Why FIDO2 Passkeys are Safer than MFA and Passwords

Marketing
As digital threats and cyberattacks continue to evolve at an alarming rate, the need for robust and reliable security measures has never been more prevalent. Traditional methods of authentication, such as passwords and even multi-factor authentication (MFA), have demonstrated vulnerabilities that attackers exploit to gain unauthorized access to user accounts and personal data. However, a new authentication method has emerged that has successfully eliminated the greatest attack vector by rendering passwords completely obsolete – FIDO2 passkeys.
This article explores all the reasons FIDO2 passkeys surpass passwords and MFA in terms of security.
What are FIDO2 Passkeys?
FIDO2 (aka FIDO 2.0) is the latest set of specifications of FIDO (Fast Identity Online), a set of open protocols based on public key cryptography. FIDO2 combines the W3C Web Authentication (WebAuthn) specification and accompanying Client-to-Authenticator Protocols (CTAP) with the pursuit of eliminating password usage over the internet.
This innovative collaboration allowed the introduction of Passkeys - passwordless credentials that let users access their FIDO sign-in information across multiple devices, including new ones, without needing to enroll each device separately for every account.
Unlike Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA), passwordless systems do not require users to provide an additional knowledge factor (such as passwords or PIN codes) to confirm their identity: The login process relies solely on possession factors, such as embedded (f.e. biometric authentication or PINs) or external authenticators (f.e. physical security keys, mobile devices, wearables, etc.).
To summarize, FIDO2 passkeys enable users to log into a platform only using a passwordless credential (such as FaceID or a physical token) of their choice and sync their FIDO private keys across multiple devices.
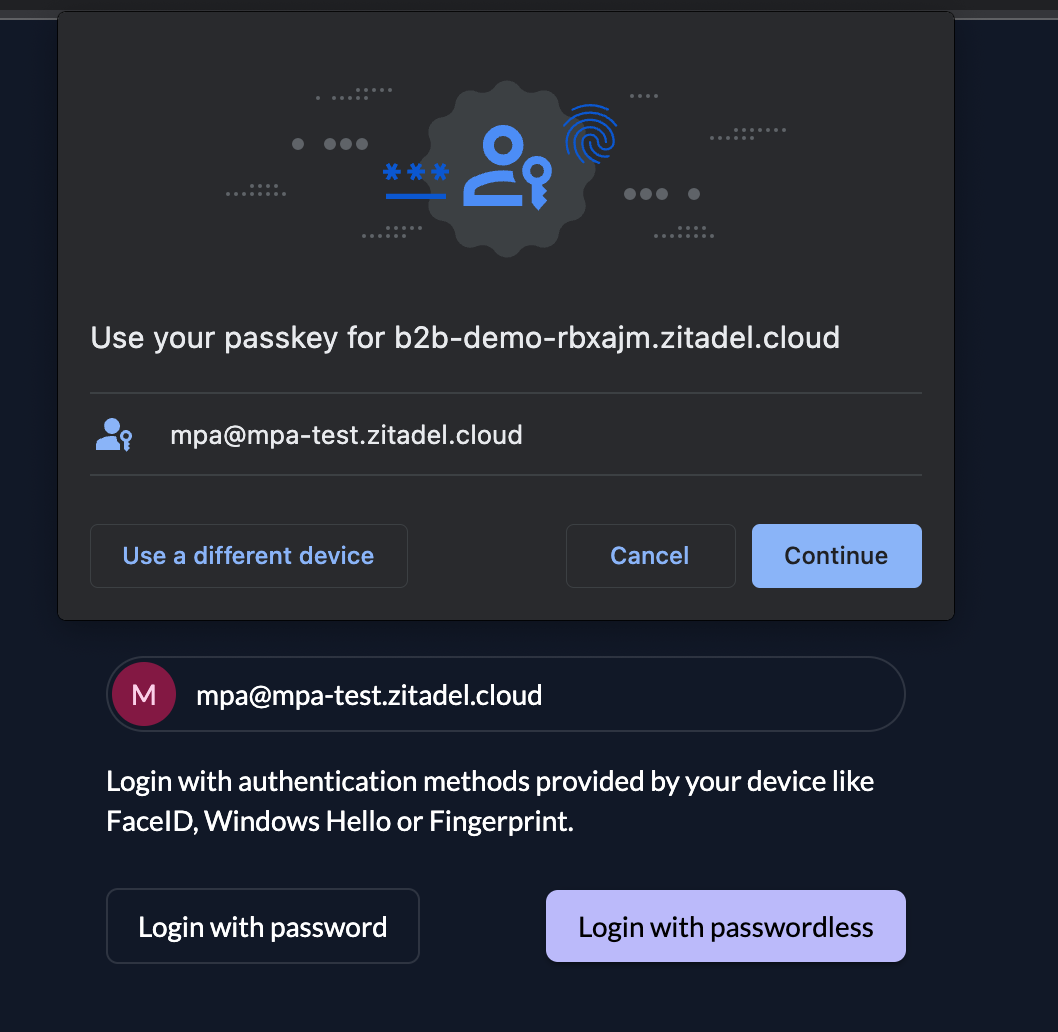
Figure 1 - Using passkeys in ZITADEL
Why are Passkeys Safer than Passwords and MFA?
