Internet of things.
Secure IoT Authentication with Zitadel
Zitadel
Zitadel is the identity infrastructure solution built for developers and security officers with APIs and SDKs that enable easy integration into your project while delivering granular audit capabilities.
Zitadel supports unique features such as
- B2B Multi-tenancy
- In-context audit trail
- Machine-to-Machine authentication
- Non-human identity management
Use Cases
Have you heard of the Lac des Dix? It's one of the highest dams in the world. If you are in Switzerland it's worth a visit. It's used for hydroelectric power generation. Let's imagine the following fictive protagonists:
- A floodgate which opens if the water level is above 50 metres and closes if the water level is below 49 metres
- An operator who monitors the entire reservoir
- An application to monitor past water levels and state of the floodgate
- A water level indicator which sends its data every second to the floodgate and the application
The floodgate, the monitoring application and the indicator are technical users. This means that no human interaction is required for authentication. Let’s take a look at how this works:
Sensor to floodgate and application aka. machine to machine
For this purpose the sensor requests a token from ZITADEL and sends the data with the token to the receivers. Before they start processing the data, they request ZITADEL to verify the disclosed token and send information about the device of the token. With this information they are able to verify that the sender is the water level indicator and process the received data.
Operator uses application aka. human to machine
If the operator wants to take a look at the historical data he has to log in.
For that the application redirects the user to ZITADEL. The user passes its login credentials. ZITADEL validates this information and sends relevant attributes like roles of the user to the application. The application displays the history of the water level and when the floodgate was open and closed because the users roles allow the user to see these data.
Why is device authentication important?
Everyone should be able to verify the source of information. There are several possibilities to verify these sources, but if you have to verify hundreds or even thousands of them sending data in sub seconds, verification is only possible via automation. That’s the point where ZITADEL comes in.
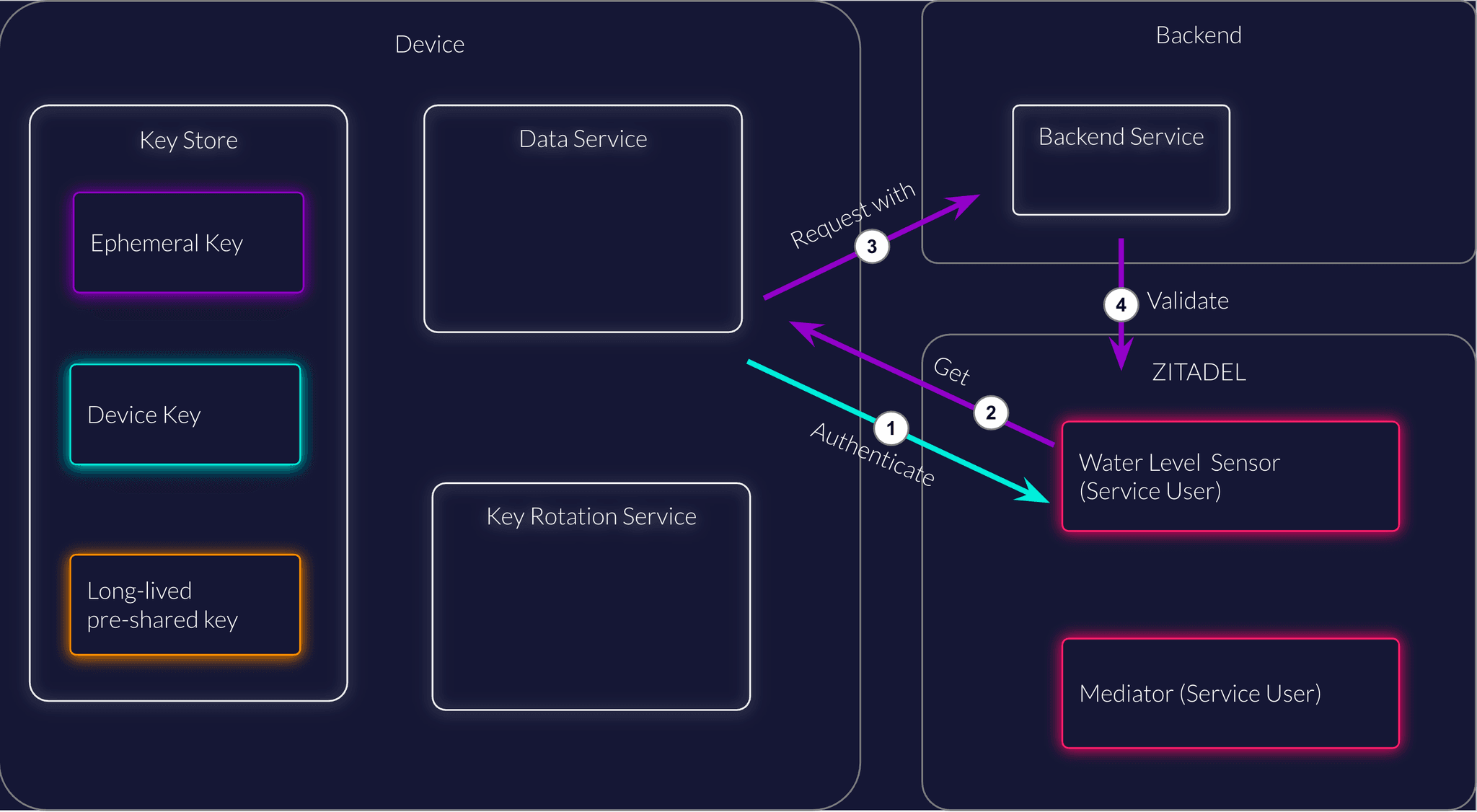
Following security best practices, a device should authenticate itself with a device key and use short-lived keys to send data to a backend service. The backend service can validate the key used in communication independently.
