ZITADEL Administrators
Administrators are users or service accounts who have permission to manage resources within ZITADEL.
Administrator permissions can be assigned to different levels in ZITADEL:
- IAM Administrators: This is the highest level. Users with IAM Administrator roles are able to manage the whole Instance.
- Organization Administrators: Administrators at the Organization level are able to view or manage everything, according to their permissions, within the granted Organization.
- Project Administrators: In this level the user is able to manage a project.
- Project Grant Administrators: The project grant administrator manages projects granted by another organization.
The scope of the administrators is restricted based on their level. Which means that an administrator, assigned to one organization, will have access only to the resources and settings of that organization. Only the Administrators on the instance level can view resources, such as users, across all organizations.
To configure administrators in ZITADEL, go to the resource where you like to add it (e.g., Instance, Organization, Project, GrantedProject). In the right part of the management console you can find ADMINISTRATORS in the details part. Here you have a list of the current administrators and can add a new one.
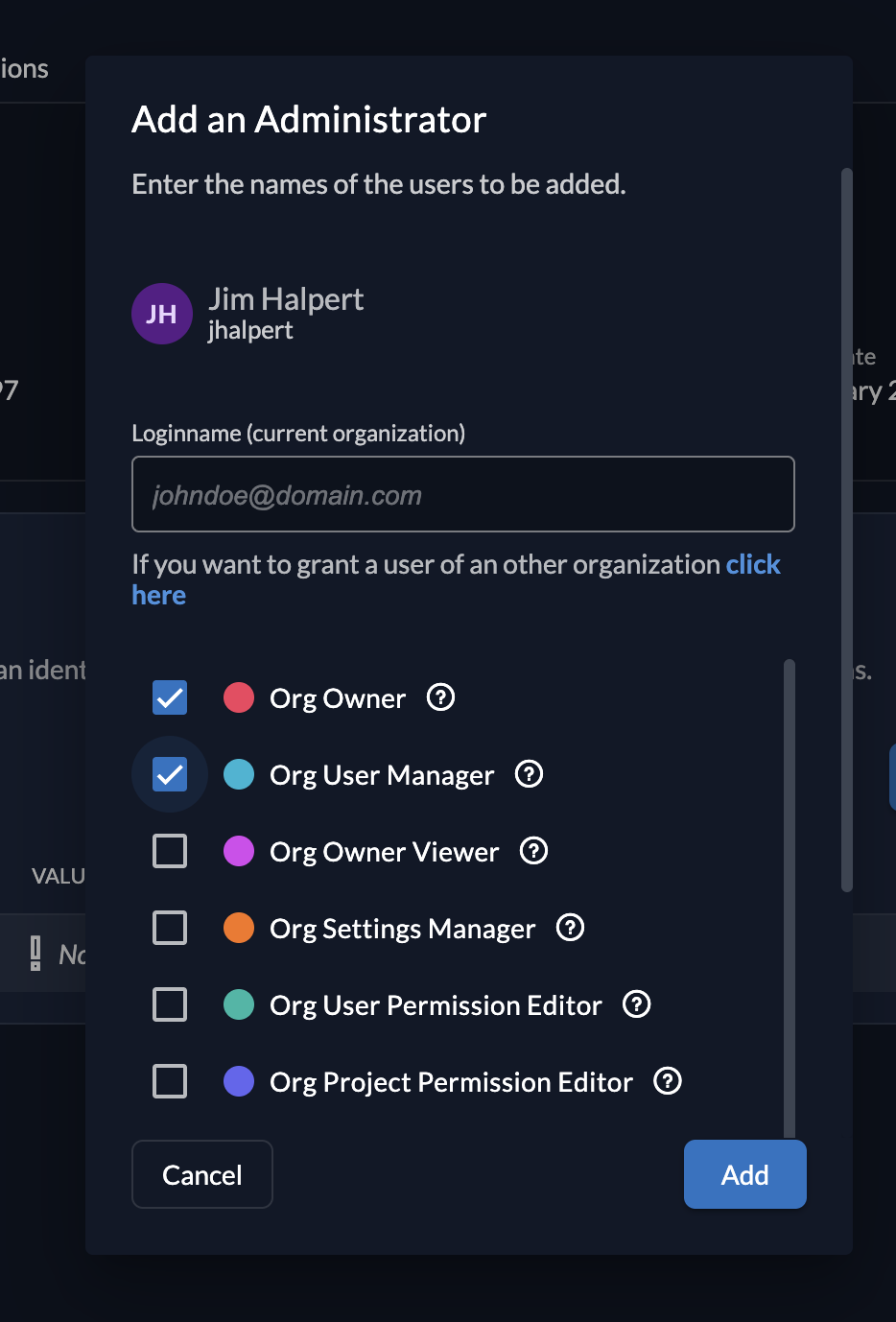
When adding a new administrator, you can select multiple roles, some of which are only allowed to read data. This can be especially useful if you add service account for one of your projects where you only need read access.
