Why You should Switch to Passwordless Authentication

Marketing
Whether it is your social media profile, your favorite streaming service, or your work email, the usage of passwords is the most common way people access their virtual identities. However, in recent years, a new alternative has been seeing traction in the web: passwordless authentication. Although this method would have seemed like a supernatural concept a decade or two ago, today, it is commonly praised as the future of authentication: According to the technology research firm Gartner, 60% of large and global enterprises and 90% of midsize enterprises will implement passwordless methods in more than 50% of use cases by the end of 2022.
To grant an insight into the newly found popularity of passwordless, this article will explain its concept, describe its reason for existence and elaborate upon its advantages over regular passwords.
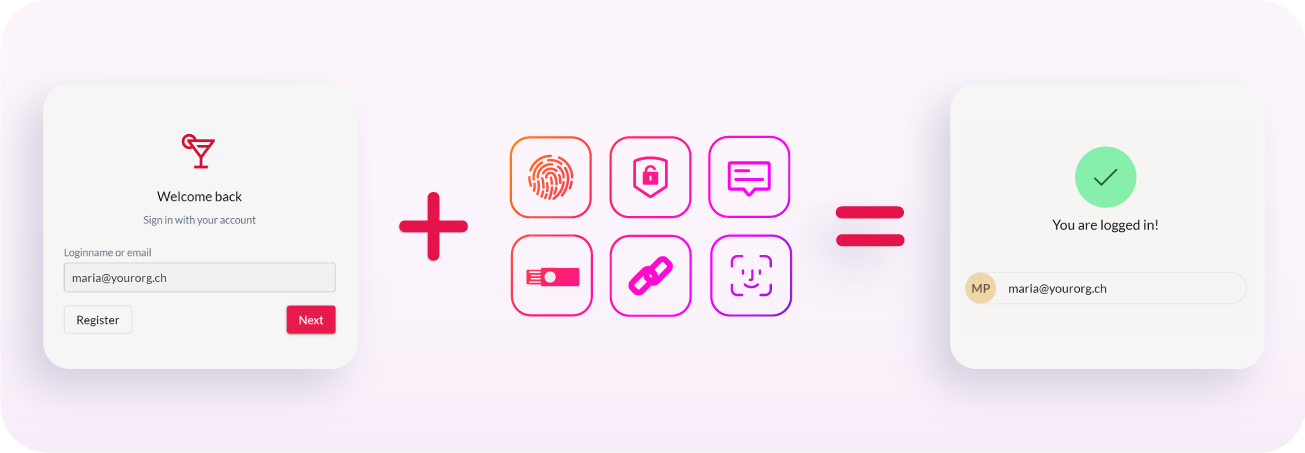
What is passwordless?
The term passwordless refers to authentication methods that confirm a user's identity without entering a password. Instead of relying soley on a knowledge factor, passwordless utilizes alternate authentication methods, ensuring a more convenient and secure way to access your virtual identities.
The most popular passwordless authentication methods include:
- Possession factors: An object, such as USB Devices (FIDO2-compliant keys), physical tokens, or your smartphone
- Biometrics: Physical traits (f.e. Fingerprint scanning or Face-ID) or other characteristics, such as voice recognition
- Magic links: A link sent to the entered email address
- One-Time-Passwords: A code sent via text message or an authentication app
- Software Tokens: A virtual possession factor granted by an authentication software
Which of these methods a platform implements, depends on their individual preferences: To ensure their users the possibility to authenticate themselves via their preferred factor, many applications utilize multiple passwordless options. Platforms akin to ZITADEL, which work with sensitive data, generally implement open standards such as FIDO2 that allow users to use at least one of the listed methods.
Not to be confused with passwordless is Multi-Factor Authentication (MFA). While the latter commonly utilizes a passwordless factor in addition to the regular username-password login method, it is ultimately not the same as the complete omission of passwords as done by the passwordless approach. For example, an MFA-based system might request you to enter your password and then use Face-ID as a secondary authentication factor, whereas a passwordless-based system would solely rely on Face-ID to confirm your identity. Although both of these methods undoubtedly surpass traditional password-based logins in terms of security, passwordless systems are less susceptible to phishing and cyber-attacks due to their complete waiver of passwords. Moreover, passwordless is less time-consuming and memory-reliant nature generally makes for a more convenient user experience.
