Built with ZITADEL: Open Systems' IAM Strategy for Global Networks

Developer Advocate

Key Outcomes
-
Open Systems has adopted self-hosted ZITADEL to modernize their identity and access management. This adoption provides a robust authentication framework for their customer portal, serving a large customer base with diverse global networks and is pivotal in managing secure access to their backend systems for both admin users and potentially end users in the future.
-
The decision to switch to ZITADEL was driven by its seamless integration with various third-party identity providers, cloud-native design, self-hosting capability, and adaptability in accommodating new features and custom requirements. This strategic choice allows Open Systems to stay ahead with a modern authentication stack, offering significant improvements over the previous legacy RADIUS-based system and well-known solutions like Auth0 and Microsoft AD (now Entra ID).
-
This shift to a more advanced, off-the-shelf solution aligns them with current identity management trends. It drastically cuts down development time, with the setup now accomplished in just 15 minutes per customer, as opposed to the previous duration of 24 hours. Furthermore, it enhances system compatibility across diverse Identity Providers (IdPs) and streamlines risk management effectively.
Introduction
Open Systems is a leader in networking and cybersecurity, primarily focusing on the Secure Access Service Edge (SASE) domain. With a customer base of around 200, primarily large-scale organizations with global networks, Open Systems focuses on providing robust security and network solutions. The key aspect of their service includes a customer portal for service management, emphasizing the importance of authentication and identity management. This portal serves several thousand users, necessitating a strong authentication solution. Open Systems has effectively addressed their authentication requirements by choosing ZITADEL, a decision influenced by its capabilities and advantages over notable solutions like Auth0 and Microsoft AD (currently referred to as Entra ID).
We had an insightful discussion with Simon Stäheli, product owner and manager for the authentication platform team at Open Systems, about how they leverage ZITADEL for their authentication needs.
Open Systems Managed Secure Access Service Edge (SASE)
The Open Systems Managed SASE solution addresses the critical challenges that businesses face today, especially in enabling secure and efficient access for a globally distributed workforce and leveraging cloud capabilities for business empowerment, all while minimizing costs and risks.
Features of Open Systems Managed SASE:
- Comprehensive Framework: The Managed SASE solution unifies essential components like Software-Defined Wide-Area Network (SD-WAN), Firewall, Secure Web Gateway(SWG), Cloud Access Security Broker (CASB), and Zero Trust Network Access(ZTNA) into a single framework. This integration facilitates secure connectivity across cloud and hybrid environments, simplifying network and security management.
- Unified Data Platform: A centralized data platform underpins Open Systems Managed SASE. This unified approach allows for consistent policy enforcement across global networks. Enhanced with predictive analytics, this platform proactively identifies potential issues.
- Customer Portal: The solution is delivered as a 24×7 managed service, offering an easy-to-use customer portal for visibility and control. This service model includes onboarding, unlimited support, and lifecycle management.
The Open Systems Managed SASE stands out for its ability to facilitate seamless work from anywhere, integrating a cloud-delivered network and security architecture that efficiently allocates resources, and eliminates the need for traditional network components and VPNs. It incorporates Zero Trust principles for secure access to cloud resources.
Customer Focus and Differentiation at Open Systems
Open Systems mainly caters to large-scale organizations with an extensive global presence, often including companies with over 20 branches and exceeding 1,000 employees. This client base typically comprises sectors like insurance, banking, and major international organizations. The company's specialty lies in building and managing global networks, efficiently interconnecting numerous sites—some clients have over 300 locations.
A key distinction of Open Systems is their customer portal, which goes beyond typical service offerings. The portal provides direct access to engineers for issue resolution or consultancy, enabling immediate and expert-level interaction. This approach contrasts with the common industry practice of multi-level support structures, where initial responses often come from first-level support. The customer experience at Open Systems is also defined by a longstanding commitment to self-provisioning. While this approach is becoming more common in the industry, Open Systems has been integrating it into their services for quite some time.
Their service offerings combine traditional and modern solutions. This hybrid approach allows clients to choose between physical appliances ('old-world' solutions) and cloud-native services ('new-world' solutions) depending on their specific location needs. Such flexibility in service offerings is relatively rare among their competitors, who typically specialize in either traditional or cloud-based solutions.
