New Personal Access Tokens (PAT): A game changer for Service Users
- JSON Web Tokens (JWT) and their application
- Personal Access Tokens (PAT) and why they are needed
- How to set up PATs on the ZITADEL console
- In Conclusion
Access tokens, as the name suggests, are an essential part of Identity and Access Management (IAM) Services: They are used to grant access to client resources. Since they contain such sensitive data, access tokens must be kept confidential in transit and in storage; the respective application should therefore ensure that the token is not accessible to other apps on the same device.
Access tokens come in different formats, all of which have their respective uses. So far, ZITADEL has allowed JSON Web Token (JWT) Profile for authentication of Service Accounts. This month, we are expanding the possibilities of our platform by introducing Personal Access Tokens (PAT) that can be enabled along with an existing JWT profile.
In this Article, I will explain why we have chosen to introduce PAT in addition to JWT, which audience this change will benefit and how PAT can be implemented into the ZITADEL console.
As a first step, it is essential to know what JWT and PAT have to offer.
JSON Web Tokens (JWT) and their application
JSON Web Token (JWT), is a compact and self-contained open standard used to share security information between a client and a server in a structured format (JSON). It is commonly used as an access token (for authorization and securing APIs) by specific protocols such as OAuth 2.0.
The use of access tokens is that they must be passed upon every request of an application to access routes, services, or resources (f.e. APIs) to confirm the user's authorization. Some solutions might not support JWT Profile for Machine-to-Machine (M2M) communication, although it is the preferred method to authenticate Service Accounts in terms of security.