Ever since their release, there have been some misconceptions and mistrust circulating around passkeys: Are they really as safe as they claim to be if PIN codes can be cracked and physical tokens stolen?
The following sections aim to debunk these misconceptions and explain why FIDO2 passkeys are the more secure and convenient alternative to 2FA, MFA, and password-based authentication.
Elimination of Passwords
One of the key reasons why FIDO2 passkeys are significantly safer than MFA is due to their complete waiver of passwords.
Although passwords have been the industry standard for decades, they have proven to be highly susceptible to various attack vectors due to several inherent flaws. Since they are knowledge factors that require easy recallability, many of them subsequently end up being easy to guess and are reused across multiple accounts. These simple passwords can be easily exploited by attackers, using techniques such as brute-forcing, social engineering, and phishing.
Passkeys, on the other hand, are a possession-based authentication method that employs advanced cryptography. Rather than depending on a human-readable secret, it replaces the password with a non-phishable primary factor for user authentication that is integrated into practically every computing device we use today. Thus, it makes cyberattacks practically unfeasible.
Phishing Resistance
While MFA adds an extra layer of security by requiring at least two authentication factors to gain access to an account, it is still not completely foolproof. There are various 2FA bypass attacks that can be employed to compromise both authentication factors and without the user’s knowledge: For instance, users can be subjected to social engineering by giving away their credentials or manipulated to do so by falling for MFA-Fatigue attacks.
One of the most commonly used 2FA bypass attacks is the Man-in-the-Middle (MITM) attack. This infamous phishing technique allows attackers to gain unauthorized access to an account without even knowing the victim’s login credentials by having a third party intercept the communication between two systems. A popular tool to conduct MiTM attacks is a phishing website: A fraudulent duplicate of a legitimate login page that tricks users into placing their credentials and second authentication factors directly into the attackers’ hands.
Fortunately, these attacks can be mitigated entirely with the help of FIDO2’s use of cryptography keys and challenges. FIDO2 uses two types of keys - a public key and a private key. The public key is linked to the domain of the service, while the private key is safely stored on the user's synced devices. Once you initiate a login to a platform that uses FIDO2, the server sends a challenge to your device. The private key is then used by your browser to provide a unique response to the challenge, which the server validates using the associated public key that is linked to it. If your response does not match the challenge, the login is unsuccessful. Thus, FIDO2 prevents users from authenticating on an illegitimate application or website.
Secure Storage
When we talk about the weaknesses of authentication methods involving passwords, guessability, and excessive reuse are the main flaws that tend to come to mind. However, one significant shortcoming is often forgotten: The storage of passwords in an often vulnerable, centralized database.
Within the framework of password-based authentication, the system is designed to compare offered credentials to the comprehensive collection of user passwords stored in a database. Needless to say, if this database is breached, attackers can retrieve all of the stored credentials and user data. While password hashing and salt can enhance the security of databases by converting plain text passwords into a random string of characters, that technique is ultimately still vulnerable to many attacks and might lead to follow-up attacks putting sensitive information at risk.
FIDO2 passkeys use public-key cryptography, which provides a higher level of security compared to centralized password databases. The private key never leaves the user's device, making it nearly impossible for attackers to steal or intercept it. Even if an attacker manages to access the passkey on one device, they cannot use it to access the account on another (unauthorized) one. Thus, there is no need for concern regarding the mishandling of your passkey secret by a website or that your passkey could be used to access another service.
Multi-device Authentication
In 2022, the FIDO alliance introduced a significant new development of the standard, which aimed to improve the usability and deployability of the FIDO-based authentication mechanism: Multi-device FIDO credentials. With the help of this upgrade, users who had set up multiple FIDO credentials for different relying parties on a device that they don’t use anymore can easily access all those credentials on a new device. The underlying OS platform "syncs" the cryptographic keys associated with a FIDO credential from device to device. Thus, this innovation mitigates the risk of losing access to your credentials due to device loss.
Bonus: Better User Experience (UX)
Passkeys eliminate the need to remember and repetitively enter complex passwords to access your accounts. These accounts can also be easily accessed from different devices without compromising security. Moreover, signing in with passkeys only requires a single authentication factor, making the login process faster and smoother than MFA. These advantages are especially helpful in scenarios where speed is crucial, such as making online payments.
In Conclusion
The main goal of the Identity and Access Management (IAM) solution ZITADEL is to ensure that the end-users of your application can verify their virtual identities in the safest and most convenient way possible. To make this goal a reality, we highly recommend they choose FIDO U2F tokens or FIDO2 Passkeys over MFA as their preferred authentication method. Learn more about ZITADEL’s authentication methods