How MFA Fatigue Attacks Compromise User Security

Marketing
Have you ever made a reckless decision in a hectic situation that you later regretted? We know you did. And sadly, so do cybercriminals.
There are countless bad decisions made online every day. Whether they are made accidentally or due to being misguided, just a single wrong click can lead to devastating consequences. MFA Fatigue Attacks aim to take advantage of this irrational decision-making to deceive users into bypassing or circumventing Multi-Factor-Authentication (MFA), thus jeopardizing the security of their accounts.
This article discusses MFA Fatigue Attacks targeting MFA systems with push notifications and how we can mitigate them.
MFA with Push Notifications
Since Push Notifications are commonly used as a second factor in two-factor authentication (2FA) or multi-factor authentication (MFA) systems, you have likely already encountered this verification method. Like other Multi-Factor Authentication methods, it adds an additional layer of security to user accounts by mandating an extra verification factor in addition to the traditional username and password login approach. The popularity of Push Notification reliant MFA can generally be accredited to its relatively robust security and convenient user experience.
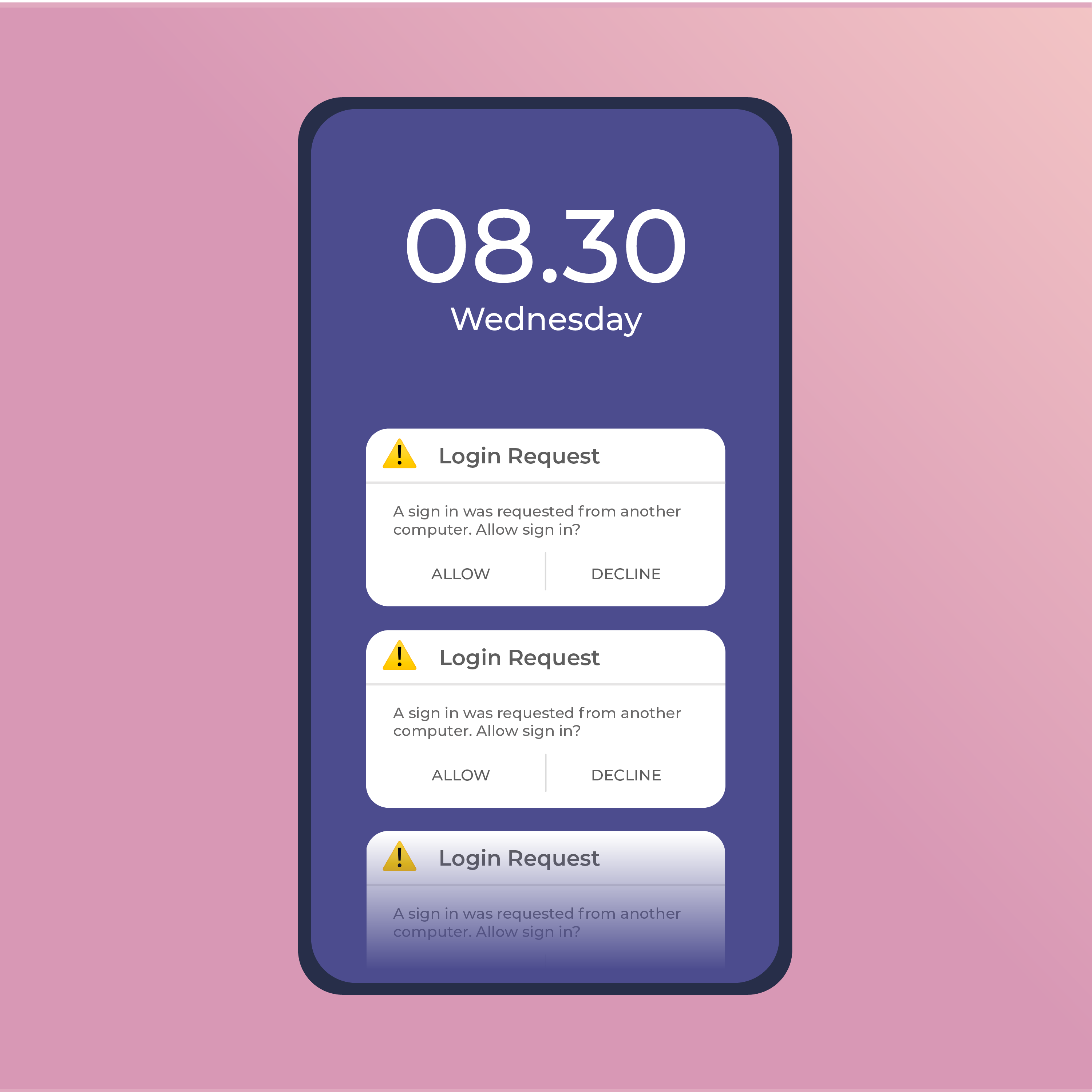
Verifying your identity with this authentication method is very simple: When attempting to log in to a service or application that has this type of MFA enabled, you receive a push notification on your registered device (such as a mobile device or tablet) instead of a code. This notification contains information about the authentication request, including the device and location. Upon reviewing these details in the authenticator app, you can allow or decline the login attempt, which helps you block malicious actors from accessing your data.
While Multi-Factor Authentication with push notifications is significantly safer than single-factor password-based login, it is not impervious to all cyberattacks. One of the most common techniques threat actors use to bypass this MFA method is an "MFA Fatigue Attack".
