How Password Hashing and Salt Can Enhance Password Security

Marketing
Maintaining proper password hygiene does not end with creating a strong password - How your passwords are subsequently stored is equally pivotal to the safety of your personal data.
The most common practice enterprises use to authenticate their users is implementing a system that compares offered credentials to those stored in a centralized database. Due to the comprehensive collection of user passwords in this database, it has unfortunately emerged as an attractive objective for malicious actors.
This article discusses the importance of password hashing and salting to secure password storage.

What is Password Hashing and why is it used?
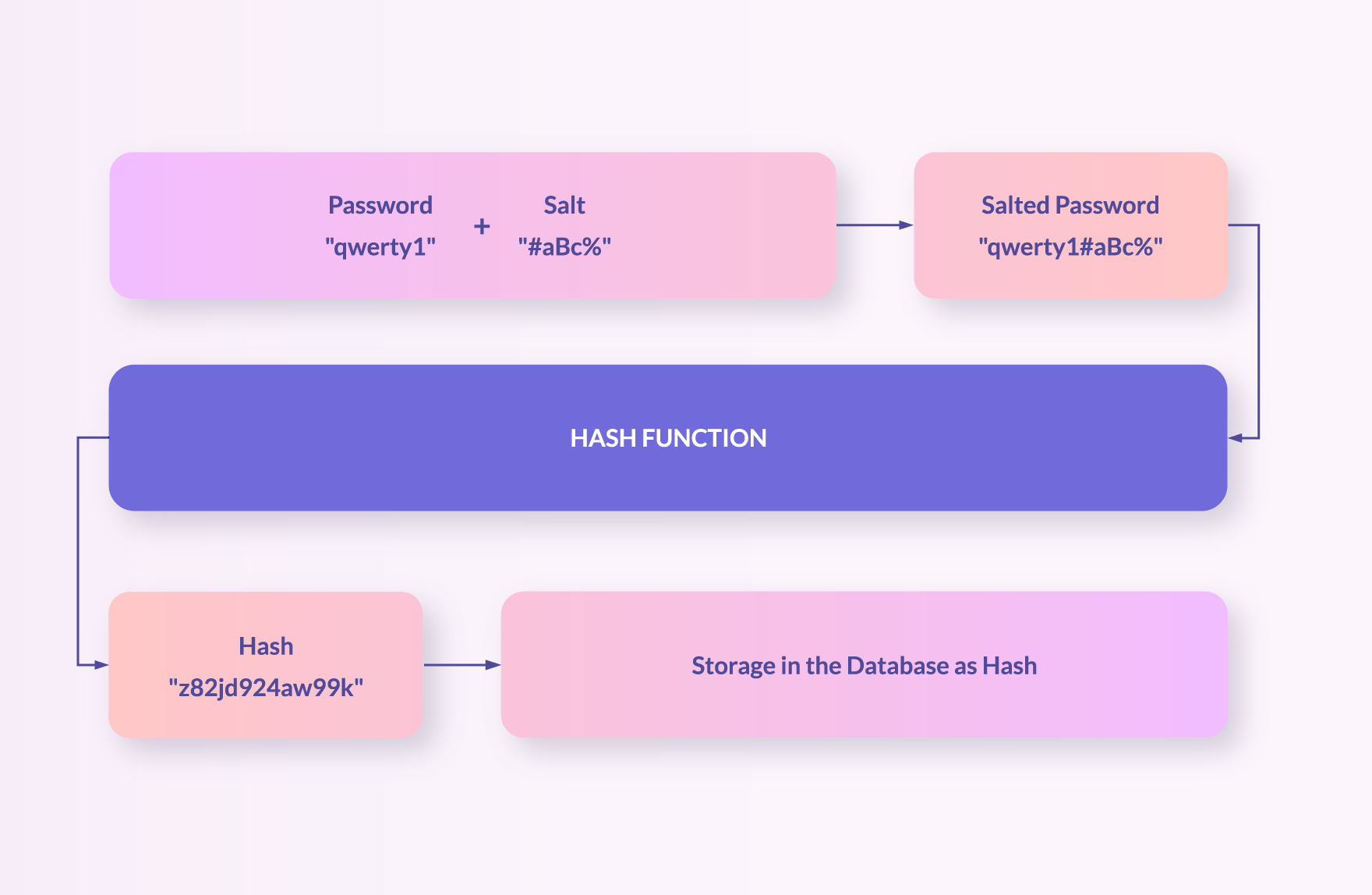
The term "password hashing" refers to the process by which a cryptographic algorithm converts a password irrevocably into a string of characters and numbers known as a hash. After this conversion, the password is stored on the company’s server in its hashed state instead of plain text.
