Our Vision for ZITADEL

Founder and CEO
What is ZITADEL
ZITADEL is a "Cloud Native Identity and Access Management" solution built for the cloud era. ZITADEL uses a modern software stack consisting of Golang, Angular and CockroachDB as sole storage and follows an event sourced pattern.
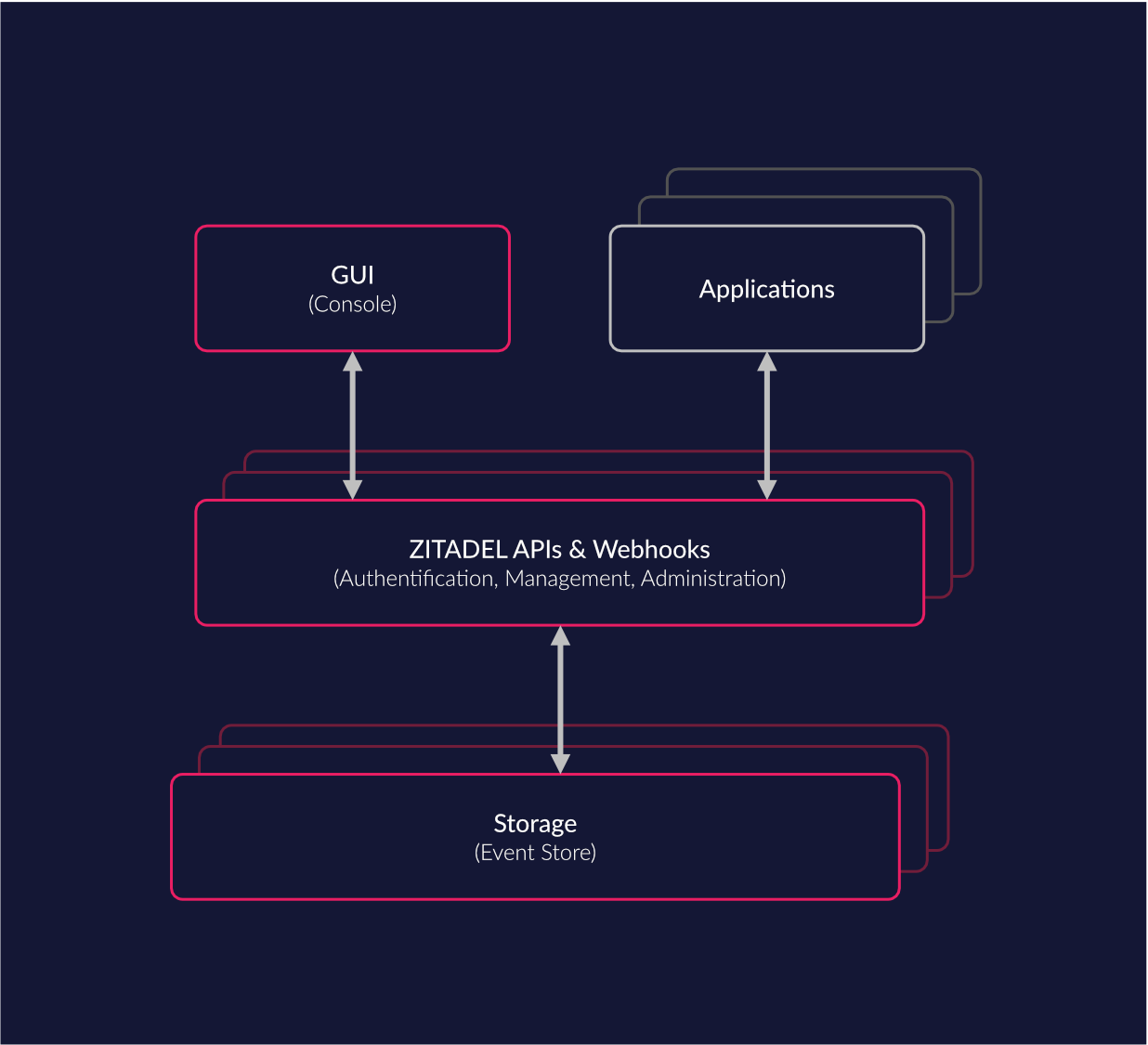
We built ZITADEL not only with the vision of becoming a great open source project but also as a superb platform to support developers building their applications, without need to handle secure user login and account management themselves. By platform we mean a system where multiple parties can integrate custom use-cases for digital identities on top of solid core features. To enable easy integration into your business case, nearly all functions can be accessed via an API. With this we achieve a proper separation of concern and don’t need to integrate custom code within our codebase.
What features does the platform provide?
