and sending fraudulent messages to their lower-ranking co-workers. Due to the instructions of the phishing message seemingly coming from a trusted higher-up, the targets are more likely to fall victim to the scam.
2. Baiting
When you are trying to catch a fish, you may discover that it is much more likely to bite the hook if equipped with an alluring bait. The same simple principle can be applied to a social engineering attack.
Baiting attacks put something intriguing in front of their target to trick them into giving away their personal or financial information or downloading malicious software. The bait in question could come in many forms, such as a gifted USB inflicted with a virus or an online ad luring people to malicious websites. Either way, it is intended to be hard for the victim to resist.
Akin to other social engineering techniques, baiting thrives on exploiting the flaws of human nature. If someone is nice enough to make us feel special, we are taught not to look a gift horse in the mouth - especially if the item or the deal seem authentic.
3. Pretexting
Pretexting is an exceptionally calculated social engineering attack that strives to get people to give away sensitive information under false pretenses. It generally involves the scammer creating a fake scenario under a false identity to trick corporations into providing access to their databases.
While the concept of pretexting might sound similar to phishing, they vary in their motives: the former solely aims to set up a successful future attack, while the latter is generally the attack itself.
An infamous example of a pretexted scenario leading to a powerful attack occurred in 2019 when a hacker impersonated a CEO’s voice with AI software. In this case, the attacker established an employee’s trust by claiming the identity of his boss and subsequently urged him to transfer €220,000 to a made-up supplier. And just like that, an imaginary scenario and a phone call were enough to scam a company out of thousands of euros.
4. Honey Trap
While bosses can undoubtedly sway people to follow orders blindly, their influence is still inadequate compared to the power of love. Though the internet has blessed us with the chance to find our soulmate while lounging at home, it comes with the curse of commonly deceptive self-representation.
Honey Trap (aka. Honey Trapping) is a type of social engineering attack in which the attacker seduces the victim into an online relationship, usually using a fraudulent profile of an attractive person. The perpetrator then exploits the trust and devotion of the victim towards their “partner” to yield personal information or large sums of money.
While the technique of honey trap is commonly used with the previously mentioned malicious goal in mind, it can also serve an investigational purpose: For example, to prove that a partner is unfaithful.
5. Tailgating and Piggybacking
Unlike most social engineering attacks, Tailgating is carried out in the physical world. It involves an attacker closely yet unnoticeably following an authorized person to gain access to an unauthorized location. The technique can be as simple as the offender using an object or body part to prevent the door from closing after the authorized person has entered the area.
While Tailgating requires the attacker to be stealthy, Piggybacking relies on the authorized person to voluntarily grant access to the restricted area. Of course, the offender will use deception to earn this grant, such as by pretending to be a new employee who forgot their keys.
6. Quid pro Quo
We have all heard of the golden rule: “Never give away personal information to strangers.” But what if the stranger needs them to help me fix an issue?
“Quid pro quo" (Latin for "something for something") refers to a social engineering attack where the attacker offers to exchange a service for information. For instance, they might pose as an IT worker and offer to inspect your computer for viruses to improve its performance. All they need is your login credentials to access the required platform. Of course, you want them to be able to perform the promised service, so you comply without giving it a second thought. Little do you know, you have just directly placed your valuable data into the wrong hands.
How to prevent social engineering attacks
Evidently, social engineering is a severe security threat that can lead to devastating consequences. Fortunately, though, it is preventable. If you would like to drastically minimize the likelihood of falling victim to a social engineering attack, we recommend taking the following precautions for your safety.
Keep an eye out for suspicious messages and links
Since many legitimate messages aim to redirect users using an attached link, it can be tricky to spot a social engineering attempt confidently. Luckily, there are some common indicators of smishing and e-mail phishing attacks to look out for:
- The message asks you to click on an URL with a domain that does not correspond to the service’s name. Furthermore, shortened URLs (f.e. starting with bit.ly, cutt.ly, and shorturl.at) are generally not trustworthy in the context of e-mail and SMS messaging.
- The message is very generic – Legitimate senders generally include the package number, your bank’s name, or your name/nickname, depending on the context.
- The message contains spelling- or grammatical errors - Texts from service providers are usually automated, so the possibility of a typo would be extremely low.
- The number or e-mail address of the sender and the service provider they claim to be, do not match. Moreover, when you receive a message from bigger service providers (f.e. banks, post offices, or delivery services), they will mostly display their company names instead of their numbers.
- The last warning - If you do click the attached link and a warning pops up that the site you will be redirected to is not secure, do not proceed.
If the text or mail you received is guilty of at least one of the formerly listed signs, refrain from opening attachments or links. Furthermore, replying or calling the attacker would be counterproductive – Doing so confirms that your number/e-mail address is in use, making you a potential target for more attacks. Instead, please block the sender and report the message to your country's national cyber security center.
Limit the information you share on social media
While it feels great to share the joys of your life with others, bear in mind that the more information that is available about you online, the simpler it will be for attackers to manipulate or even impersonate you. Think about it: Would you be more likely to be suspicious of a spam e-mail sent en-masse or a personal text supposedly coming from your boss or a family member? To avoid falling victim to spear-phishing, we strongly recommend keeping personal details private or limited for viewing.
Enable Two-Factor-Authentication (2FA)
Enabling 2FA or Multi-Factor-Authentication (MFA) adds an additional layer of security to your account that is significantly harder for attackers to bypass. This protection measure requires users to provide a second factor (such as off-device access codes, biometric factors, or a physical token) in addition to their password to confirm their identity. Thus, you will immediately get notified if someone attempts to log into one of your virtual identities.
Do not give away your login credentials!
Whether it’s your online friend, a service provider, or a platform admin, a person or entity directly asking for your user credentials should always raise suspicion. It is crucial to note that a legitimate service or platform never requires users to confirm their password or access code by sending it to them via e-mail or text message.
Even if the person asking for your credentials is someone you know personally (such as a family member or co-worker), it is safest to confirm that the person truly is who they claim to be. For instance, you can ask them in person, call them, or invite them to continue the chat on another platform. Of course, the same principle applies if they request you to make a (high-value) purchase.
The Takeaway
Since social engineering attacks can be carried out by virtually anyone, we are bound to encounter an attempt at least once in our lifetimes. To prevent yourself from falling victim, your account and personal information must be adequately safeguarded.
With ZITADEL as your organization’s authentication solution, you can easily protect your end-users’ accounts and sensitive data with the help of phishing-resistant MFA options (f.e, passkeys), a wide variety of 2FA alternatives, and many more cutting-edge security features.