Integrating Open Systems' services into a client's network includes integrating critical network infrastructure components like WANs, firewalls, web proxies, and email security, creating network schemas, defining policies, and configuring and implementing these policies.
The Customer Portal
The Customer Portal of the Managed SASE offering is a tool designed for managing the SASE services.
Figure 1 - The Open Systems Customer Portal
Key Features and Functions
- Real-Time Insights and Analytics: The portal provides a comprehensive overview of network and security postures, offering real-time reports, tools, and trend analysis.
- Collaboration and Transparency: It acts as a collaborative platform, sharing technical data between clients and Open Systems engineers. Users can view service statuses, analyze network performance, and observe current threats, mirroring the visibility available to engineers. The integrated ticketing system offers detailed configuration views and operational metrics.
- Audit and Compliance: An embedded audit trail in the portal ensures that every change is documented, enhancing transparency and compliance.
- Network Health Monitoring: The portal facilitates detailed mapping of network connections and health, enabling users to prioritize and address critical issues promptly.
The Problem
Open Systems faced substantial challenges in identity and access management, primarily stemming from the need to modernize their authentication systems, thereby reducing technical debt, and effectively serving a diverse customer base. With over 30 years in the industry and a business model more than two decades old, the company had historically relied on legacy systems, including a self-developed authentication solution based on RADIUS.
The primary issue was the lack of an identity management solution that could seamlessly interface with the identity providers (IdPs) used by their 200 customers. Given that the majority of these customers used Entra ID for account management, with others utilizing platforms like Auth0 or Okta, it was important for Open Systems to adopt a system compatible with these varied third-party IdPs. This need for compatibility and seamless integration was pivotal in their search for a new solution.
Open Systems required a solution that offered the flexibility of self-hosting while ensuring robust support and ongoing development. This requirement ruled out solely cloud-based solutions and self-hosted, open-source options that lacked substantial backing and support.
The Solution
ZITADEL emerged as the chosen solution for Open Systems after they evaluated various options, including well-known services like Auth0 and Keycloak. The decision leaned towards ZITADEL due to its alignment with Open Systems' specific technical and operational requirements, and the limitations encountered with other cloud services. Interestingly, their discovery of ZITADEL through social media interactions presented a solution that closely matched their specific needs.
The primary factors that made ZITADEL an appealing choice for Open Systems are:
-
Cloud-Native Design: ZITADEL's architecture is inherently cloud-native, built to operate efficiently in Kubernetes environments. This modern approach to product design was crucial, especially compared to competitors whose products were not developed with a cloud-native focus.
-
Integration with Third-Party IdPs: A crucial requirement for Open Systems was the ability to integrate seamlessly with various third-party identity providers (IdPs) used by their clients. ZITADEL's provision of IdP templates for easy identity brokering or federation with these third-party IdPs was a key feature that met Open Systems’ needs.
-
Self-Hosting with Support: Open Systems valued the ability to self-host the identity management solution while still receiving robust support. ZITADEL offered this balance, providing a self-hosted solution with a solid support model—a combination that was lacking in purely cloud-based solutions or open-source products without substantial backing.
-
Rapid Development Cycle: ZITADEL's development life cycle stood out, with frequent releases (every two weeks) allowing for quick bug fixes and feature updates. This agility was a significant improvement over previous experiences where updates and new feature implementations were much slower.
Solution Architecture and Deployment
The primary application of ZITADEL within Open Systems is centered around their customer portal, where it serves to authenticate users accessing the SASE services. The portal application is designed with a frontend built in Typescript and a backend developed using Java. Currently, the utilization of ZITADEL is predominantly by the administrators or IT teams of Open Systems' clients. For these users, the interaction with ZITADEL occurs during essential processes such as logging in or resetting passwords within the customer portal. Internally, ZITADEL functions as the Identity Provider (IdP) for Open Systems, employing the best practices of the OpenID Connect (OIDC) standard for authentication. The system currently utilizes opaque tokens for security purposes, but they are considering a transition to JSON Web Tokens (JWT) soon.
