All posts/ #security
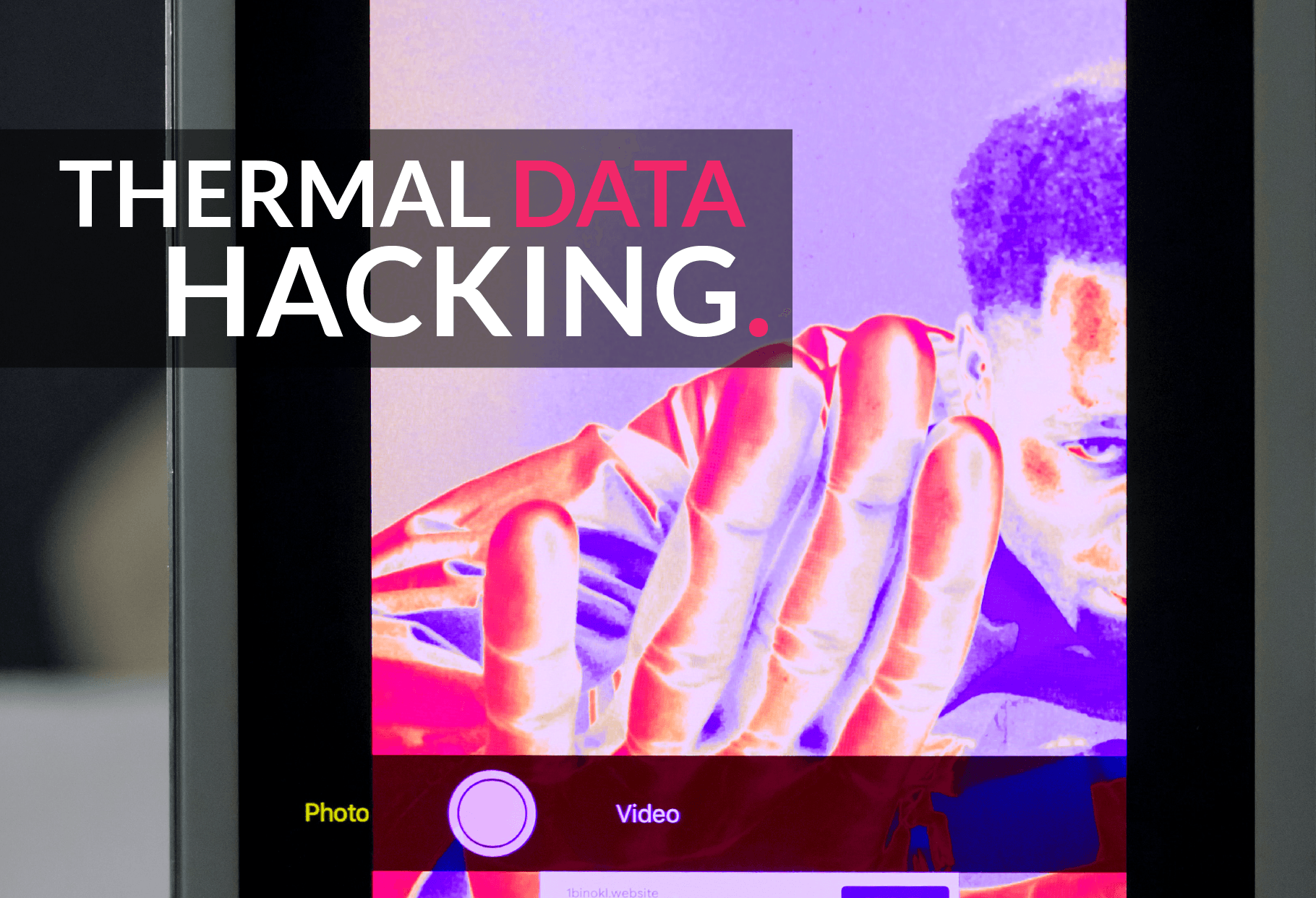
Thermal Attacks - How Heat From Fingertips Can Reveal Passwords
While you might be familiar with common hacking methods, such as phishing and malware, researchers have discovered a bizarre new alternative: Thermal Attacks.
• 7 min
How to handle silent-login in ZITADEL?
It's important to secure the myriad of connections between the devices in an IoT network and the services they communicate with. This is where IoT authentication plays its vital role. In this article, you'll learn how authentication in IoT works and how you can achieve device authentication in an IoT system.
• 3 min
How Does the Internet of Things Authentication Work?
It's important to secure the myriad of connections between the devices in an IoT network and the services they communicate with. This is where IoT authentication plays its vital role. In this article, you'll learn how authentication in IoT works and how you can achieve device authentication in an IoT system.
• 9 min
Use ZITADEL as SSO provider for self-hosting
In this tutorial, you'll learn what benefits SSO brings to the table. You'll learn how to delegate access from a self-hosted Nextcloud service to ZITADEL as an SSO provider
• 10 min
Simplify Delegated Access Management and Self-Service
Granting access is complex, and delegating it needs to be done safely. In this guide, you'll learn how to simplify delegated access management and self-service.
• 10 min
What is an Identity Broker? - Everything you need to know
Integrating multiple Identity Providers directly within applications is complex to maintain, time-consuming to set up, and hinders single sign-on of users. Luckily, this problem can be easily solved with the help of an Identity Broker.
• 4 min
Your Spellchecker Might Have Leaked Your Passwords
Whereas a seemingly innocent spellchecker might not raise any red flags, convenience and confidentiality are regrettably not always compatible online. This article explains the privacy shortcomings of Chrome’s Enhanced Spellcheck and Edge’s MS Editor and what you can do to keep your data safe.
• 4 min
Why Security Questions Are Useless And Unsafe
Discussing the shortcomings of security questions as a protection measure and what you can do to make them stronger.
• 8 min
Security Threats of Public Wi-Fi - Is It Just Fearmongering?
Although public Wi-Fi networks certainly carry some frightening risks with a lot on the line, it is evident that such attacks aren't guaranteed occurrence. So how likely is it really that one will fall victim to a malicious network?
• 9 min
Why Zero Trust is Important
Given the ever-growing prevalence of remote jobs, bring your own device (BYOD), as well as SaaS and cloud-based assets, the importance of secure and trustworthy authentication processes has significantly increased. This article explains the functionality of Zero Trust and its benefits over older security perimeters.
• 5 min
Children and Online Security: Protecting the Most Vulnerable
Given a child's natural innocence, they might not expect an ill-wisher on their favourite online platform. This article discusses the new digital threats kids are subjected to and what adults can do to keep them safe.
• 11 min
The Ultimate Guide to Choosing the Right Data Residency
This article explains the role of data residency and centers in greater detail and list the factors you might want to consider when choosing a center region.
• 8 min