IMO - Risk Based Authentication is broken

Founder and CEO
IMO = In My Opinion is a blog format where a author reflects his own opinion
At this year's Worldwide Developers Conference (WWDC) 2021 Apple did announce something that really got me thinking about what the future for Risk Based Authentication (RIBA) holds.
In short Apple did announce a feature called “iCloud Private Relay”. What it basically does is to hide the user's origin from the services the user calls. This in a way that Apple and the egress provider should not be able to track the user. Whether that’s true or not is a thing we will see in the future. This design somewhat resembles what TOR does but with less privacy.
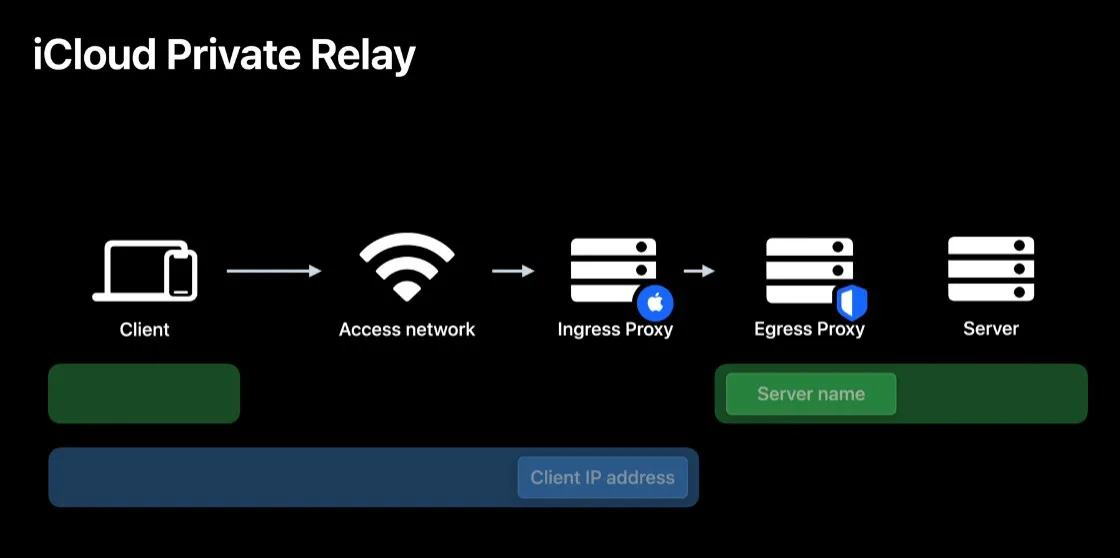
If a user enables this feature, your RIBA seriously will have a bad time. This is because, as you can see below, the user's IP Address will be more or less useless as a signal. As of writing this blog I was in Switzerland and the IP used to egress my traffic was in a region located in the US. If this also tends to change a lot and fast you can basically throw away IP addresses as data of your RIBA.
{
"ip": "2a09:bac0:205::815:95a",
"ip_decimal": 55878094235311776708809106431373805914,
"country": "United States",
"country_iso": "US",
"country_eu": false,
"latitude": 37.751,
"longitude": -97.822,
"time_zone": "America/Chicago",
"asn": "AS13335",
"asn_org": "CLOUDFLARENET",
"user_agent": {
"product": "curl",
"version": "7.76.0",
"raw_value": "curl/7.76.0"
}
}
Some of you now might say: “Well we have cookies and browser fingerprinting”. Yes but with Apple's recent announcement towards improving the privacy features of Safari things are getting harder as we speak. And this does not only apply to Apple but other browsers as well.
So what is the solution to all of this?
To be frank with you, get rid of your RIBA process and start towards the passwordless journey. It both improves your security and the users' risk quite a lot. If you are interested I dearly recommend that you read my IMO - Passkey in iCloud Keychain as well.
So that’s it? Just throw RIBA away?
Well there is a nuance to this, which I might encourage you to differ a little from that view. If we are talking about re-authentication and session management, I still recommend you to use signals you collect about the device and user, for example user-agent version, language, time, TLS version and cipher and so on to prevent things like “session cookie extraction” from the browser.
But please stop relying on RIBA for the plain authentication of a user!