Personal Access Tokens (PAT) and why they are needed
Personal Access Tokens are opaque tokens, i.e. no information can be extracted from the token itself, that enable granular access to a specific resource. This procedure is generally useful for interrogation with 3rd-party systems that use the respective platform to store records, and don't want to proxy all the protected resources via their system. In the case of ZITADEL, PATs were implemented to provide an alternative method of authentication for Service Accounts.
Although not as secure as JWT Profile, PATs are helpful for service users that have trouble integrating their Service Accounts with the preferred method. If this type of problem arises, it is advised to enable PAT along with JWT Profile. The token will grant access to all rights assigned to the user (within ZITADEL itself (manager roles) or in other projects by user grants). You should always limit the lifespan of a PAT and refresh regularly (e.g. every 30 days) to minimize security risks.
How to set up PATs on the ZITADEL console
Should you be interested in using Personal Access Tokens, it is vital to know how it is done. In this chapter, we show you a step-by-step tutorial on how to enable PATs on the ZITADEL Console.
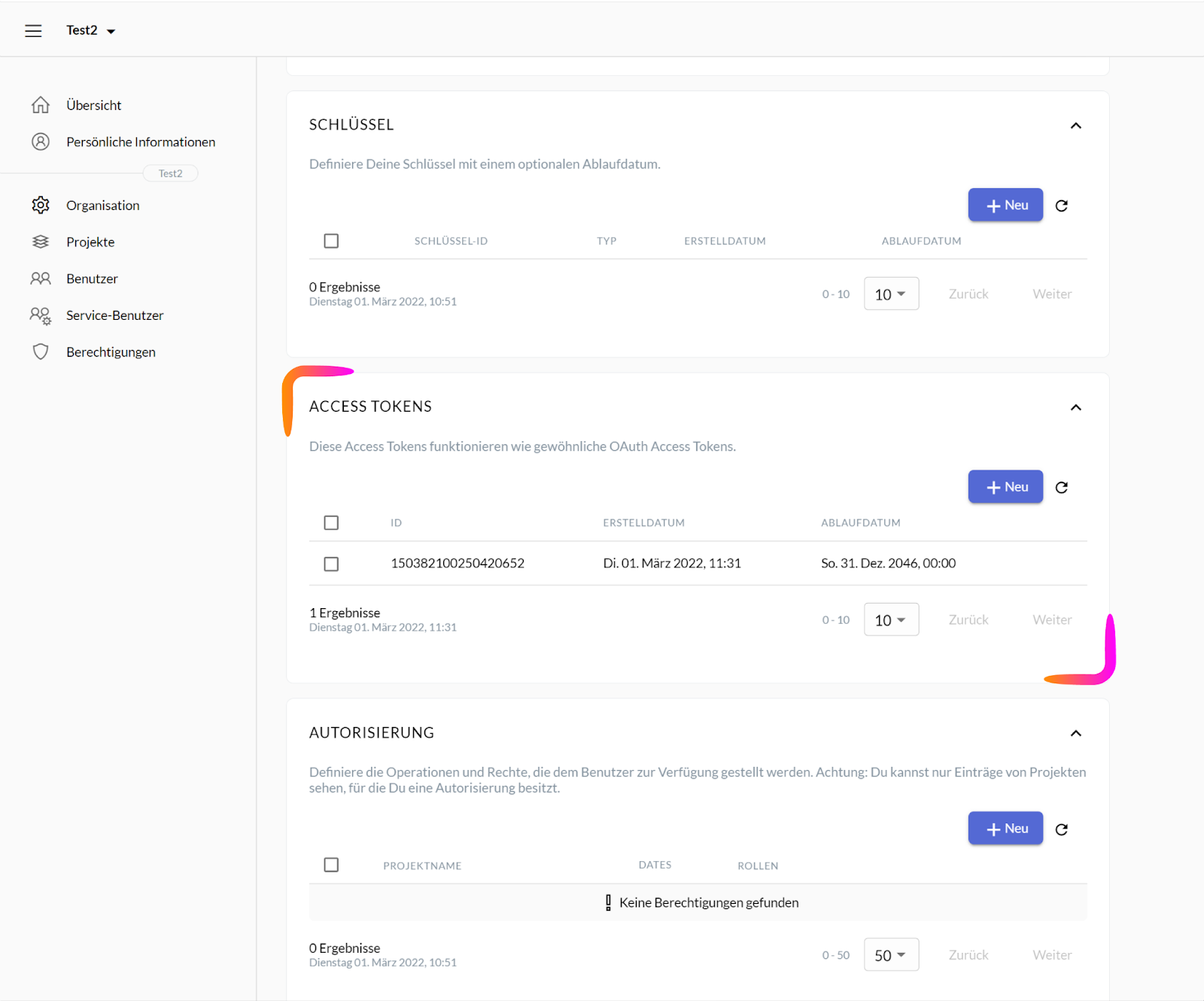
Upon signing into the ZITADEL Console, navigate to the Menu on the left of your screen. On the top left, select the organization you wish to assign the token to (here: Test2). Next, click on the menu item “Service Benutzer / Service User”.
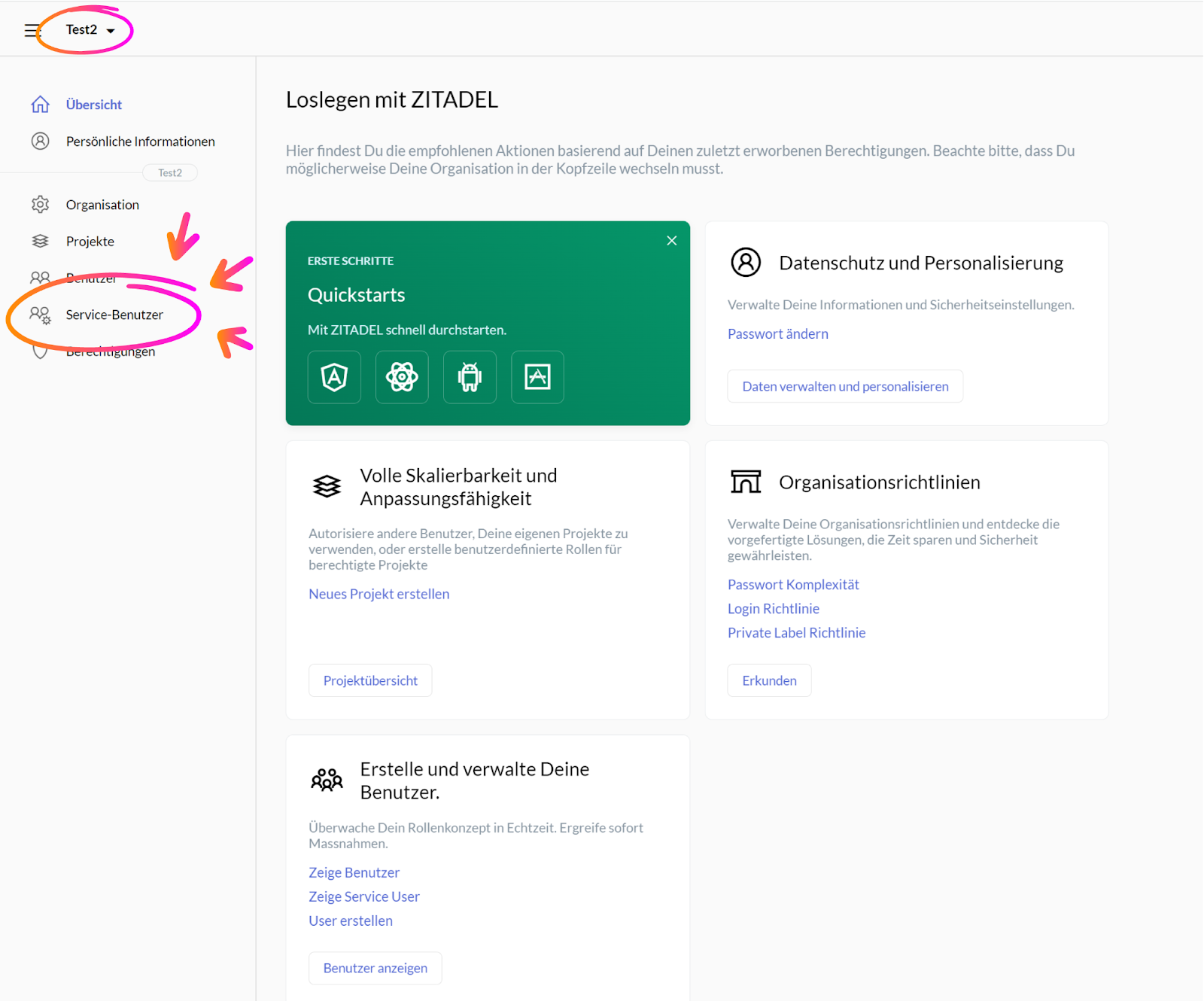
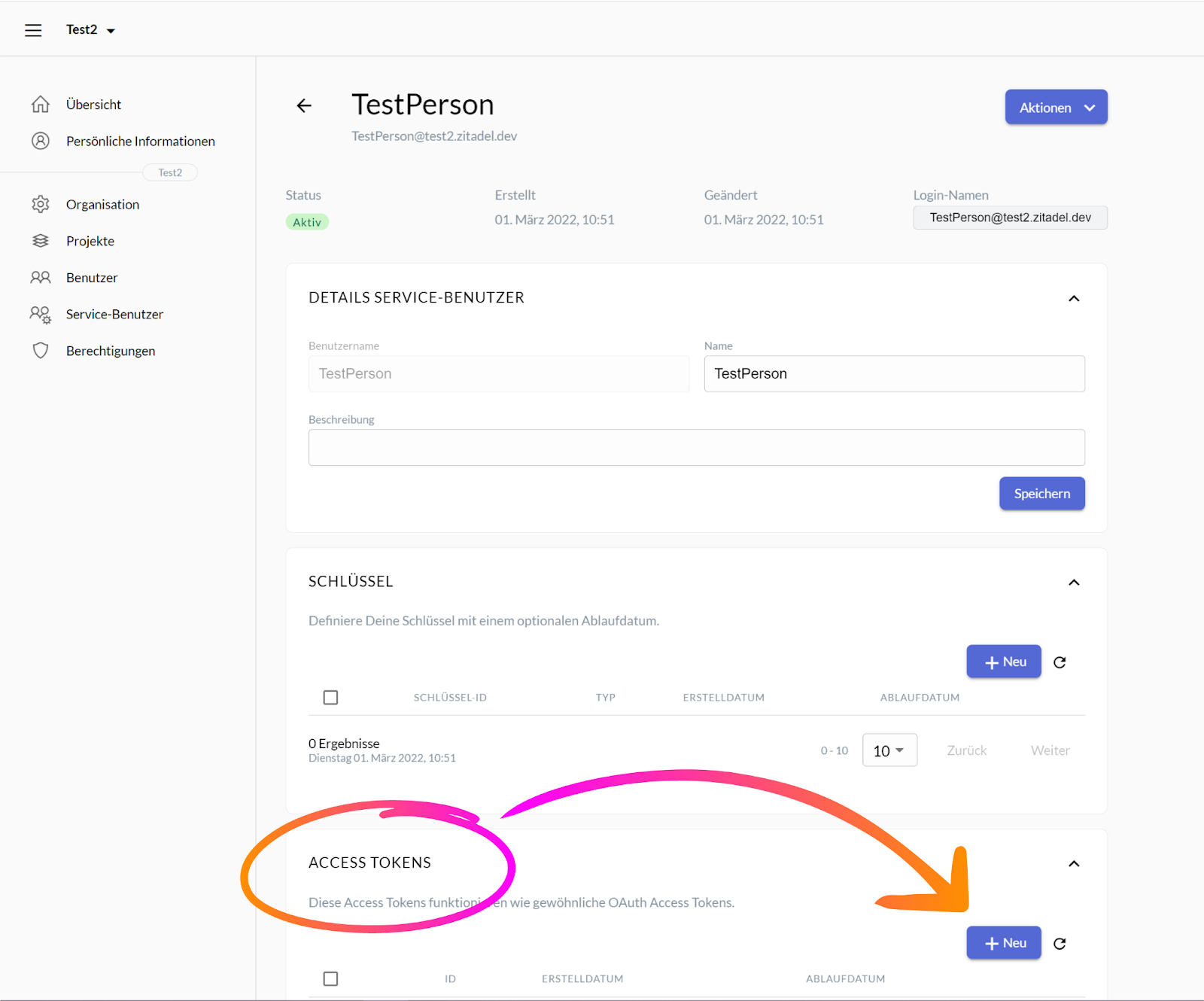
Clicking the “Service Benutzer / Service User” menu item should lead you to the page pictured below. To create a new Access Token, scroll down to the option called “Access Tokens” and click on the button “+Neu / +New”.
