Smishing - How to Recognize Dangerous Text Messages

Marketing
In the 21st century, a significant share of our conversations is held virtually, via text messages. Not only does this fact apply to interpersonal conversations between acquaintances or friends, but also service-related negotiations such as parcel deliveries, newsletter subscriptions, or even payment requests. Due to the normalization of these sorts of messages, people tend to be less hesitant when clicking on links that come from a seemingly trusted sender. A serious problem arises, however, when the attached URL redirects you to a malicious site. In this article, I will discuss the phenomenon of smishing and how to protect yourself from falling victim to it.
What is smishing?
The word “smishing” is derived from a combination of “SMS” and “phishing”. “Phishing” describes the phenomenon of being deceived into giving sensitive information to a disguised cybercriminal and “SMS” indicates that the deception is carried out via text messaging. Smishing is therefore essentially a newer breed of the infamous spam emails, however, due to the perceived intimacy of a personal text message, SMS scams have a higher chance of going unnoticed.
To further take advantage of your confidence in text message safety, attackers tend to assume the identity of well-known companies people are used to receiving legitimate messages from, such as DHL, Netflix, or Apple. Smishing text messages usually depict a situation that due to their urgency, are known to grab the victim’s attention, such as a package delivery notification, a purchase confirmation, or a credit card suspension notice. The ultimate “goal” of smishing is to trick unsuspecting people into giving away their personal or financial information. In many cases, simply clicking the provided link can initiate a download process of viruses or malware, which the cybercriminal can use to access all data and information stored on your phone.
The most common threats of smishing texts
Based on what we already know about this phenomenon, smishing is more than a simple prank-SMS. What some people do not realize, however, is how severe the risk of clicking a simple URL can be. Most commonly, the attacker will exploit the acquired data for one or more of the following purposes:
1. Stolen money
The most obvious reason a criminal would want to access your online information is to defraud you out of money: The attached link is therefore often used to intercept a one-time passcode (OTP) most banks use for step-up authentication. Alternatively, they might simply send their unsuspecting victims a warning about an unpaid bill in favor of a fake recipient. Sadly, many attackers found success in this “business”: The median of the loss reported by complainants was $800.
2. Identity Theft
Theft does not exclusively happen to tangible objects; it can also happen to a person’s entire identity. Some scammers use the accessed data to claim the identity of their victim, for various diverging causes apart from stealing money, such as filing phony health insurance claims, committing tax fraud, or even reselling your data to other criminals.
3. Installed Viruses
Another threat smishing poses is the installment of unsolicited malware. The message might encourage you to download a seemingly trusted app, which could be used to collect sensitive data from your phone, such as credit card details stored in other apps. Additionally, a phone infected with malware or viruses can become completely unusable.
Pegasus: A real life smishing example
To showcase just how dangerous the consequences of smishing can be, we are taking a look at the real-life example of the “pegasus incident”. Pegasus is a spyware that can be installed on any kind of smartphone device, intending to harvest its data from apps. While the software was intended to be used to investigate potential terrorists and criminals, multiple cases of its misuse to surveil anti-regime activists, journalists, and political leaders have been reported.
As software capable of zero-click exploit, Pegasus requires no user interaction to operate: As an example, the spyware could be covertly installed on the phone of a technology lead at Polygon, by taking advantage of a previously unknown security vulnerability in Apple’s iMessage. The Pegasus infection link was disguised as a boarding pass link for a Swiss International Air Lines flight the victim had purchased. As a result of a simple click on the URL, the spyware was granted unlimited access to every information stored on the iPhone.
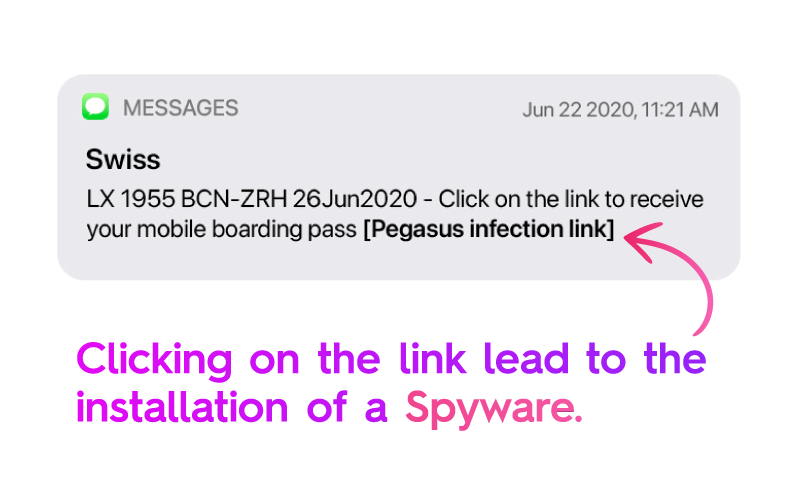
While this incident of a fraudulent boarding pass link would likely fly under the radar for many, luckily, more amateurish smishing attempts targeted at civilians are easier to identify. In the next chapter, we discuss some common signs of a potential smishing attempt.