Single-Sign-On / Single-Sign-Out
Use the convenience of a single sign-on (SSO) solution to login with every possible service. ZITADEL enables SSO via standard protocols such as OpenID Connect. Services that cannot be directly integrated can be integrated with identity aware proxy or web application firewalls (WAF). Session management is therefore handled identity-based within identity access management (IAM) and no longer solely in the application. In addition, third-party cloud applications can be easily connected in this way.
Passwordless / Multi-factor authentication
Although you can use password policies and a range of 2FA and MFA options with ZITADEL to reduce security risks during login, even complex passwords can be compromised, for example through phishing, while user experience suffers greatly from cumbersome passwords and looking up secrets. ZITADEL allows your users to configure passwordless Login based on WebAuthN & CTAP (FIDO2). Passwordless works on all browsers and platforms, requires only one gesture such as FaceID, Fingerprint or PIN, and is phishing resistant through public-key cryptography.
Identity Brokering
Identity Brokering enables you and your customers to reuse existing identity providers. For example, if you rely on Microsoft's AzureAD for identity management, then you can use ZITADEL’s Identity Brokering feature to link your existing account from AzureAD to your ZITADEL account. The benefits of this feature is that a user can link multiple external identities to it’s ZITADEL identity. Moreover, Identity brokering enables you to grant roles to the brokered users and disable their accounts if the need arises.
Role Based Access Control
To manage the users' access to projects connected to ZITADEL it supports the use of Role Based Access Control (RBAC). RBAC allows you to design a sophisticated role catalog for each of your projects and granting granular access to users. To integrate these roles into your application you can simply integrate them by utilizing well established protocols like OAuth 2.0 and OpenID Connect. ZITADEL also lets you configure whether you want to assert the roles into access tokens or simply rely on the userfinot and introspect endpoints.
Delegation
ZITADEL allows you to “delegate” roles of your projects to other organizations. With this feature you can enable other organizations to self-manage their users and the effective role they possess of your project. For example if you create an eCommerce service and you want to delegate the management of a specific tenant to your customer you could easily create a role “tenant owner” which you could grant to the customers organization.
Strong Audit Trail
Traceability is an important basis for an IAM, which is why ZITADEL offers you an audit trail of all operations of an account and its actions. The audit trail is firmly anchored in the ZITADEL because the internal data model does not save it separately but derives it from an event stream. You have the ability to export the audit trail for advanced analytics or storage to other systems.
API’s
To make for a great IAM platform ZITADEL provides close to all of its functionalities as APIs. Most important for integrators is the Management API: It provides all features to manage Organisations, Users, Projects for a certain Organisation. Furthermore OpenID Connect 1.0 and OAuth 2.0 are available to integrate your projects Authentication and Authorization requirements. Two more API’s that are available are the IAM and Auth API. The IAM API can be used to configure the whole IAM, this is mostly used in self-deployed (ZITADEL Enterprise) or managed deployments (ZITADEL Enterprise Cloud). Authentication and user information can be accessed through the Authentication API.
How ZITADEL compares to other solutions
Let’s compare ZITADEL to other well established solutions with a strong focus towards Developers or Open Source.
Auth0
Auth0 is a great IAM platform to integrate with your projects. Their developer support is exceptional and the API is well thought through. However we find that some things are not ideal, such as pricing, Closed Source, Audit Trail and improper on-premise support.
Where Auth0 is more mature
- More Protocols Supported (e.g SAML 2.0)
- Customization Support (Rules, UI, and so on)
- More stable API’s
- A lot of documentations and howtos
Where ZITADEL excels
- Runs on any cloud provider and on-premise (Cloud-Native)
- Built for multi-tenancy and self-service delegation
- Better Audit Capabilities
- Tiered pricing depending on SLA and non-security requirements
Keycloak
Keycloak is a mature IAM System with a lot of great features. It is also Open Source with an Apache 2.0 license (like ZITADEL) and has a well established reputation.
Where Keycloak is more mature
- More Protocols Supported (e.g SAML 2.0)
- Better customization (Private Labelling)
- Big Community
Where ZITADEL excels
- Built for Cloud-Native
- Better Audit Capabilities
- Multi- Cloud / Datacenter Support
- Less Resource Requirements
Platform ecosystem
We think ZITADEL is a great platform for third parties (and ourselves) to integrate business requirements on a robust platform and enable people to build business value instead of focusing on secure Authentication and Authorization implementations.
In this chapter we will provide some use-case where ZITADEL can help you excel.