In terms of configuration within ZITADEL, Open Systems makes use of a single instance that includes all their customers. These customers, amounting to about 200, are each represented as separate organizations within ZITADEL, with the number of IT administrators per organization ranging from 3 to 1000. The system uses ZITADEL's custom claims and action features to import data from third-party IdPs, including essential information like contact details, job titles, and roles. This data is then efficiently distributed to other products, ensuring streamlined and consistent information management across the board.
To access the customer portal via third-party logins, Open Systems has configured and managed the IdP federation between their clients' identity providers and ZITADEL. A majority of their clients, around 80%, use Microsoft's Entra ID for internal account management.
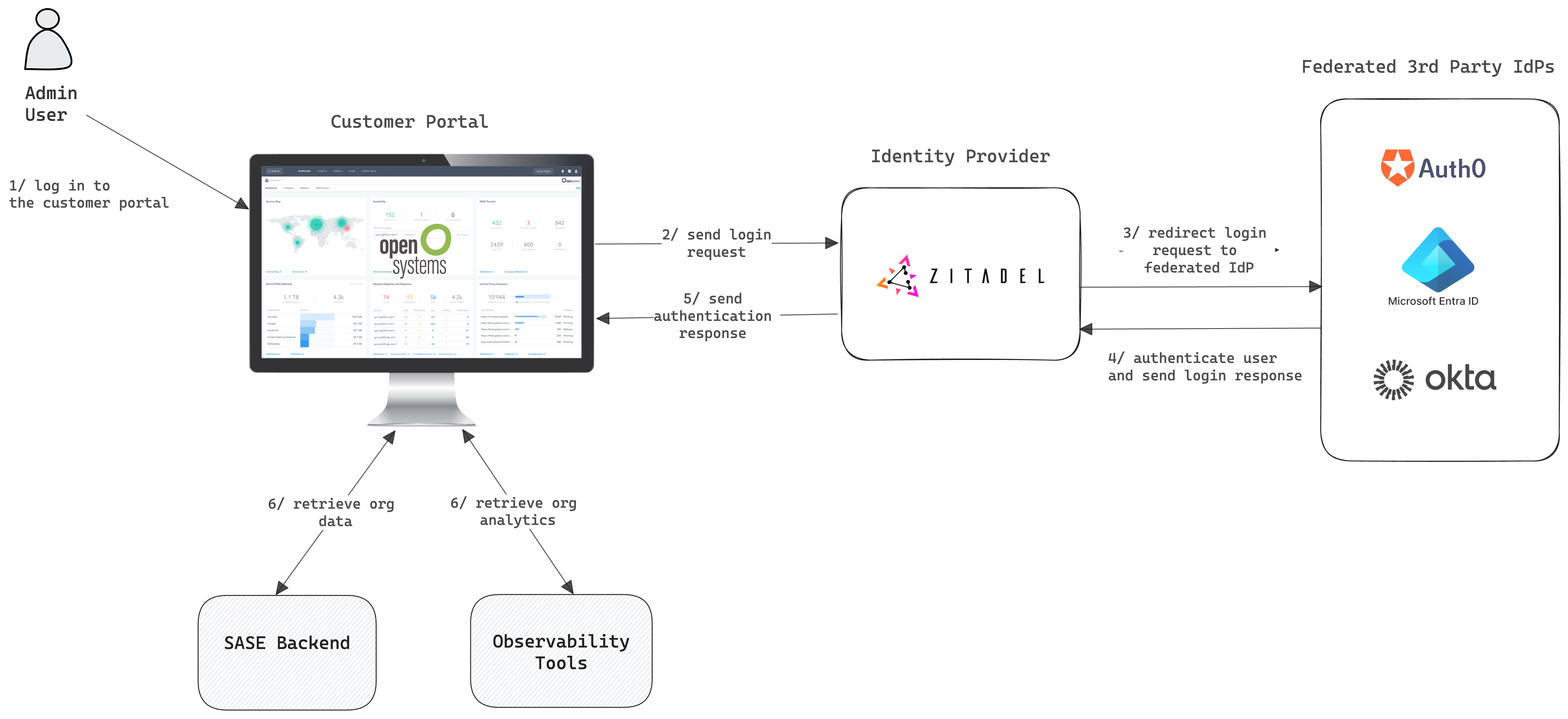
Figure 2 -User Identity and Access Management with ZITADEL
Open Systems' decision to self-host, rather than use a cloud service provider, is driven by a combination of compliance requirements and the need for operational control. For example, working with clients in the finance sector imposes specific contractual obligations that necessitate a higher degree of control over how and where data is processed and stored.
