Authorization vs Authentication

Senior Developer Advocate
Recently, I wrote a blog post on Token Management. While the main focus there was on building secure authorization and what that means, I also briefly discussed the differences between authentication and authorization.That post is fairly technical. However, I realize not everyone learns that way nor will everyone fully understand the differences between the two. With that in mind, I decided to share a couple of real world examples with you that have helped me better understand things.
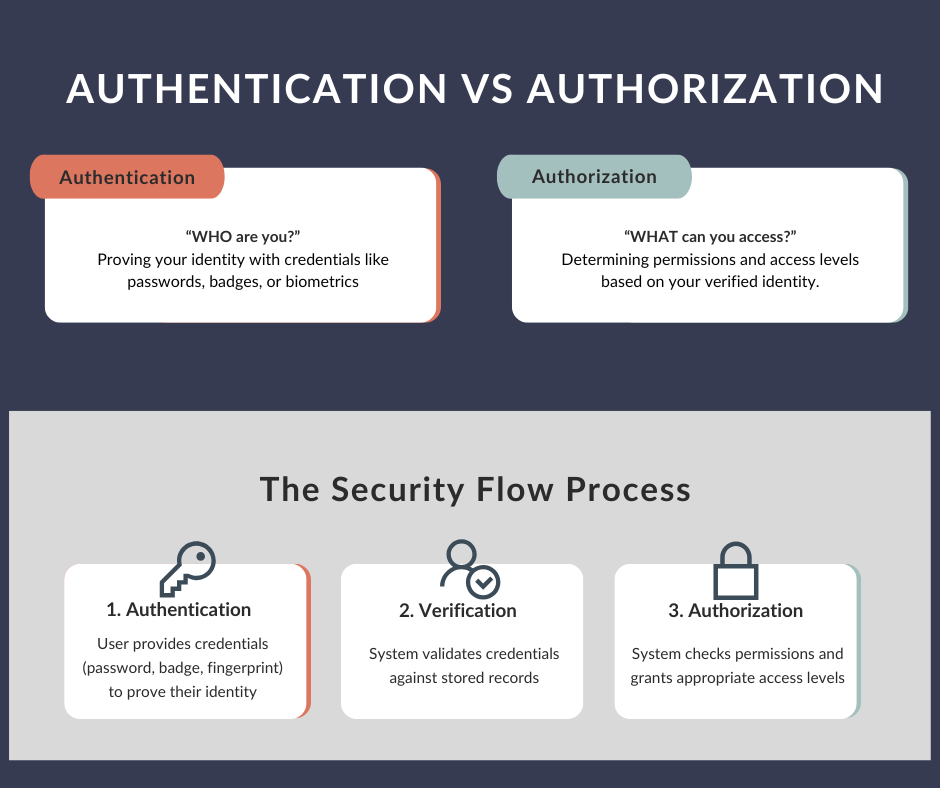
First, think of authentication and authorization as two separate but connected security gates. Authentication answers "Who are you?" while authorization answers "What are you allowed to do?" Once you grasp this core distinction, the examples become much clearer.
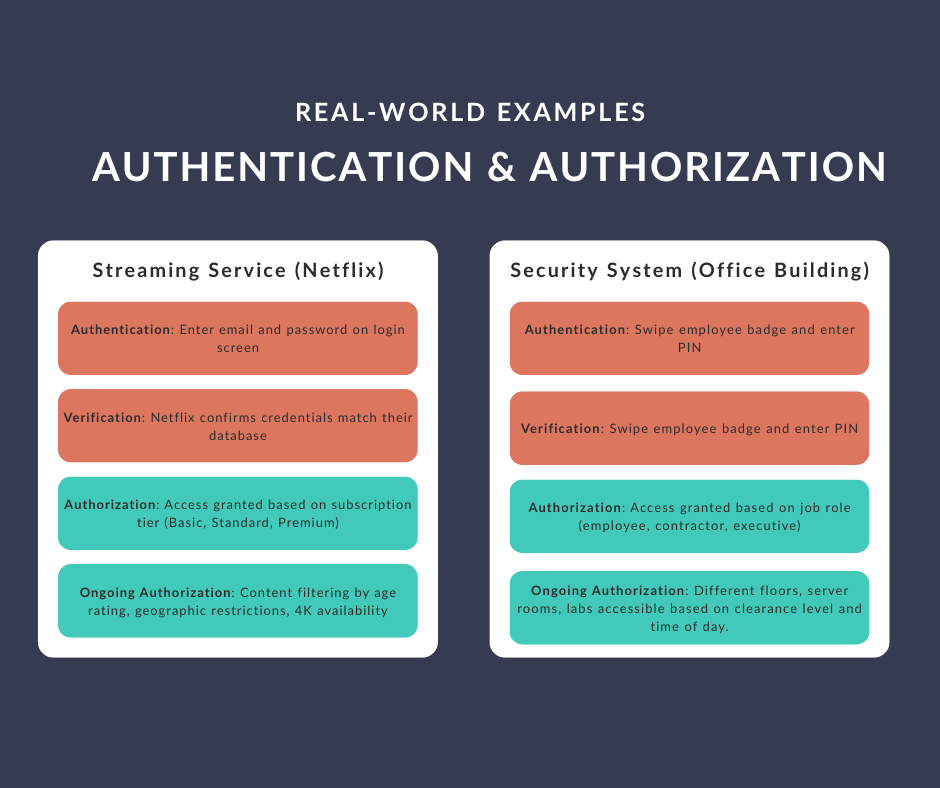
Starting with Streaming Services
When you open your favorite streaming service (we are going to use Netflix in this post) on your device, you first encounter authentication. This happens when you enter your email and password on the login screen. Netflix is asking you to prove who you are. Just like showing an ID card to a bouncer at a club, you are providing credentials that only you should know. The streaming service checks these credentials against their database to confirm your identity.
Once Netflix knows who you are, authorization kicks in. This is where the service determines which content you can access. Your subscription tier decides whether you can watch in 4K or just standard definition. Your account's age settings control whether you see R-rated movies. Your geographic location determines if you can stream certain shows that might be licensed differently in various countries. Even though you are the same authenticated person, your authorization levels change based on these factors.
Moving to Security Systems
Physical security systems work the same way but often make the distinction more obvious. When you approach a secured building, authentication might involve swiping or scanning your employee badge or entering a PIN code. The system is verifying that the badge belongs to you and that you are indeed the person authorized to use it.
Authorization happens next, even though it might seem instantaneous. The security system checks your employee record to see which areas you are permitted to enter. A custodian might have access to all floors but not the server room. An executive might access the top floors but not the laboratory areas. A contractor might only access specific floors during business hours. Your identity stays the same, but your permissions vary based on your role and current circumstances.
A Helpful Mental Framework
To remember the difference, think of authentication as the key to your house and authorization as the different rooms you are allowed to enter once inside. Your house key proves you belong there, but your family might have rules about which rooms different people can access.
Here's another way to cement this understanding: authentication is typically something you prove once per session, while authorization gets checked continuously. When you log into a streaming service, you authenticate once, but the service keeps checking your authorization status for each piece of content you try to watch.
Why Both Matter Equally
These concepts work together to create layered security. Strong authentication without proper authorization might let someone access everything once they're in. Good authorization without strong authentication might control access well, but to the wrong people. The most secure systems excel at both, creating multiple checkpoints that verify identity and continuously validate permissions.
Try thinking of other examples in your daily life where you notice this two-step process of proving who you are, then having a system determine what you can do. What are some of your favorites? I look forward to seeing what you share.