Signs that you are getting “Smished”
To protect yourself from smishing, it is essential to be able to recognize the threat coming your way. Luckily, there are some signs to look out for, when receiving a suspicious text message. If the text is guilty of at least one of these common signs of smishing, that is a warning signal that you need to take measures to protect yourself:
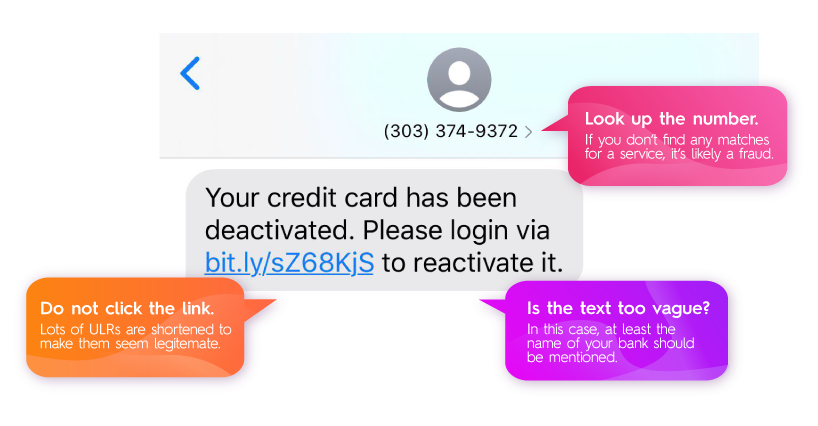
- The message is asking you to click on an URL with a domain that does not correspond to the company name. Furthermore, shortened URLs (f.e. starting with bit.ly, cutt.ly, and shorturl.at) are generally not trustworthy in the context of SMS messaging.
- The message is very generic – Legitimate senders generally include the package number, your bank’s name, or your name/nickname, depending on the context.
- The message contains spelling- or grammatical errors - Texts from service providers are usually automated, so the possibility of a typo would be extremely low.
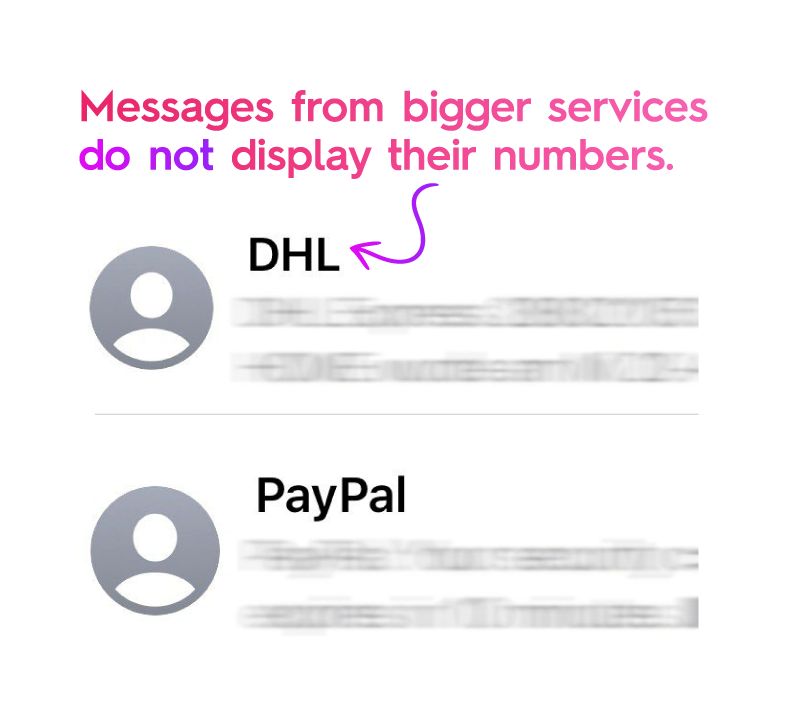
- The number of the sender and that of the service provider they claim to be, do not match. Moreover, when you receive a message from bigger service providers, (f.e. banks, post offices, or delivery services) they will mostly have their company names displayed instead of their numbers.
How can you protect yourself?
Whether you already received an illegitimate message or not, smishing can happen to everyone. However, there are plenty of measures you can take to protect your data; if you have received a suspicious message, keep these simple tips in mind to avoid falling prey to text message fraud:
- Do not open the attached link
- Replying or calling them is counterproductive – Doing so confirms that your number is in use, making you a potential target for more attacks
- Never share any of your data (passwords, address, etc.) via text
- Limit sharing your phone number on social media to decrease the number of potential scammers getting their hands on it
- Block the number and/or report the scammer to your country’s Trade or Communications Commission or the police
- When in doubt, ask the service to confirm the delivery of the message in question. However, make sure to do so via the contact information you can find on their official website; do not call the number that sent the message.
- Enable Multifactor Authentication to prevent unwanted logins to your account.