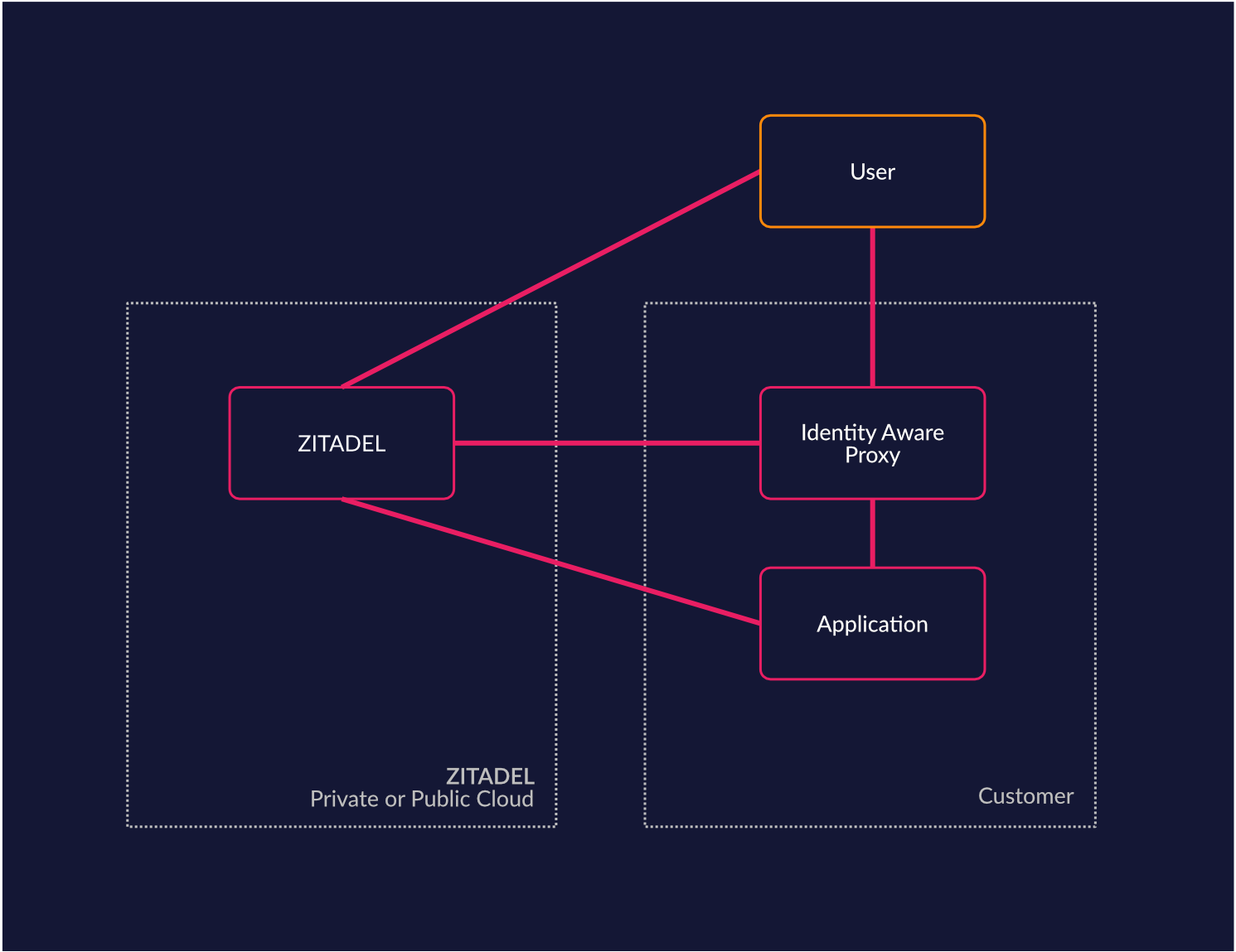
Network Integration, Identity Aware Proxy (Zero Trust)
If you use ZITADEL, you can easily integrate your network equipment (Reverse Proxy / WAF) with ZITADEL for things like secure authentication. For example you might want to enforce multi-factor authentication when a user is not at a trusted site. Your identity aware proxy could easily (re)authenticate the user when someone leaves a trusted site by prompting for a more secure authentication method. ZITADEL will then proceed with ensuring the more secure method.