By default, you will only search for users within the selected organization. If you like to give a role to a user outside the organization, you need to switch to the global search and type the exact loginname of the users. This will prevent users from guessing users from other organizations.
Roles
| Name | Role | Description |
|---|---|---|
| Instance Owner | IAM_OWNER | Manage the Instance, manage all organizations with their content |
| Instance Owner Viewer | IAM_OWNER_VIEWER | View the Instance and view all organizations with their content |
| Instance Org Manager | IAM_ORG_MANAGER | Manage all organizations including their policies, projects and users |
| Instance User Manager | IAM_USER_MANAGER | Manage all users and their authorizations over all organizations |
| Instance Admin Impersonator | IAM_ADMIN_IMPERSONATOR | Allow impersonation of admin and end users from all organizations |
| Instance Impersonator | IAM_END_USER_IMPERSONATOR | Allow impersonation of end users from all organizations |
| Instance Login Client | IAM_LOGIN_CLIENT | Get all permissions needed to implement your own Login UI. |
| Org Owner | ORG_OWNER | Manage everything within an organization |
| Org Owner Viewer | ORG_OWNER_VIEWER | View everything within an organization |
| Org User Manager | ORG_USER_MANAGER | Manage users and their authorizations within an organization |
| Org User Permission Editor | ORG_USER_PERMISSION_EDITOR | Manage user grants and view everything needed for this |
| Org Project Permission Editor | ORG_PROJECT_PERMISSION_EDITOR | Grant Projects to other organizations and view everything needed for this |
| Org Project Creator | ORG_PROJECT_CREATOR | This role is used for users in the global organization. They are allowed to create projects and manage them. |
| Org Admin Impersonator | ORG_ADMIN_IMPERSONATOR | Allow impersonation of admin and end users from the organization |
| Org Impersonator | ORG_END_USER_IMPERSONATOR | Allow impersonation of end users from the organization |
| Project Owner | PROJECT_OWNER | Manage everything within a project. This includes to grant users for the project. |
| Project Owner Viewer | PROJECT_OWNER_VIEWER | View everything within a project. |
| Project Owner Global | PROJECT_OWNER_GLOBAL | Same as PROJECT_OWNER, but in the global organization. |
| Project Owner Viewer Global | PROJECT_OWNER_VIEWER_GLOBAL | Same as PROJECT_OWNER_VIEWER, but in the global organization. |
| Project Grant Owner | PROJECT_GRANT_OWNER | Same as PROJECT_OWNER but for a granted project. |
Configure roles
If you run a self-hosted ZITADEL instance, you can define your custom roles by overwriting the defaults.yaml In the InternalAuthZ section you will find all the roles and which permissions they have.
