Evolving IoT Security: From Traditional Logins to Device Authorization Flow

Developer Advocate
Introduction
At its heart, the Device Authorization Flow or OAuth 2.0 Device Authorization Grant is an OAuth 2.0 extension (defined in RFC 8628), designed for devices that either lack a keyboard or have limited input capability. This extension enables applications (OAuth clients) on such devices to obtain user authorization by using a browser on a separate device, such as a smartphone. For this flow to work, the device needs to be:
- connected to the Internet
- able to make outbound HTTP requests
- able to display a URI and a code sequence to the user
Of course, the user must also possess a secondary device (e.g., a computer or smartphone) from which they can process the request.
Practical Uses of the Device Flow: From Your TV to Your Fridge
Have you tried setting up your Spotify account on a smart TV or perhaps a gaming console, such as Xbox? Switching between letters, numbers, and symbols on an on-screen keyboard can be frustrating, particularly if your credentials include a mix of uppercase, lowercase, numbers, and symbols, and also because they are required to be of a certain length. So, instead of the painstaking task of typing out a password using clunky controls, you are presented with a code and told to enter it on Spotify’s website via another device. That smooth process is the device flow—born out of the need to simplify logins on gadgets without easy typing capabilities. While many of us use the device flow with familiar services like Spotify, it's also working behind the scenes in modern devices. For instance, have you come across high-end fridges that display recipes or weather updates? What about the latest vehicles that come with sophisticated touchscreen displays that offer a variety of apps and services? Imagine trying to input login details without a tangible or virtual keyboard in sight with Wearable Tech like Smart Glasses or VR Headsets. Sounds tricky, right? They all can benefit from the device flow.
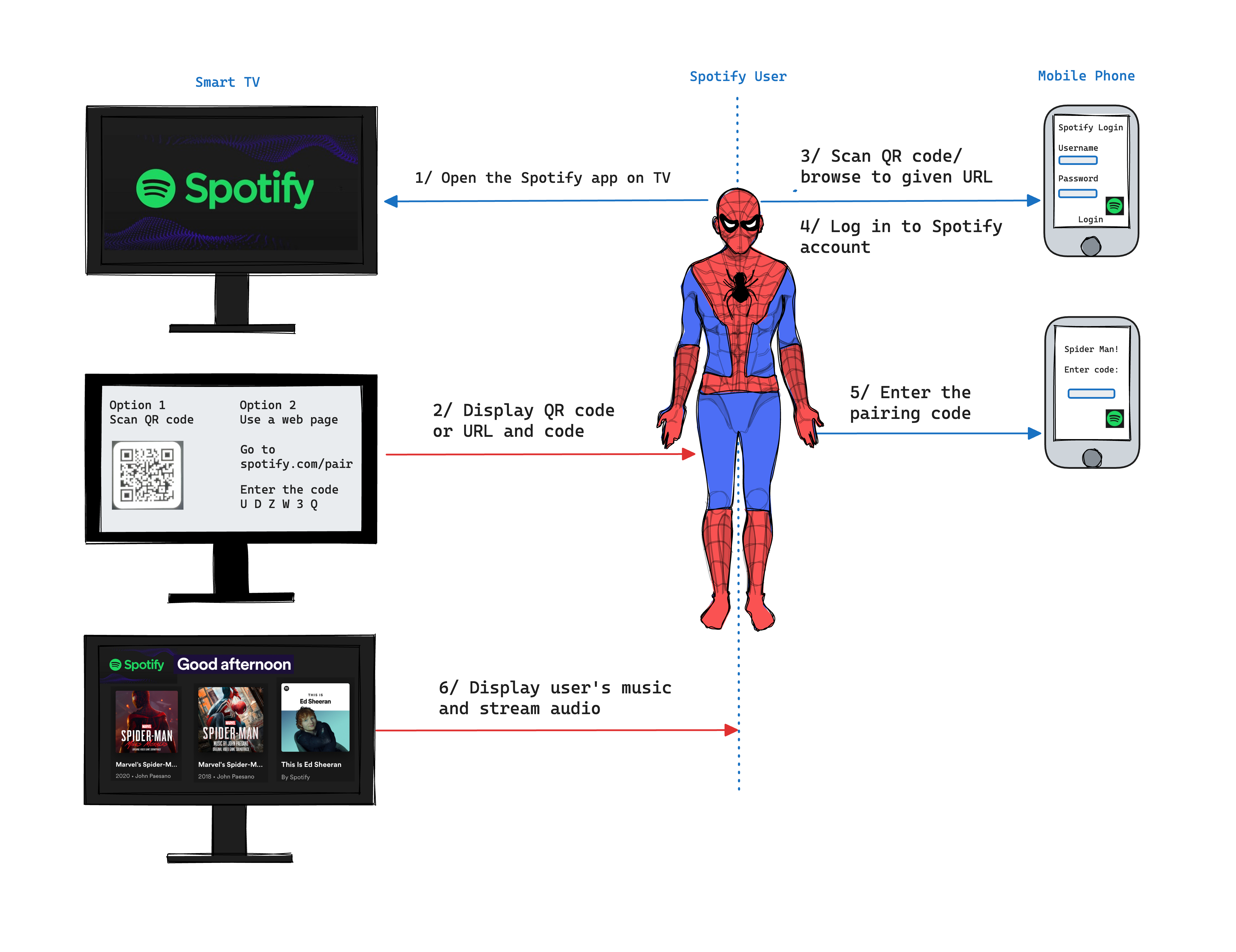
Figure 1 - User Experience of the Device Authorization Flow in Spotify
For IoT app developers, this flow is golden. It is especially handy for those crafting apps for devices where traditional login methods would be, well, a nightmare. The flow ensures that the users are getting connected without a hitch, whether they are watching, gaming, or even cooking! Here is a simplified breakdown of the flow from the perspective of the user:
- Initiation: You request access to an app or service on a device, say, a smart TV.
- Code Display: Instead of the familiar username/password prompt, the device displays a user code and provides a verification URL. This verification URL is your portal to authenticate. How you see this – be it text or a QR code – depends on your device.