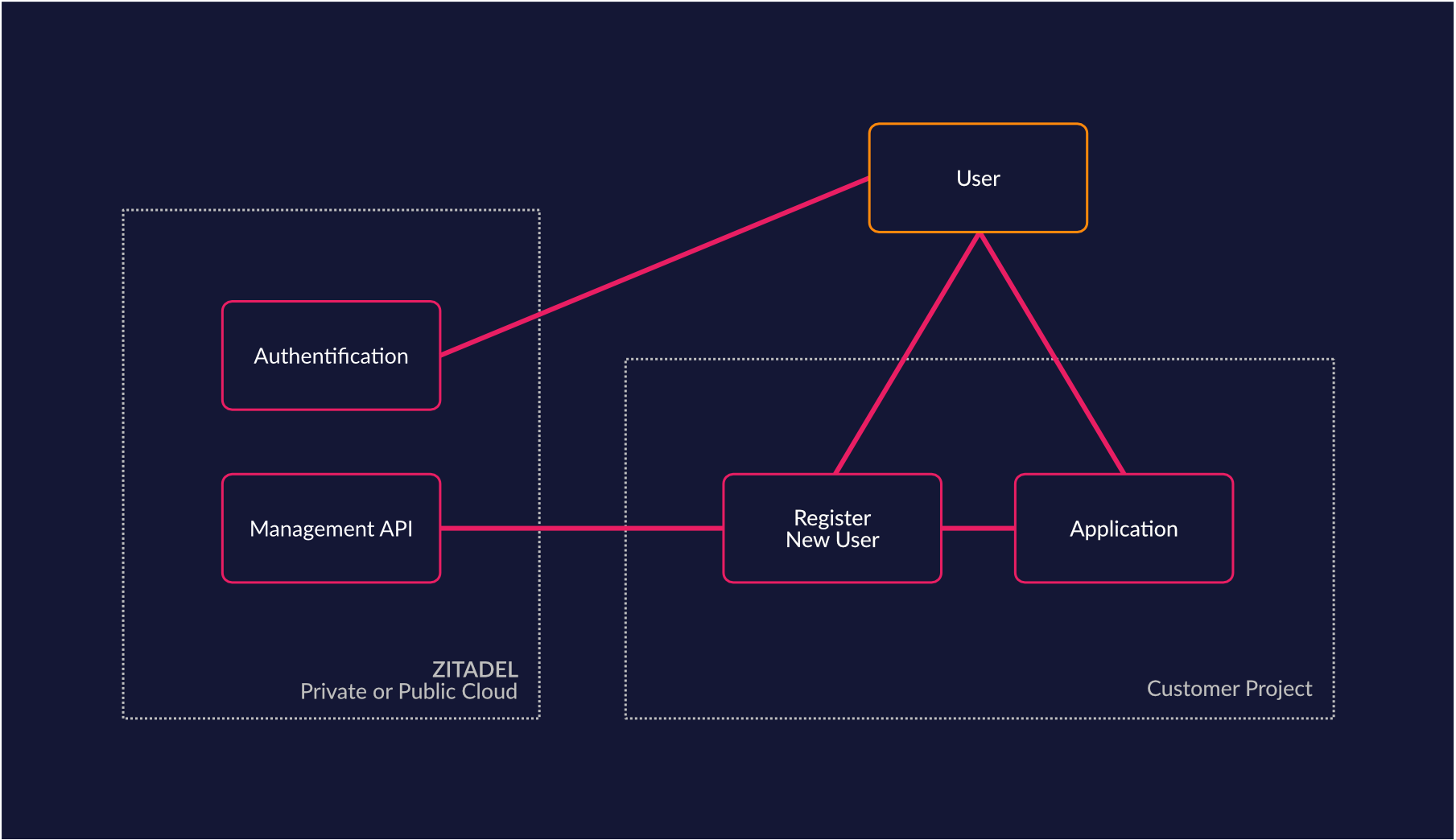
Custom User Registration
If you have special requirements for your user registration (KYC, eHealth, eGovernment), you can easily rely on ZITADEL to build your own registration process by integrating your project with the ZITADEL management API. By building your integration you can reuse existing features to manage identities from our platform and combine them with your unique registration requirements.
