How Attackers Bypass Two-factor Authentication (2FA)

Marketing
Usernames and passwords - this combination represented the go-to method of authenticating users for multiple decades. However, as time passed, it has become increasingly evident that relying solely on two words to safeguard personal data is not without its devastating risks. Consequently, countless platforms continue turning to more complex authentication methods to increase their users’ safety.
Perhaps the most commonly used alternative to traditional password-based authentication is Two-Factor-Authentication (2FA), also known as 2-step verification. 2FA is a security measure that requires users to provide a second factor (such as an off-device code, biometric factor, or a physical token) in addition to their password to confirm their identity. While this extra layer of protection can undoubtedly make it more difficult for attackers to access your account, it is still not entirely foolproof.
This article discusses five typical methods attackers use to bypass two-step verification or two-factor authentication and some precautions you may take to protect your account.
The most common 2FA Bypass Attacks
1. Password reset
One of the easiest and, therefore, most common ways to bypass two-factor authentication is by simply utilizing the password reset function of websites and applications.
Although every login function should require the second authentication factor after two-factor authentication is enabled, one of them is often forgotten. A surprising number of platforms allow users to access an account after obtaining a password reset token without additional verification. Obviously, such a blatant security hole makes the job of attackers significantly easier.
2. Social Engineering
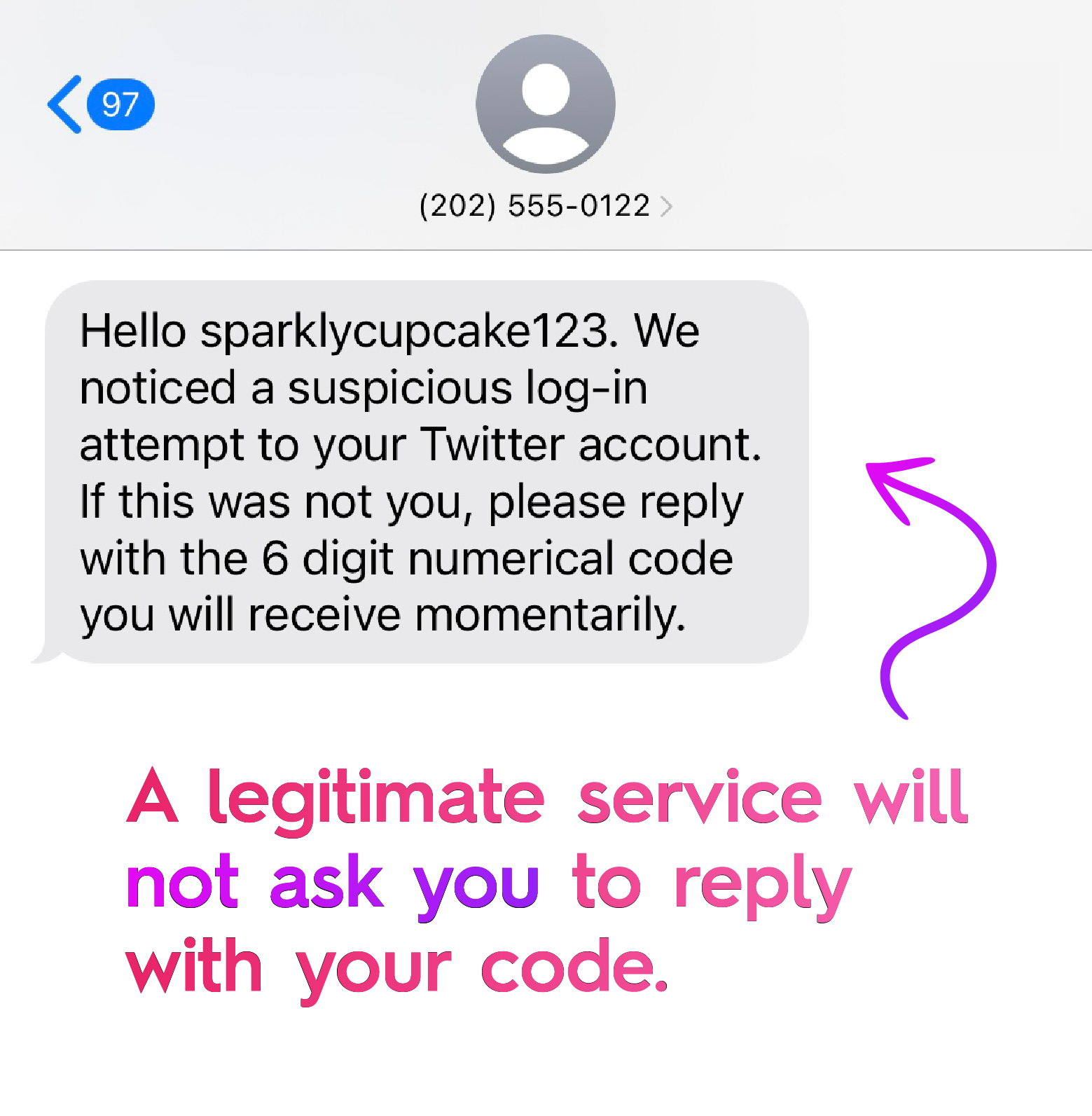
Another non-technical method of bypassing two-factor authentication is Social Engineering. While this notorious attack takes on many forms, they all share a common goal of tricking a person into giving away private information.