- User Verification: Using a secondary device, like your smartphone, you visit the verification URL, enter the code, and then log in as you normally would.
- Grant Access: Once you are verified, you are granted access to the service via the input-constrained device, e.g., the smart TV. This might sound like a handful of steps, but in real-time, the flow is swift and intuitive, thanks to the backbone of the process: the Identity Provider.
Why Incorporate Device Authorization Flow into your IoT Apps?
Choosing the OAuth 2.0 device flow over conventional on-device logins has its perks: Users will no longer fumble with tricky on-screen keyboards Users can follow their usual login methods—they can also utilize saved passwords or password managers. Users can use advanced authentication methods as usual, like WebAuthN. Overall, it is safer for the users, especially when they are unsure about the device's security. For example, if the user wants to use a smart TV in a hotel, the device flow ensures they never input actual credentials into the unknown device. They just log into the service, e.g., Netflix, on their smartphone, and the TV gets a special token. They can revoke that device's access from their Netflix account once they check out.
Enforce Device Authorization Flow Using an Identity Provider
In the simplest terms, an Identity Provider(IdP) is a system that authenticates users, essentially confirming, "Yes, this person is who they say they are." The IdP is the trusted entity that verifies user identities and dishes out tokens that apps or services can use to confirm a user's authenticity. In our Device Authorization scenarios, the IdP is instrumental in verifying the identity of the person scanning that QR code on their TV, car touchscreen, or VR headset.
The Role of Identity Providers in the Flow:
- Identity Verification: When you scan that QR code with your phone, the request is forwarded to the Identity Provider. The IdP validates your credentials when you log in through the verification URL via the secondary device (e.g., your smartphone). It ensures that the person trying to gain access is indeed the rightful account holder.
- Token Generation: Once you've authenticated yourself on the secondary device, the IdP generates an access token, which the TV or other input-constrained device obtains. This token gives that device the okay to access the desired service.
Why use an Identity Provider for Device Authorization?
Standards-compliant IdPs support the OAuth 2.0 Device Authorization Grant, ensuring a universal, streamlined process across devices and platforms. For developers, incorporating the Device Authorization Flow becomes much simpler with an IdP in the mix. Instead of wrangling with the intricacies of user authentication and token management, developers can leverage the robust frameworks provided by IdPs.