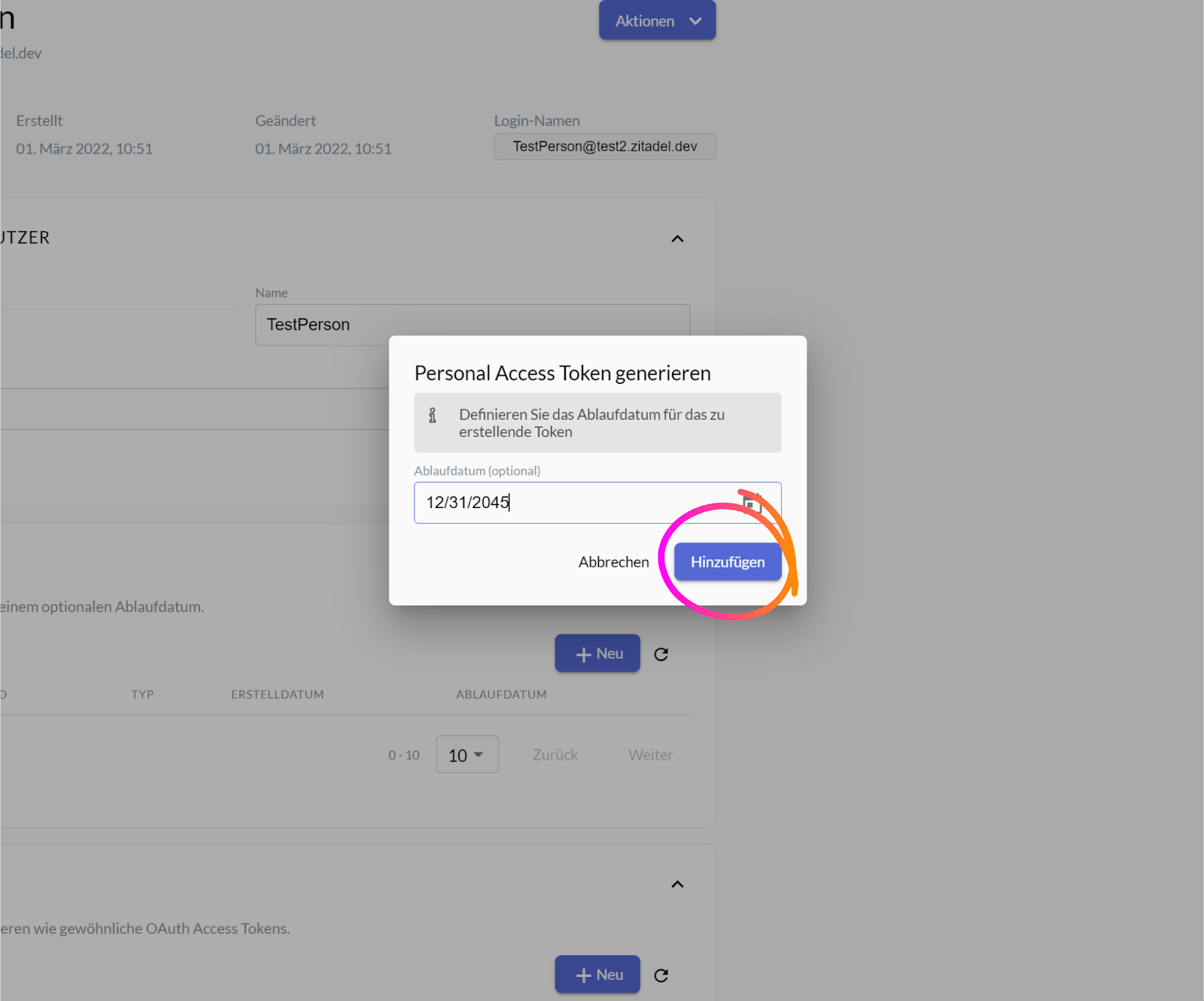
A small new window should pop up on your screen, asking you to define a custom expiration for the token you are about to generate. If you wish for your PAT to only be valid through a specific timespan, enter the desired expiration date into the input field or select it using the calendar icon on the right, then click the button “Hinzufügen / Add”.
Whether you chose to enter an expiration date or not, upon pressing the “Hinzufügen / Add” button, another small window should be revealed. The message in red will warn you to copy the long token code, for you will not be able to access this code again. To do so, click on the clipboard icon next to it. Once the code is copied, you can close the small window by pressing the “Schliessen / Close” button.