Even if the attacker has already obtained your user credentials, they still need to acquire the additional authentication factor to gain access to your account. To receive the required code from the victim, the criminal might call, text, or email them with a seemingly plausible justification. Of course, they will likely do so disguised as a trusted entity, such as Google or Apple, to minimize suspicion. Make sure to always double-check the sender’s identity, as well as the content of the text message, to avoid falling victim to a hacking attempt.
3. Man-in-the-middle Attacks
Tech-savvy attackers can even bypass two-factor authentication without knowing the victim’s login credentials. Man-in-the-middle (MiTM) attacks describe the phenomenon of a third party, also known as a man-in-the-middle, intercepting the communication between two systems.
Similarly to Social Engineering, MiTM attacks rely on deception to obtain valuable information from their victim. However, instead of directly asking for the two-factor authentication code, the latter method uses a malware to extract user session cookies. Since the cookies contain the user’s data and track their activity, hijacking them allows the attacker to bypass 2FA easily.
A phishing website is one of the most popular tools to conduct MiTM attacks. By posing as a trusted entity, the criminal prompts the victim to authenticate themselves via an attached link. Due to the website the user is redirected to often seeming legitimate, many people unsuspectingly enter their credentials to the proxy login page. Unfortunately, doing so allows the phishing site to obtain sensitive data about the user, including personal information, passwords or less secure second factors, and place them into the wrong hands.
4. OAuth Consent phishing
Consent phishing is a relatively new yet dangerously calculated tactic attackers use to compromise user accounts. Unlike other 2fa bypass attacks that prey on session cookies and login credentials, this technique targets users who are already signed in - making it immune to all kinds of login protection measures, such as two-factor authentication and passwordless.
If you are registered to any type of cloud-based application (such as Google Workspace and Microsoft 365), you are likely already familiar with the concept of user consent. For instance, when you use your pre-existing Google account to sign up for a third-party website or application, a consent screen will ask for your approval to access the specified data on your Google profile. Since constenting to this commonly seen prompt is necessary to utilize the platform, we tend to disregard it as a pointless reading exercise and routinely click "Accept."
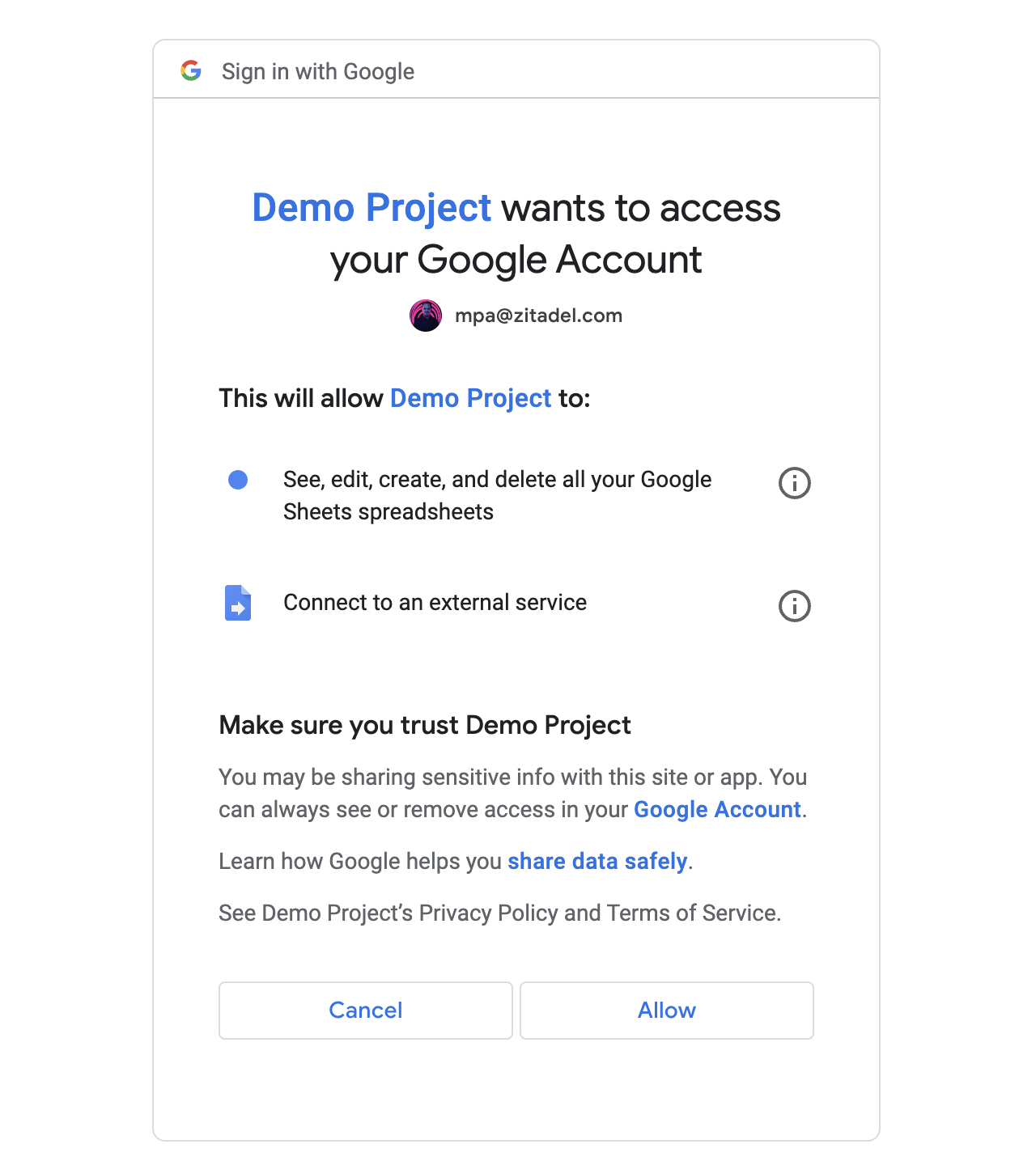
And just like that, all it took was one button hit to give the person behind the screen unrestricted access to your account, which is retained even if you change your password or turn on two-factor authentication. The actions the platform may take using the obtained information can range from exploiting your credentials to writing files and sending messages on your behalf.