What are MFA Fatigue Attacks?
MFA fatigue attacks, also known as MFA exhaustion, 2FA fatigue, MFA push spam, or prompt bombing refer to a type of 2FA bypass attack that exploits the usability challenges associated with Multi-Factor Authentication using push notifications. However, instead of relying on brute force or deception techniques, 2FA fatigue attacks take advantage of the flaws in human decision-making.
If the attacker has already acquired someone's login credentials, they can initiate a login attempt, automatically sending a push notification to the victim's registered device. Should the victim deny the authentication request (as usual), the attacker simply repeats the process. The attack aims to continue sending these login requests to the user's device until they eventually give in out of frustration or by accident. Accordingly, increasing the frequency at which the user is sent MFA requests can significantly enhance the attack's success rate.
The Psychology Behind MFA Fatigue Attacks
Upon learning about the concept of MFA Fatigue Attacks and their relatively high success rate, a commonly asked question might arise: Why do some victims eventually accept the authentication request if it was clearly triggered by a malicious actor?
There are some people who even unthinkingly accept the first MFA push notification they receive, possibly as a force of habit. Surely, some might also press the wrong button by accident or perhaps think that a bug causes the spamming of the notification. The behavior of the third category of victims, who seemingly deliberately accept the approval request after it keeps on invading their devices, is rooted in a psychological phenomenon called decision fatigue.
If a machine were asked the same question repeatedly, it would always provide the same response since that is what it was pre-programmed to do. However, unlike machines, humans do not always operate rationally - especially in overwhelming situations.
When users are unwillingly prompted to decline the same MFA push notification over and over again, their sensible decision-making abilities often suffer due to their growing botheration with the repetitiveness. This phenomenon of decision fatigue increases users' likelihood of taking shortcuts or ignoring security protocols: For example, instead of declining the MFA prompt yet again, the user would begrudgingly select "Allow" to finally make it disappear. Obviously, doing so would only solve a minor inconvenience while simultaneously making way for an infinitely bigger problem: having their personal information compromised.
How to Mitigate MFA Fatigue Attacks
Change your Password
Whether or not an attack has previously been attempted on your account, consider creating a strong password to reduce the likelihood of it being guessed or cracked. Ideally, this password should include at least one uppercase letter, one number, one symbol, and a total of 9 characters.
While an MFA Fatigue Attack may be mitigated if the attacker does not know your login credentials, having to remember a long and complicated password significantly decreases the user experience.
Switch to Another MFA Method
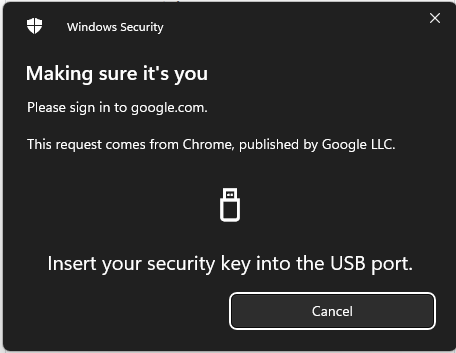
Another way to avoid falling victim to MFA fatigue attacks is to enable a different MFA login method on your account instead. We recommend switching to a FIDO U2F authentication technique whenever your platform allows it.
U2F leverages public-key cryptography, which makes it far safer and less vulnerable to 2FA bypass attacks than other MFA methods (such as One-Time Passwords (OTP)). This FIDO protocol uses security devices known as U2F tokens as the second factor. These tokens can be embodied in various form factors, such as a USB device (f.e. Yubikey), a Near Field Communication (NFC) device, or a BlueTooth LE device.
This option, akin to changing to a safer password, may temporarily solve the problem of MFA fatigue attacks. However, these MFA systems still rely on passwords as their primary authentication factors, which are highly subjectable to various attack vectors. Thus, as long as passwords are part of your login process, your account remains subject to various 2FA bypass attacks.
Fortunately, the constant evolution of security standards led to the development of safer authentication protocols that do not incorporate passwords into their systems.
Go Passwordless with Passkeys
The ultimate solution to eradicating MFA fatigue attacks is to switch to a passwordless authentication method. By eliminating passwords from their authentication process, passwordless systems are far less susceptible to cyberattacks, such as phishing, social engineering attacks, and brute-force attacks.
Passwordless protocols, such as FIDO2 (aka FIDO 2.0) passkeys, depend entirely on exchanging public-private keys between a user's device and the server that authenticates the user, thus ensuring highly secure access to all virtual identities. The risk of MFA is significantly mimized, since the FIDO request needs active initialisation on the device that raises the prompt. Therefore, another person can not initiate the verification of the second factor for the user since their device does not hold the passkeys. Furthermore, passwordless systems enable a smoother authentication experience due to their waiver of the knowledge factor.
Secure Authentication with ZITADEL
Successful 2FA bypass attempts, such as MFA fatigue attacks, can have devastating consequences. However, choosing a robust and secure authentication method can significantly reduce the chance of falling victim to a cyberattack.
With ZITADEL as your company's Identity and Access Management (IAM) solution, your end-users have a plethora of highly secure authentication methods to choose from. Furthermore, due to the platform not supporting MFA with push notifications, the chance of an MFA fatigue Attack is off the table.
To ensure that your end-users can verify their virtual identities in the safest and most convenient way possible, we highly recommend that they either set up a FIDO U2F token or a FIDO2 Passkey as their preferred authentication method.