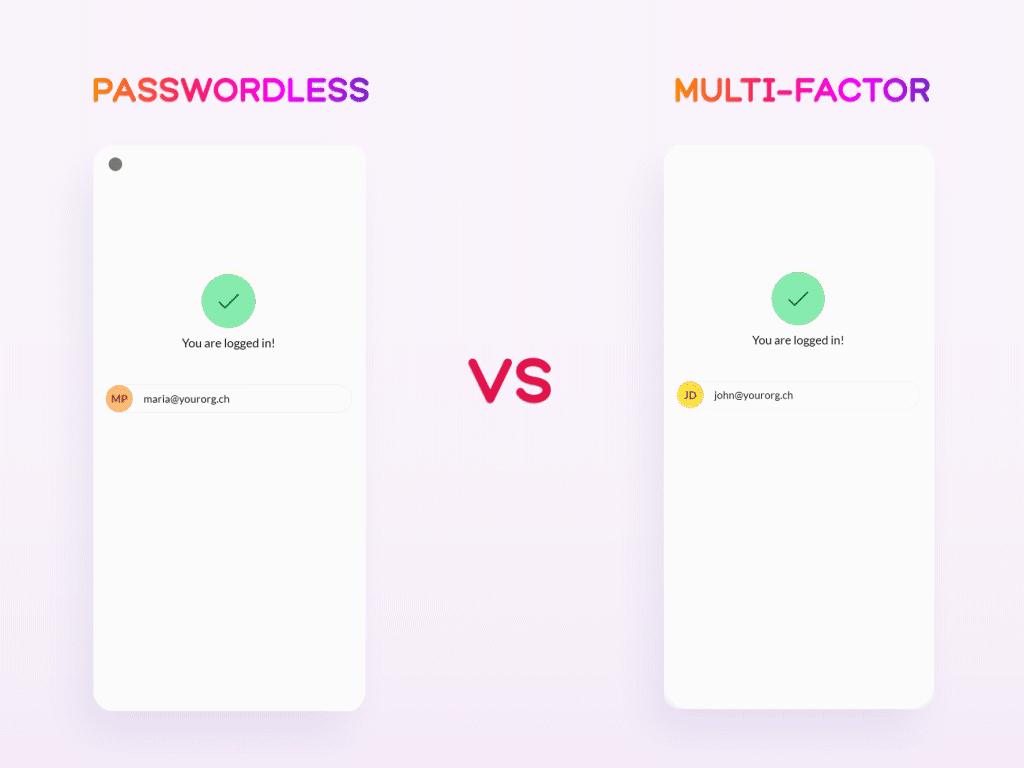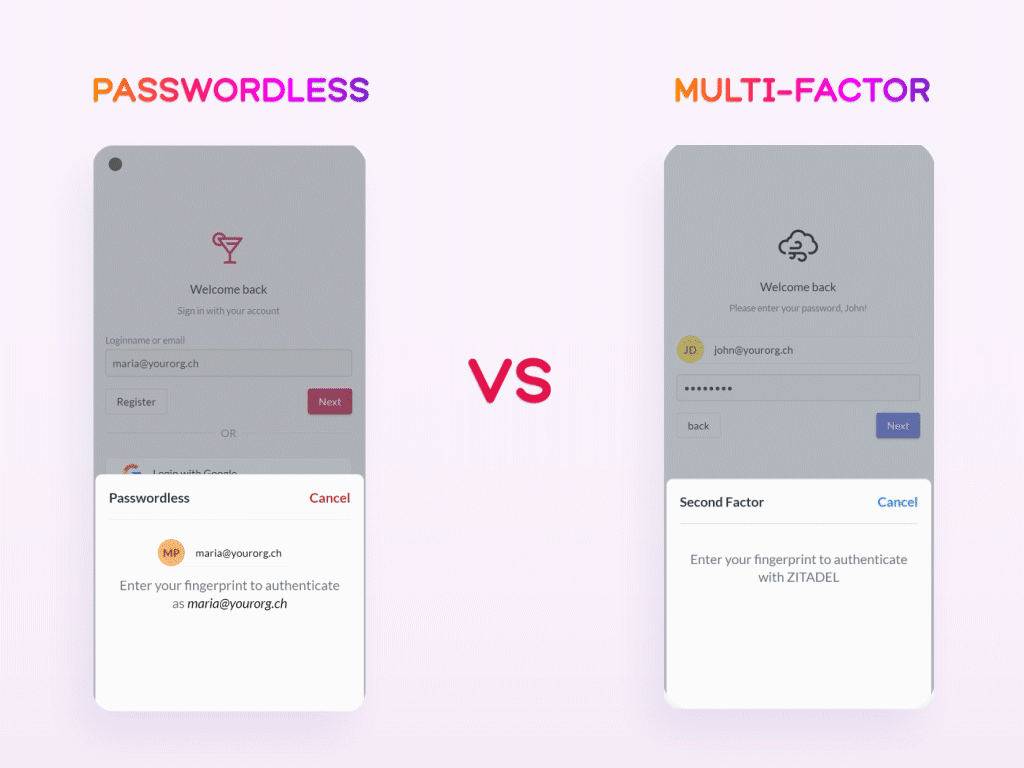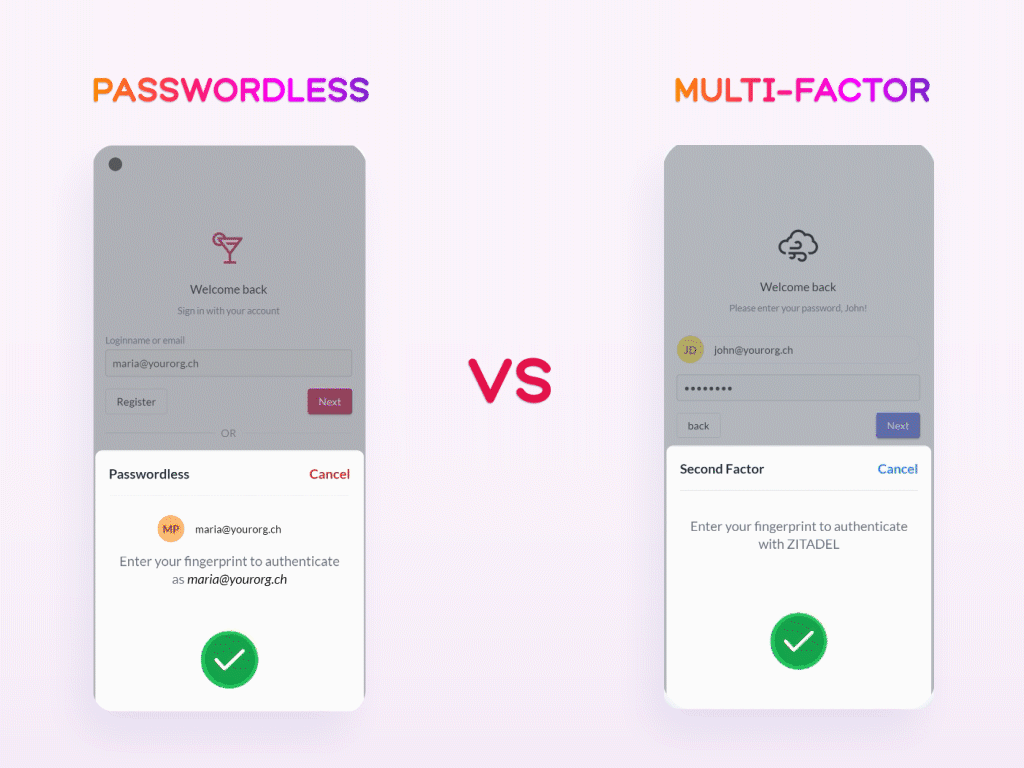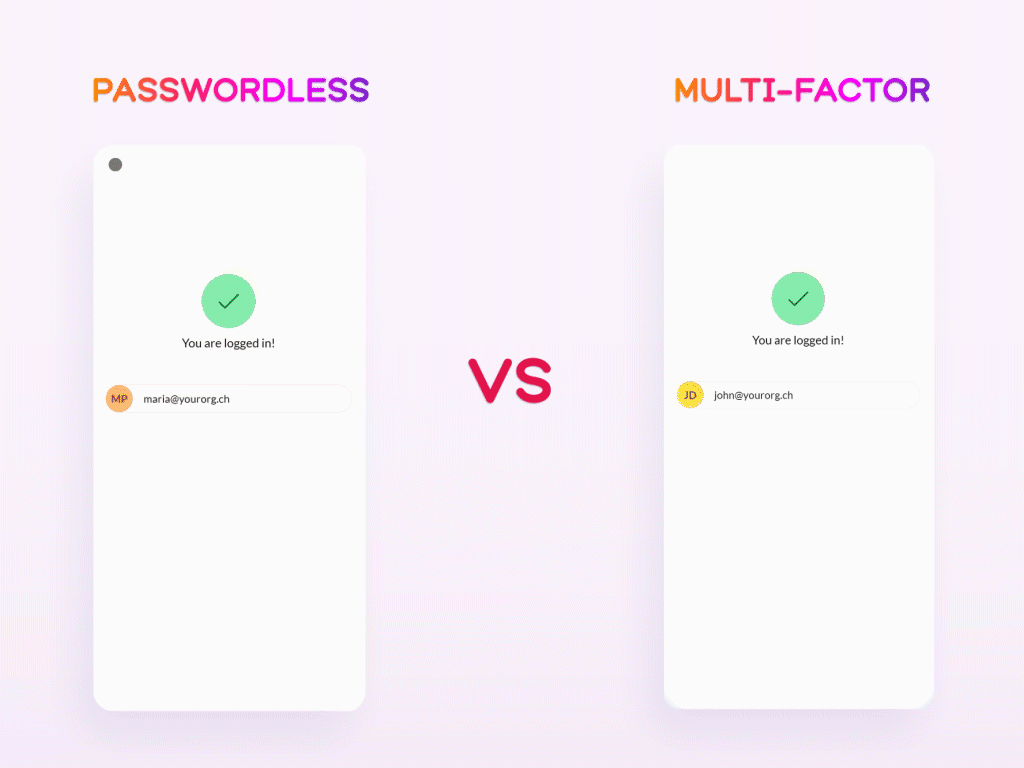
With this said, the existence of the passwordless authentication alternative might pose the obvious question: Why should it be used? To answer this question, it is worth looking into the issue it means to eliminate: the increasing problems with passwords.