While the consequences of user consent might sound concerning, if the platform requesting your permission was legitimate, it is quite unlikely that they had ulterior motives. However, OAuth 2.0, the standard protocol that lies behind these consent screens, enables almost anybody to register an application. This makes it possible for cybercriminals to exploit a seemingly reliable OAuth 2.0 authorisation exchange, by deceiving the user to grant a malicious platform access.
5. Duplicate-Generator
Akin to many other 2FA bypass attacks, the Duplicate-Generator is also intended to exploit the security holes in this authentication method. Or, more specifically, the flaws of the one-time-password (OTP).
Interestingly, many platforms seem to rely on number generators to create the security key used as the second authentication factor. These generators typically begin with a randomly chosen seed value, which is used to produce the first number in the verification code. If this seed and the algorithm are learned, the attacker can produce a duplicate of the victim’s generator that will display the identical set of numbers - and thus, find out the OTP.
6. SIM-Jacking
Similarly to Duplicate-generator, this attack operates by exploiting one-time passwords. However, rather than relying on an OTP copy, Sim-jacking ensures that the authentication code lands directly in the hands of the hacker.
As the name suggests, this OTP bypass method involves the attacker hijacking a user's SIM card to take over their phone number. Given the complexity of contemporary hacking techniques, the criminal does not need to physically possess the SIM to exploit it. Simply tricking a mobile phone provider into adding the targeted number to the attacker’s phone will allow them to get all text messages intended for the victim - including the OTP.
How you can protect your account
Despite its shortcomings, two-factor authentication still remains among the most effective methods for safeguarding your own account. Although some may have figured out how to bypass 2FA, there are several countermeasures to stop such an attack from happening.
Be Careful With OTPs
Due to their straightforward usage and quick setup, OTP security codes have established themselves as the go-to secondary authentication factor for numerous accounts. Unfortunately, their simplicity is also their most significant vulnerability.
If you are worried about falling victim to sim-jacking or a duplicate-generator attack, consider applying one of the following practices:
- Switch to an alternate 2FA method - such as biometric authentication or physical tokens.
- Use an authenticator app to receive the OTP - such apps (f.e. Authy) exclusively display the verification code on the device you are using and do not rely on an SMS.
Switch to Passkeys
Passkeys is an alternate authentication method that entirely relies on a private-public key exchange between a device and the service to verify a user’s identity. The private key is securely stored on the device and requires the user to provide a second factor, such as biometrics, to unlock the key. Although both two-factor authentication and passkeys undoubtedly surpass traditional password-based logins in terms of security, the latter method is less susceptible to phishing and cyber-attacks due to their complete waiver of passwords.
Evaluate Consent Requests
To prevent a fraudulent website or application from using OAuth 2.0 to delegate access, we strongly advise users to carefully review the consent request, as well as the data and the permissions it is asking for. If you spot a spelling or grammatical error within any text the application displays, the platform is probably illegitimate. Even if the domain appears to be trustworthy, keep in mind that attackers frequently spoof these to appear to be from a reputable service or company.
If you have any suspicion about a platform attempting consent phishing, please report it either directly on the consent prompt or to the national cyber security center in your country.
Never share your Authentication Code!
Last but not least, consider the age-old rule of keeping your account safe: Never share your verification code/link with anyone. Remember: No legitimate service will ever ask you to reply with the credentials they have (supposedly) just sent you.
In Conclusion
As methods for bypassing two-factor authentication advance, so must our countermeasures. With ZITADEL as your organization’s authentication solution, you can easily protect your end-users’ account and sensitive data with the help of a safe mechanism for password reset, phishing resistant MFA options (f.e passkeys), a wide variety of 2FA alternatives and many more cutting-edge security features.