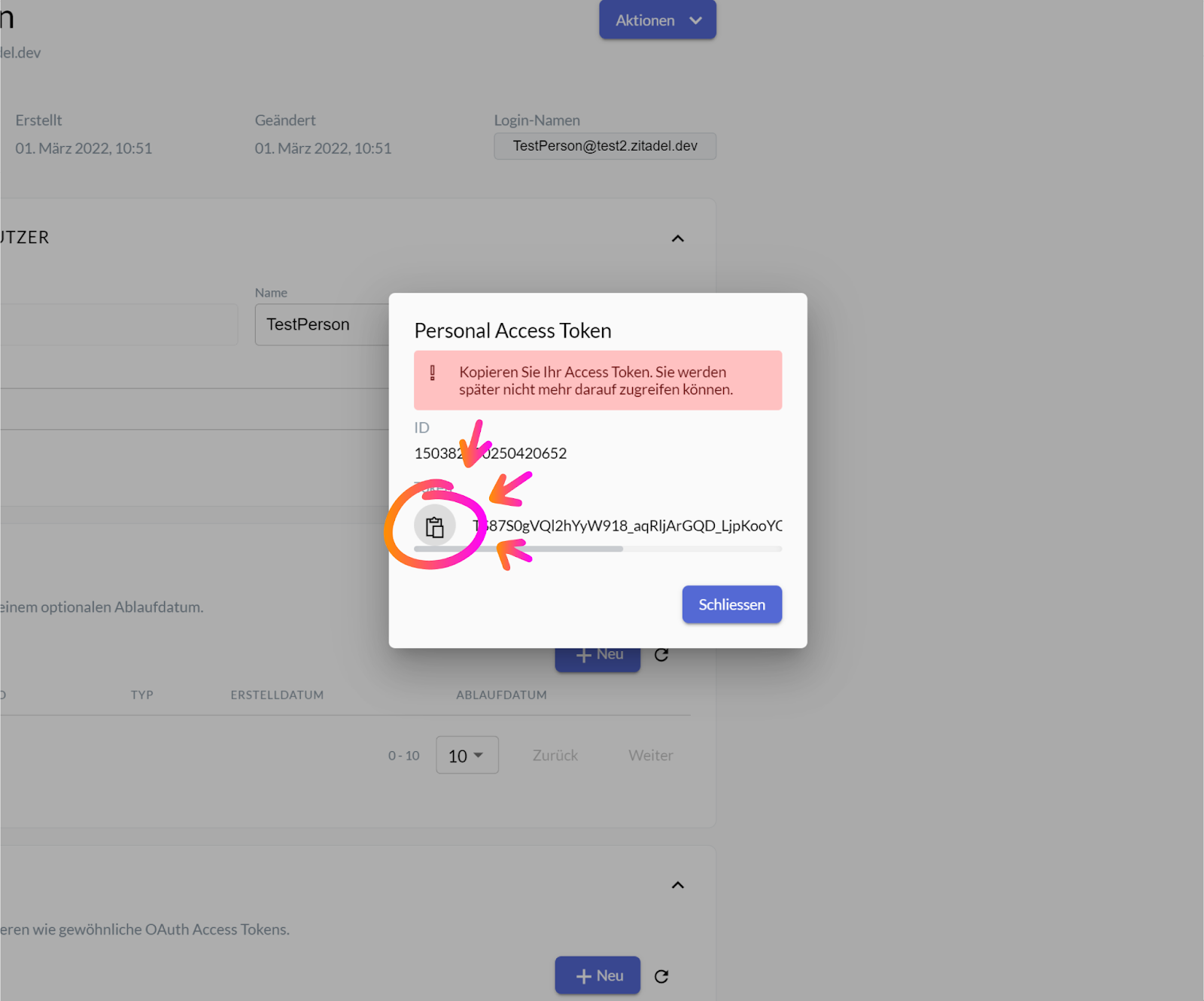
Following the previously listed steps should result in the creation of a Personal Access Token for your desired organization. Finally, the copied token code can be embedded as a bearer token in the authorization header into the ZITADEL application via a third-party service.
See our documentation for more details.
In Conclusion
If you are a service user and have trouble with integrating your accounts with JWT Profile, consider enabling a Personal Access Token along with JWT Profile.
Should you have questions regarding PATs, JWTs or any other related (or unrelated) topics, feel free to contact us anytime on our ZITADEL Discord Server. Alternatively, you can reach us on our Twitter, Linkedin or Github pages or on our Website.