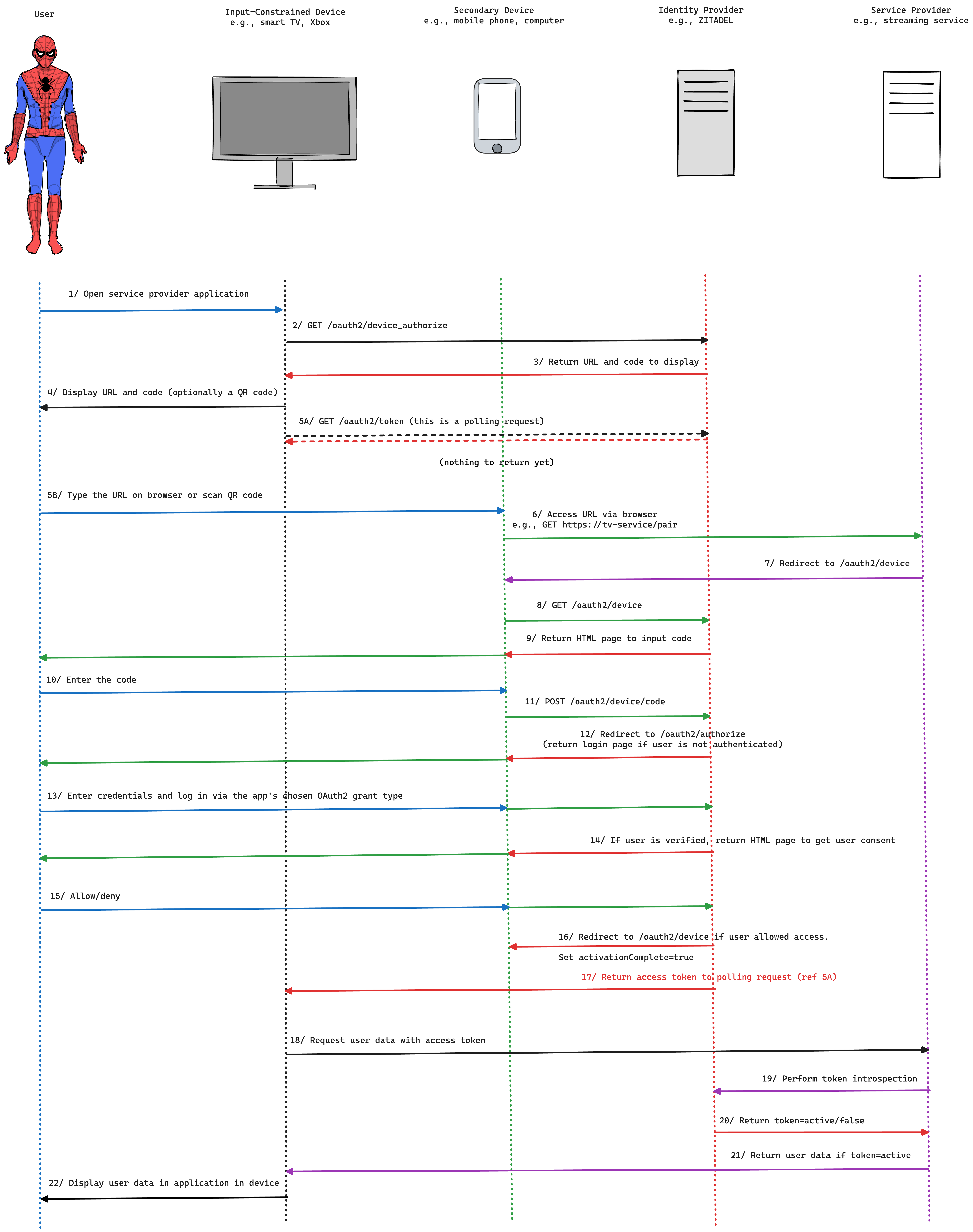
Figure 2 - The OAuth 2.0 Device Authorization Flow with an IdP
Try out the Device Authorization Flow with ZITADEL
For example, ZITADEL is an Identity and Access Management solution, which offers a SaaS and is also open source if you want to self-host and need more flexibility. It supports both B2C and B2B scenarios. You can authenticate users and authorize your application to access their protected resources on their behalf on ZITADEL with OAuth2/OpenId Connect(OIDC). ZITADEL supports the OAuth 2.0 Device Authorization Grant, and you can try out the Device Authorization Flow in ZITADEL through this example. You can also read this post on the other OAuth2/OIDC grant types that ZITADEL supports, how it supports them, and recommendations depending on the application type.
Closing Remarks
As we venture further into a world brimming with diverse smart devices, ensuring seamless and secure access across different devices becomes crucial. The Device Authorization Flow is proving to be an effective bridge, making our digital experiences more fluid, regardless of the gadget in use. Using an OAuth-2.0-compliant Identity Provider ensures this process is seamless and ironclad. For application developers, the IdP is not just a convenience. Instead of building a complex identity verification system from scratch, developers can lean on trusted Identity Providers to ensure top-notch security, compliance with privacy regulations, and a seamless user experience, all while saving time and resources.