The problems with passwords
One of the most apparent reasons for the popularity of the passwordless alternative is the increasing dissatisfaction with the traditional username-password login method. While the usage of passwords has been the industry standard for decades, the evolution of technical knowledge amongst the public also opened the door for more and more cybercriminals who take advantage of the simplicity of this authentication method.
Even when used in combination with Multi-Factor-Authentication, passwords are more prone to phishing attacks. This phenomenon occurs largely due to the fact that people tend to set a simple word or pattern as their passwords, since they are supposed to be easily recallable. Evidently, a complex combination of multi-case characters, numbers and symbols is harder for hackers to guess, but unfortunately, they are also harder for users to remember.
To protect their data from potential risks, numerous companies order their employees to change their passwords periodically. While on paper this measure might sound like an optimal solution to the password-problem, in practice however, it increases the chance of the user losing track of them. Moreover, people tend to use the same password for multiple virtual identities; accordingly, if a hacker should get a hold of your password, it would grant them access to each profile that uses the same login credentials.
Whether you buy into the passwordless journey or not, always enable two-factor authentication and use different passwords for each service. Use a password manager to ease the pain of multiple passwords and even creating and rotating new passwords.
Benefits of passwordless
To replace the previously mentioned risky password management practices, a new alternative had to be developed that does not tie the authentication process to a singular phrase: Thus, the passwordless method came into existence. Standards such as FIDO2 entirely rely on public-private key exchange between a user's device and the server that authenticates the user, thus passwordless not only eliminates the inconvenient practice of remembering complicated passwords but also ensures highly secure access to all your virtual identities. Moreover, switching to passwordless is highly beneficial for the users of an application and its developers: Due to the high cost of managing and maintaining passwords, the alternative generally poses a lower total cost of ownership (TCO). While the implementation of passwordless might seem expensive at first glance, its price does not even come close to the fines and losses incurred due to a cyber-attack.
The most significant benefits of using passwordless authentication instead of passwords:
- Security: Highly reduced risk of cyber-attacks
- UX: Higher customer satisfaction due to its convenience
- Cheaper TCO: No need to invest in maintaining passwords
- More Sign-ups: Not having to create a new password makes the registration process smoother, thus increasing customer satisfaction and sign-up rates
Why should a PIN be more secure than a password?
When using passwordless, users are generally prompted for a gesture such as FaceID, Fingerprint, or even just a PIN. At first glance, it might seem illogical how this method should be more secure than multi-factor authentication. The vital difference is that this gesture only unlocks a software or hardware-based “vault” where the keys are stored for authenticating. The personal credentials, such as biometrics or the PIN, itself were not shared across the network or even across devices.
Drawback of this method is that each device has to be enrolled individually in the service. For most users, this is confusing and creates additional friction in onboarding and managing users. However, according to the FIDO alliance, this issue will be solved with multi-device credentials, known as “passkeys”, within the current year.
ZITADEL and passwordless
As an identity and access management platform, ZITADEL holds the security of its customers and their end-users to the highest value: Accordingly, to replace security threats with highly modern login convenience, the inclusion of passwordless methods is indispensable. ZITADEL offers a wide variety of passwordless authentication options via FIDO2 for logging into its console itself and for the login form of the customer's application: They can use their fingerprint, security key, or any other WebAuthN compatible authentication method to log in. Regardless of which approach the user chooses, ZITADEL's passwordless authentication protects them effectively against data breaches, thus eliminating a significant attack vector.