But why is it necessary to store passwords as a string of code? The answer is simple: Doing so helps to safeguard it against a potential attack on the database.
Imagine you are a user attempting to sign in to your company’s server. After entering your password, it is automatically hashed and compared to the hash stored in the platform’s database. If an attacker gained unauthorized access to this database, they could still only see a code in your password’s place. Since password hashing is a one-way function, it is impossible for them to determine the actual password from the hash alone.
The Importance of Salted Passwords
While holding a hashed password in a server's database is unquestionably safer than displaying it in plain text, password hashing is still not immune to all types of cyberattacks.
As an example, if the attacker were to learn the hash function used by the hashing algorithm, they could try conducting a brute-force attack by entering random passwords into the function until a matching hash is found. While this particular attack might often prove inefficient, because hash functions can be configured to take a long time to execute, there is, unfortunately, another method at the attacker's disposal:
One of the most common methods attackers use to crack password hashes is called the “Rainbow Table Attack.”
Rainbow Tables
Rainbow tables are large databases containing precalculated hash values for common passwords. If a hacker manages to compromise a hash already listed on the table, they can trace that hash chain backward to determine the original password.
Think of hashing a plaintext password as an equivalent of translating a word into another language. Just like how “Katze” is consistently translated as “cat,” the hash code for the password “qwerty” will always be represented by the same combination of characters and digits. Rainbow tables are similar to dictionaries, storing a list of passwords along with their corresponding “translations.” Therefore, if a hacker figures out this universal hash for “qwerty,” they would automatically be able to recognize this password in every database - as if it were written in plain text.
Adding Salt to Hashing
As proven by the security issue posed by brute-force attacks and rainbow tables, Password Hashing alone is not entirely foolproof. Fortunately, a specific technique can be used to boost hashes and subsequently counteract rainbow table attacks. This method is called Salt Hashing, also known as adding Salt to a password.
In this context, the term “salt” describes a random string of characters added to the password prior to hashing. The hash is then created based on the combination of the random salt and the password instead of the password alone. Since the value of the salt is uniquely generated for every hashing process, even if two users have the same password, their hash codes will differ. Thus, making the rainbow table useless.
This technique of salting passwords has become a fundamental element of modern hashing algorithms, such as bcrypt. As opposed to weak hashes found in older algorithms, an attempt at breaking the robust architecture of salted hashing functions would require far more computational power than ever before.
Hashing and Salting with Bcrypt
In the age of ever-evolving cyberattacks, password hashing and salting are indispensable components of every current password management system. Fortunately, a reliable authentication solution can lift these administrative responsibilities off your company's shoulders.
ZITADEL is a rapidly growing open-source platform that assists thousands of businesses in keeping sensitive information out of the wrong hands. The solution uses bcrypt, a ready-to-use high-level function that handles the salt, hashing, and string encoding. Due to bcrypt’s adaptability and integrated work factor, this tool is highly successful in preventing unwanted access to user accounts. Migrating users from a system that does not support bcrypt requires users to reset their passwords, as it is impossible to transform one hash to another hash function on the fly. Thus, we will expand the options of available hash-functions in the future, such that multiple hash functions are supported.