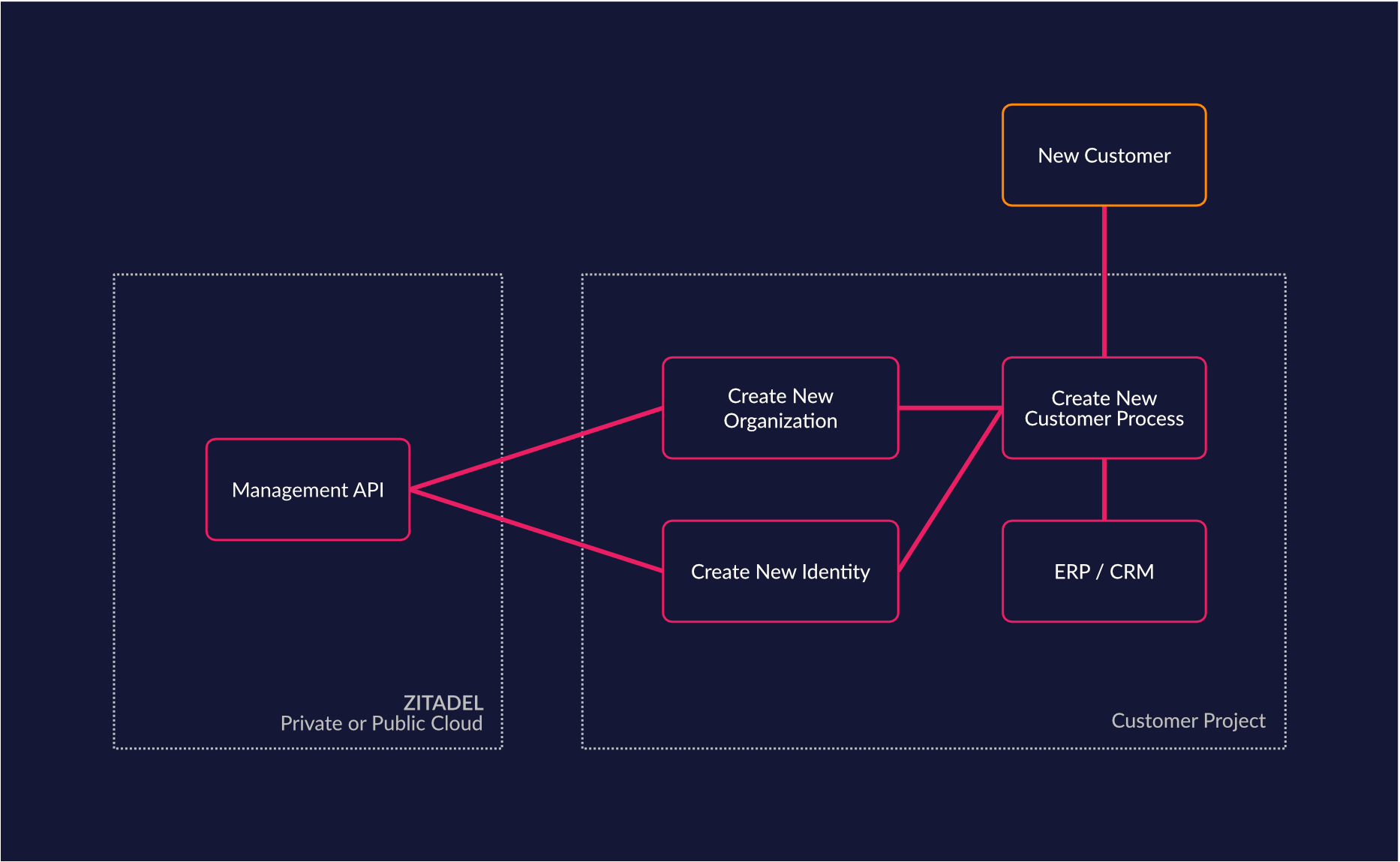
Business Process integration (SaaS, MSP)
When building a service for your customers you may want to integrate your access management process into your order management. For example, if you have a SaaS solution where a customer can set up a new tenant by himself, you can delegate the ability to manage their own users directly to the customers. This may greatly reduce support requests from customers to setup users and access rights. With ZITADELs unique self-service capabilities it's even possible to let your customers register their existing identity solutions on their own.
Custom Lifecycle Requirements (HR Systems)
If your business already has some systems in place that are responsible for managing your Human Resources or Business Processes, you can easily integrate them with ZITADEL. For example, if you have an HR System which already manages the employee lifecycle, you can use ZITADEL to handle the users identity, but leave the business process in the proper domain - within your HR System. With this approach you can reuse your employee process (joiner, mover, leaver) without leaking business processes into the IAM platform. We think that an IAM platform should not be the component in your architecture which executes business processes. Because if you implement business processes from domains like HR, CRM into the IAM Domain, you will eventually create a IAM which can not be easily replaced even if you use standard interfaces.