The backend service can ensure to only accept data from authenticated devices.
How to securely manage cryptographic keys
A common challenge is the secure rotation of key material. A manufacturer must ensure that even when keys are compromised, exchange of key material is safe.
That is why we recommend using keys with different lifetimes
- Ephemeral key for transactions (lifetime: minutes)
- Device key to authenticate the device and receive a ephemeral key (lifetime: days)
- Long-lived pre-shared key to rotate the device key (lifetime: months or years)
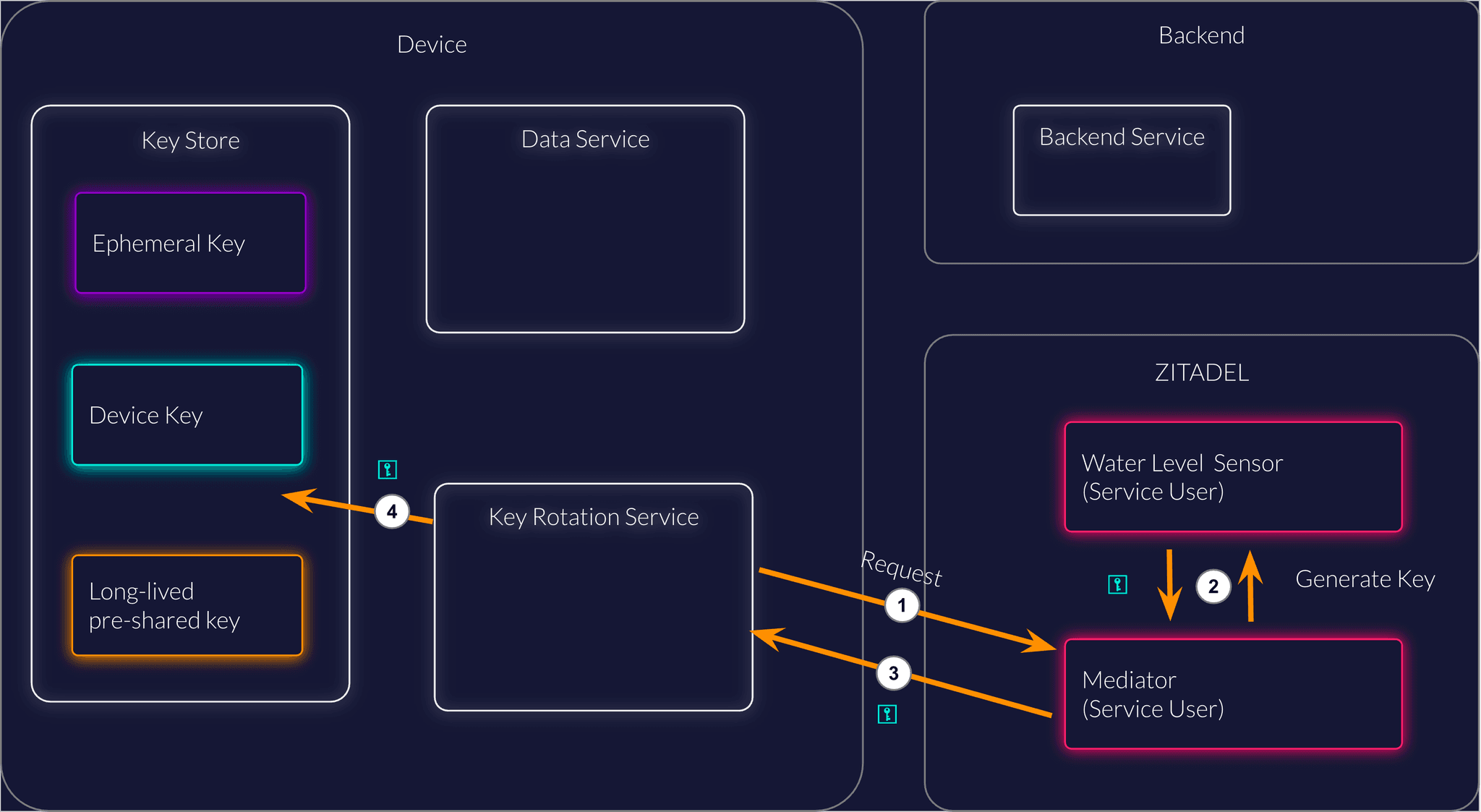
The long-lived pre-shared key must be exchanged physically with an attested device. This may happen during regular maintenance of the device or site.
An intermediate machine account (in ZITADEL called Service User) can be called with the long-lived pre-shared key to exchange the key material for a device (eg, Water Level Sensor).
Try it out
We would be delighted if you try out ZITADEL. You can create your ZITADEL Cloud Instace for free, no credit card required.
Further information
If you have further questions please contact us here
Florian describes the key differences between Keycloak and ZITADEL