When a company like Open Systems considers using a cloud or Software as a Service (SaaS) provider, this external provider becomes a subprocessor. They would be processing data on behalf of Open Systems (who is the primary data processor). Adding a new subprocessor in such a regulated environment is not a simple task—it often involves a thorough vetting process to ensure compliance with various data protection laws and industry-specific regulations. This process can be time-consuming, often taking several months, due to the need for careful review, risk assessments, and possibly contract negotiations to ensure all compliance requirements are met.
Therefore, by opting to self-host, Open Systems avoids the complexities and delays associated with adding a new subprocessor. Self-hosting ZITADEL gave them the flexibility to fulfill that requirement, and they decided to integrate it into their existing Kubernetes cluster.
The core of their deployment is a mid-sized Kubernetes cluster, which includes various backend systems of the SASE, the customer portal, and observability tools. They make use of the ZITADEL Terraform provider to manage ZITADEL resources, which allows them to efficiently automate and manage ZITADEL configurations, ensuring streamlined deployment and consistency across their cloud environments.
Product Experience, Challenges, and Support
Efficiency in Authentication
Simon highlighted that the switch to ZITADEL has greatly simplified their process of configuring and deploying authentication mechanisms for each customer. This improvement is significant compared to their previous system, which relied on managing local accounts and using older protocols like RADIUS and LDAP. With ZITADEL, the process of setting up and integrating authentication services for a new customer – including configuring identity providers, user access, and security policies – is now notably quicker, typically completed in about 15 minutes. Previously, this setup process could take up to 24 hours, which required deploying a host into the customer's network followed by the configuration of RADIUS and LDAP. This showcases the efficiency benefits of a modern IdP system.
Challenges
Open Systems encountered several challenges, primarily when migrating to ZITADEL. Simon highlighted that the most significant hurdle was updating the existing username patterns and naming conventions to conform to ZITADEL’s system. Given the diversity and complexity of their user base, this task was far from trivial. Open Systems had to account for numerous unique cases and intricacies inherent in their legacy system, making the transition to ZITADEL somewhat challenging.
Flexible Feature Roadmap
Despite this challenge, ZITADEL's flexibility, particularly in introducing features to its frequent release cycle, was key in managing Open Systems' transition effectively. He noted that while about 90% of their required features were already in ZITADEL, for the remaining 10% that needed customization, Open Systems worked closely with the ZITADEL team. This collaboration facilitated the timely introduction of new features into ZITADEL’s existing release cycle, effectively meeting Open Systems' specific needs.
Consultancy and Support
According to Simon, a key aspect of the implementation process was the consultancy and support provided by ZITADEL, including the valuable assistance of a dedicated Technical Account Manager (TAM). This professional guidance went beyond just the technical features of the product; it also covered broader aspects of the transition process. The involvement of the TAM was particularly beneficial in aligning Open Systems' future goals with ZITADEL's capabilities, offering insights into potential opportunities and solutions.
Future Plans
Open Systems is still in the process of migrating to ZITADEL, with their immediate focus on tracking the transition of users from their old authentication platform to ZITADEL. Looking ahead, they are contemplating broader applications of ZITADEL within their operations.
One of the key plans under consideration is the extension of ZITADEL’s capabilities to authenticate end users, especially for client VPN and Zero Trust network services. Currently, ZITADEL's use is predominantly by the IT administrators of their clients, but extending its application to end users would mark a considerable enhancement in their service offerings.
Testimonials

"Choosing ZITADEL was a key decision for us at Open Systems, particularly for its straightforward integration with various third-party identity providers used by our client base. ZITADEL's cloud-native approach and rapid development cycle aligned perfectly with our needs. This, coupled with the ability to self-host and receive excellent support, made ZITADEL stand out as the best choice for our modern authentication requirements."
-Simon Stäheli, Product Owner/Manager, Open Systems