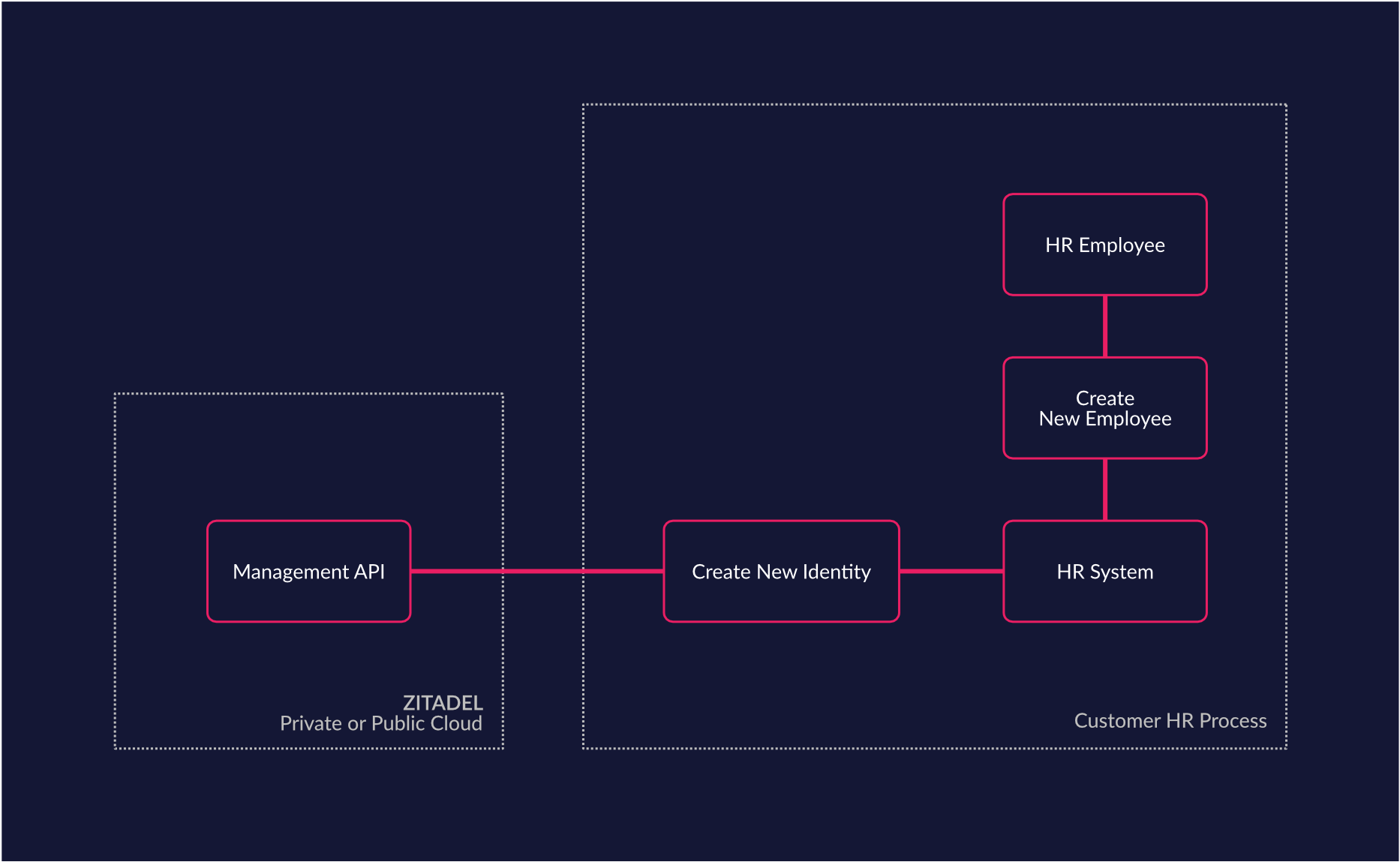
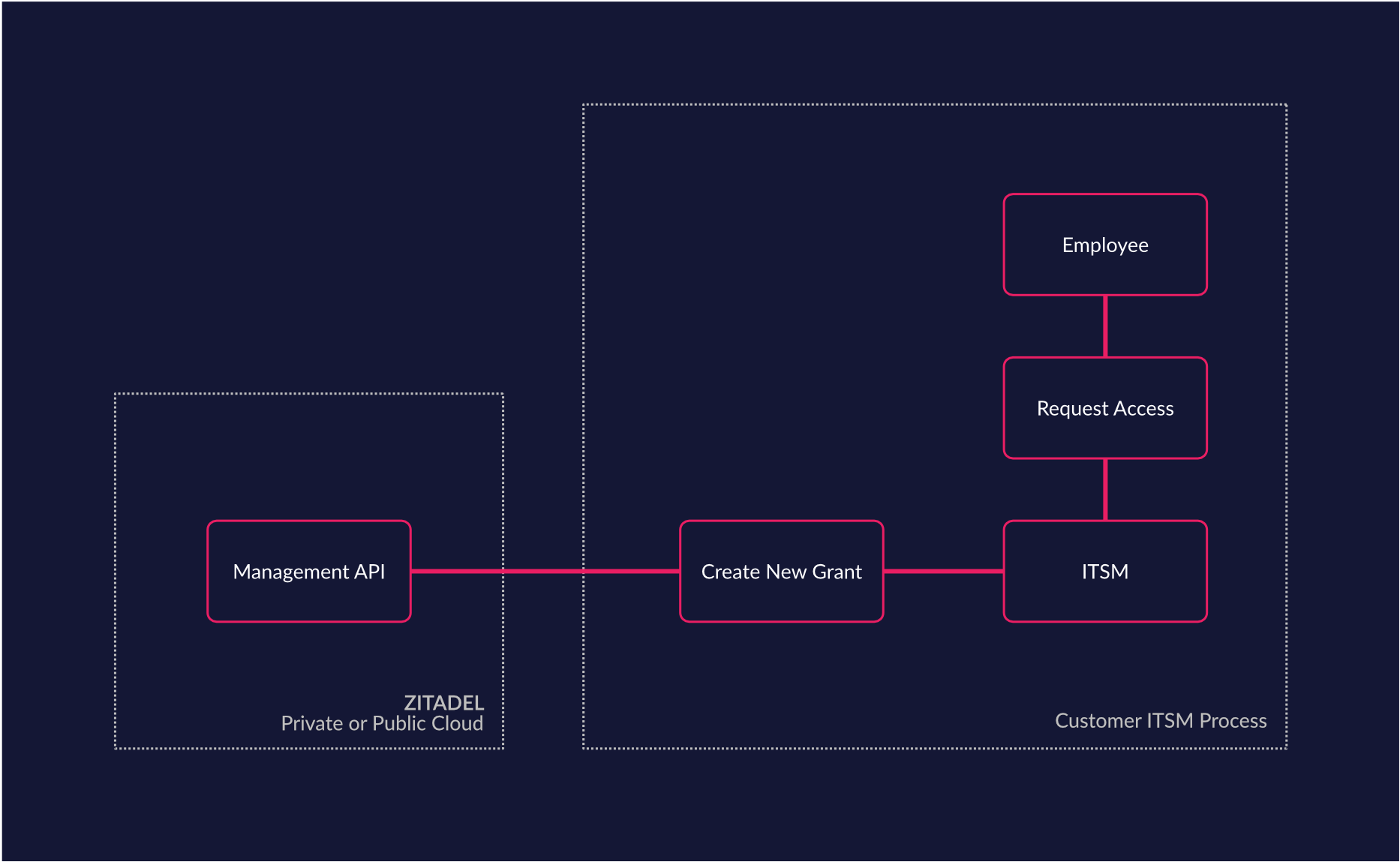
Custom Access Management Requirements (ITSM)
Quite a lot of companies already rely on IT service management (ITSM) systems like ServiceNow to handle their fulfillment processing (access request, account reset, etc.). In such cases it makes sense to leave the IT service workflows in the tool that is optimized for business processes and integrate ZITADEL as an access Management system. Such an integration allows you to fully integrate your IT services process. For example the account of a user could be locked from the ZITADEL management interface and the unlock process could be built as a workflowinto your ITSM. This helps you build and maintain lean processes with low implementation and change cost.
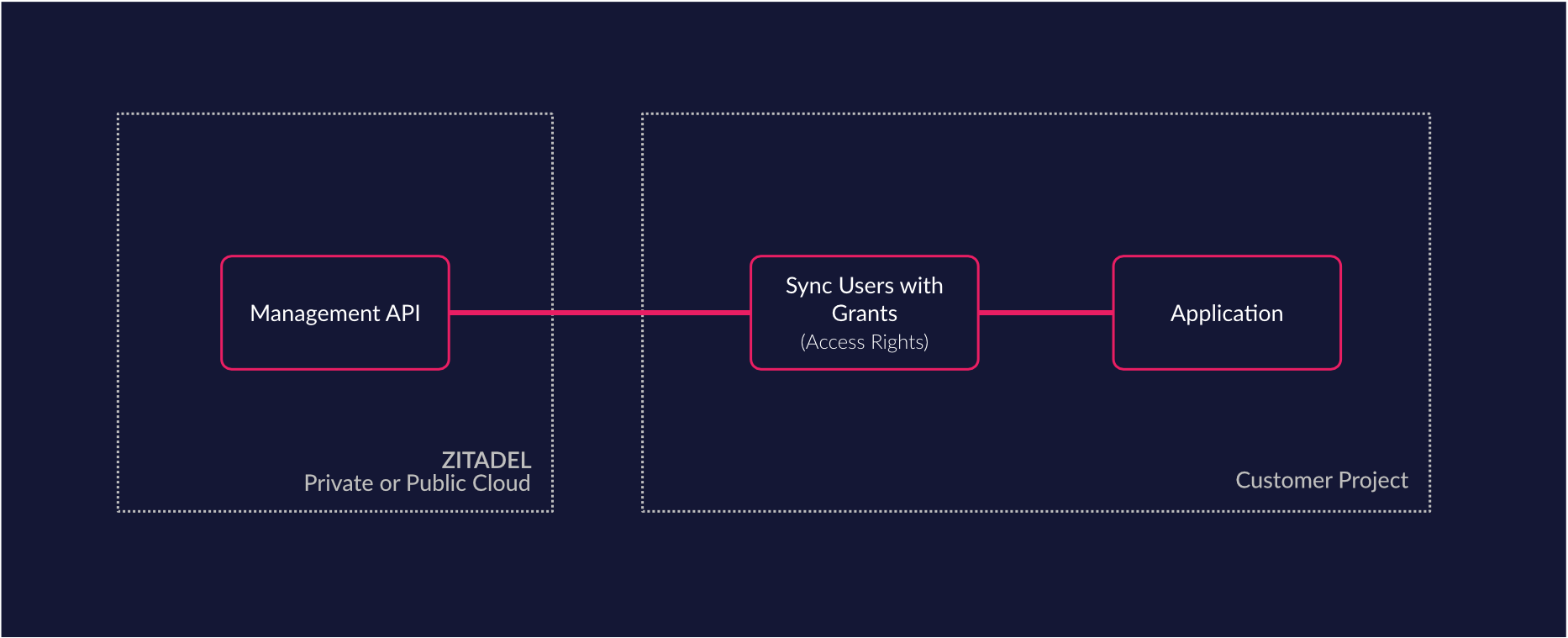
Custom Sync of data (Sync any data source)
ZITADEL’s APIs enable you to manipulate and synchronize data from any system. For example, you can sync your applications users list with ZITADEL and even change user data from within your application. All of this without relying on ZITADEL’s management interface (console). If you care about a deep integration of the user experience this is a great way to enable your project. Furthermore some applications require an up-to-date list of all users for their processes. These applications can easily query ZITADEL for said data.
How people use ZITADEL
Most of the time, our customers choose to use our platform's core features like Authentication and Authorization by utilizing protocols like OpenID Connect and OAuth 2.0. But in some cases they integrate even deeper with our API to improve their time to market, operational efficiency and security. Read about what people have already built in this chapter.