Example:
InternalAuthZ:
RolePermissionMappings:
- Role: "IAM_OWNER"
Permissions:
- "iam.read"
- "iam.write"Administrator Permission Matrix
This table is generated dynamically from our settings file.
| Permission | IAM ADMIN IMPERSONATOR | IAM END USER IMPERSONATOR | IAM LOGIN CLIENT | IAM ORG MANAGER | IAM OWNER | IAM OWNER VIEWER | IAM USER MANAGER | ORG ADMIN IMPERSONATOR | ORG END USER IMPERSONATOR | ORG OWNER | ORG OWNER VIEWER | ORG PROJECT CREATOR | ORG PROJECT PERMISSION EDITOR | ORG SETTINGS MANAGER | ORG USER MANAGER | ORG USER PERMISSION EDITOR | ORG USER SELF MANAGER | PROJECT GRANT OWNER | PROJECT GRANT OWNER VIEWER | PROJECT OWNER | PROJECT OWNER GLOBAL | PROJECT OWNER VIEWER | PROJECT OWNER VIEWER GLOBAL | SELF MANAGEMENT GLOBAL | SYSTEM OWNER | SYSTEM OWNER VIEWER |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| action.execution.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| action.execution.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| action.target.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| action.target.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| action.target.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| admin.impersonation | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| events.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| group.create | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| group.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| group.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||||||
| group.user.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| group.user.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||||||
| group.user.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| group.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| iam.action.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.action.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| iam.action.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.debug.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| iam.debug.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.feature.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.feature.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| iam.feature.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.flow.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.flow.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| iam.flow.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.idp.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.idp.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| iam.idp.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.member.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.member.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| iam.member.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| iam.policy.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.policy.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| iam.policy.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| iam.restrictions.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| iam.restrictions.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.web_key.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.web_key.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| iam.web_key.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| iam.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| impersonation | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| milestones.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| org.action.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| org.action.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| org.action.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| org.create | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| org.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| org.feature.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| org.feature.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||||
| org.feature.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| org.flow.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| org.flow.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| org.flow.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| org.global.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||||
| org.idp.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| org.idp.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||||
| org.idp.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| org.member.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| org.member.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||||||||
| org.member.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| org.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||||||||
| org.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| policy.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| policy.read | No | No | No | No | No | No | No | |||||||||||||||||||
| policy.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| project.app.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| project.app.read | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||||||||||
| project.app.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| project.create | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| project.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| project.grant.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||||
| project.grant.member.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| project.grant.member.read | No | No | No | No | No | No | No | No | No | No | No | No | ||||||||||||||
| project.grant.member.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||||
| project.grant.read | No | No | No | No | No | No | No | No | No | No | No | No | ||||||||||||||
| project.grant.user.grant.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| project.grant.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||||
| project.member.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| project.member.read | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||||||||||
| project.member.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||||
| project.read | No | No | No | No | No | No | No | No | No | No | ||||||||||||||||
| project.read:self | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| project.role.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| project.role.read | No | No | No | No | No | No | No | No | No | No | No | No | ||||||||||||||
| project.role.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| project.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| session.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||||
| session.link | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| session.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||||
| session.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| system.debug.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.debug.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| system.debug.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.domain.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.domain.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| system.domain.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.feature.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.feature.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| system.feature.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.iam.member.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| system.instance.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.instance.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| system.instance.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.limits.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.limits.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.quota.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| system.quota.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| user.credential.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||
| user.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| user.feature.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| user.feature.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||||||
| user.feature.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| user.global.read | No | No | No | No | No | No | No | No | No | No | ||||||||||||||||
| user.grant.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||||||||
| user.grant.read | No | No | No | No | No | No | No | No | No | No | ||||||||||||||||
| user.grant.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||||||||
| user.membership.read | No | No | No | No | No | No | No | No | No | No | No | No | ||||||||||||||
| user.passkey.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||||
| user.read | No | No | No | No | No | No | No | No | No | No | No | No | ||||||||||||||
| user.self.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||
| user.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | ||||||
| userschema.delete | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| userschema.read | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |||
| userschema.write | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No |
Was this page helpful?