Integration Case - Task Management
One of our customers built a SaaS Service for tracing pandemics. Right now this solution is used to trace the SARS-CoV-2 spread in some parts of Switzerland. The special integration in this case is that the workers who use the solution need to be able to assign work to entitled people. To accomplish this, the software utilizes a service account to query ZITADELs management API in a scheduled manner and syncs this list into their database. With this they are able to provide an up-to-date list of all entitled users. Further ZITADEL enables their development by providing an IAM as a Service model, where CAOS takes care of all operation security questions.
Kudos to JOSHMARTIN for helping us through the pandemic by providing the government with a progressiv application that really enables the tracing effort.
Used Features
- Authentication (incl. MFA, Passwordless)
- Authorization
- OpenID Connect / OAuth 2.0
- Management API, Query Granted Users
- Service Accounts
Tech Stack
- Elixir
- Phoenix Live View
Resources
joshmartin.ch/en/projects/kanton-st-gallen-contact-tracing/
Integration Case - eCommerce Framework
The great people of sly are building a modern microservice oriented headless eCommerce Framework called VELOX and choose ZITADEL as the solution for handling all of their authentication and authorization needs.
Kudos to sly for creating such a great and adaptive eCommerce solution!
Used Features
- Authentication incl. multi factor
- Authorization
- Single Sign On
- OpenID Connect / OAuth 2.0
- Management API
- Service Accounts
Tech Stack
- Java
Resources
velox.swiss
Integration Case - multiple ASP.net Core Projects
The Zurich located development agency called smartive utilizes ZITADEL for their projects. As they often rely on ASP.net Core to build award winning projects they wanted to improve their time to market. To integrate ZITADEL with the existing Microsoft authorization ecosystem, they implemented the .net library and open sourced it. Go checkout the library on Github.
Kudos to Christoph Bühler for implementing this!
Used Features
- Authentication (incl. MFA, Passwordless)
- Authorization
- Single Sign On
- OpenID Connect / OAuth 2.0 (incl. JWT Profile and introspect support)
- Management API
- Service Accounts
Tech Stack ASP.NET Core
Resources https://github.com/zitadel/zitadel-net
Future Enhancements (subject to change)
We will improve ZITADEL over time with new features. To give you a small hint of what we are planning to release, have a look at the following list.
- API Docs with Swagger / OpenAPI - Since creating this blog we released this feature
- Outbound Webhooks
- SCIM 2.0 API
- Expose Authentication Functions as API
- Conditional Access Rules API
If you have ideas of question feel free to engage with us on Github Discussion Board
TL; DR Why you should consider ZITADEL your goto IAM Platform
ZITADEL is a proper Open Source project, offers competitive and fair pricing, is built by an experienced team and a committed company and has a high velocity for developing new features and constantly improving security.
In short ZITADEL is the identity & access platform for your business!
Feel free to contact us on these channels
If you consider contributing we would also be happy to welcome you!